Latest news about Bitcoin and all cryptocurrencies. Your daily crypto news habit.
Proof-of-Work consensus operates on the premise that attacking the network is too expensive and it’s more profitable to work with other nodes towards the same ends. But a recent slew of 51% attacks suggests we might need to rethink the place of PoW in the crypto ecosystem.
There have been several 51% attacks on proof-of-work blockchains in recent weeks, including Verge and GameCredits, but the most noteworthy has been the attack that saw hackers make off with up to $18 million after a successful double spend was executed on the Bitcoin Gold network.
Proof-of-work cryptocurrencies are maintained by networks of computers carrying out simple but repetitive and computationally-expensive tasks (‘work’). The problem is that if one node possesses more computational power than the rest of the network put together, it can rewrite the blockchain record — allowing the attacker to profit in the process: ‘The attacker made deposits at cryptocurrency exchanges, traded the coins for BTC or another coin, and then withdrew the funds. Next, the attacker used their dominant computing power to force the rest of the network to accept falsified blocks that reversed their initial deposits and caused these funds to vanish from exchange-controlled wallets.’
The Nakamoto Consensus — the proof-of-work system that enables bitcoin to serve as a peer-to-peer value transfer network — was absolutely ground-breaking when it was first proposed and implemented in 2008 and 2009. Bitcoin has never been compromised: hashrate, or the total computational power of all the computers in the network, is so high that it would be astronomically expensive to attempt a 51% attack. In the years since the Bitcoin protocol was released, many other proof-of-work coins have also been launched. None have the hashrate that secures Bitcoin, but many nevertheless have vast networks of computers that collectively secure them.
And herein, ironically, lies the problem. Because the strength of those networks represents a vulnerability to other, smaller networks.
Miners’ sunk costs mean opportunities for hackers
Bitcoin hashrate is vast, over 30 million TH/s (30,000,000,000,000,000,000 H/s), and is rising constantly with greater adoption and better hardware. However, there are many, many coins with networks supported by orders of magnitude lower hashrate. That’s also the case with other blockchains that use different consensus algorithms. Bitcoin Gold, for example, uses Equihash — and so do several other large coins. That made BTG a small and vulnerable fish in a big pool.
Proof-of-work is successful in securing a network when the costs outweigh the benefits. But having a large network means there are a lot of miners with sunk costs: people who have already bought hardware in order to profit from block rewards, but which can just as easily be deployed elsewhere if it looks more profitable. That’s what happened with Bitcoin Gold. The attacker simply needed to switch their hashrate from one blockchain, where they were mining honestly, to a blockchain that was weak enough to attack for profit.
The series of 51% attacks and double-spends we’ve recently seen will therefore likely continue and accelerate. There is, quite simply, no reason for them not to. The hashrate is there, and if it is more profitable to mine dishonestly than honestly, that’s exactly what miners will do. In some cases — as has already happened with very low-hashrate chains — miners will attack the network just for fun.
Solutions
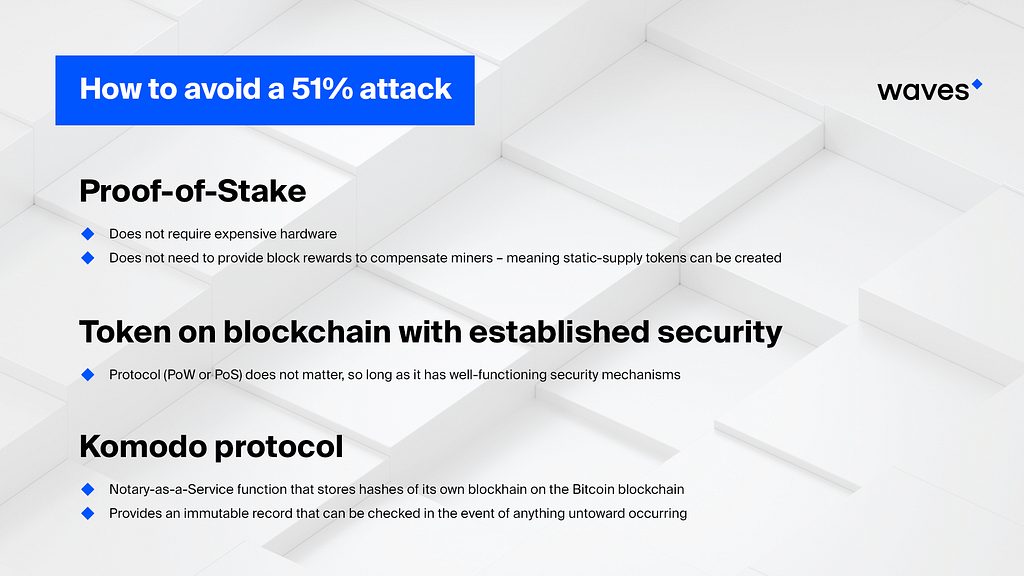
There are a number of solutions to this problem, which could otherwise threaten every new blockchain that uses the same PoW algorithm as an existing, large network.
The first is Proof-of-Stake (PoS), which already has advantages of energy efficiency and throughput — as demonstrated by Waves-NG, which supports many hundreds of transactions per second. Proof-of-stake is already growing in popularity because it does not require expensive hardware, and therefore does not need to provide block rewards to compensate miners — meaning static-supply tokens can be created (which is what most ICO investors want).
A second option is launching tokens on a blockchain with established security, whether that is PoS or PoW. Ethereum (currently PoW) has proven popular for this reason, as well as its large developer and investor community. Waves, similarly, is a popular option for launching tokens without the overhead of maintaining a network.
The third option, taken by GameCredits after the network was attacked, is to ‘notarise’ the blockchain periodically on a stronger blockchain — in this instance. This has been carried out via the Komodo protocol. Komodo operates a Notary-as-a-Service function that stores hashes of its own blockhain on the Bitcoin blockchain, providing an immutable record that can be checked in the event of anything untoward occurring.
Thus one unintended and welcome consequence of these attacks will likely be the greater interoperability of different blockchains, as more projects launch tokens on established chains and more networks use each other to validate the integrity of their own blockchains.
51% attacks and the future of PoW was originally published in Hacker Noon on Medium, where people are continuing the conversation by highlighting and responding to this story.
Disclaimer
The views and opinions expressed in this article are solely those of the authors and do not reflect the views of Bitcoin Insider. Every investment and trading move involves risk - this is especially true for cryptocurrencies given their volatility. We strongly advise our readers to conduct their own research when making a decision.