Latest news about Bitcoin and all cryptocurrencies. Your daily crypto news habit.

The place of data safety in business viability and reflects on how to enable security in digital product — discusses by me, Igor Pyatnytskyy, VP, Business Development at Nullgravity.
The digital transformation gave birth to a new business philosophy. The individualistic stance was changed to ecosystem-led business models — the aggregated environments of connectivity, collaborative approach, integration and new tier of interaction between stakeholders. The rapidly dynamic digital landscape demands businesses to create and capture value by establishing dynamic relationships between actors, coordinated via platforms. With the expansion of these networks, the cybersecurity surface, which is prone to attacks, also grows.
Businesses leverage data for the sake of innovativeness, competitiveness, scaling and entering new markets. As soon as data is the lifeblood of digitalization, ensuring its security is paramount for the enterprise. That is the reason why CISOs are no longer behind-the-scenes dwellers, but are fully-fledged members of C-suite. The magnitude of the cybercrime market, and the vectors being used for data breaches, put pressure on digital partners to be proactive and weave safety into their products from the start.
Cybersec is about the ecosystem, not a company
Interconnectedness and collaboration as major traits of an ecosystem-led environment expose businesses to increased types of risks. However, the same traits provide potential solutions. The growing interdependence between ecosystem actors requires ensuring data security as the foundation of these relationships. In view of this, cybersecurity is no longer a matter of concern for an individual enterprise. A holistic approach to data security is exactly what business resilience means today.
It is a security-driven mindset which is a success determiner for a company. The roots of the problem — why data security is underestimated, underinvested or unattended at all — can be found in a misperception of security. It is not a destination or reaction to attack, but rather, a journey, where an organization explores its capabilities, blind spots and enhances security across the levels.
Risk management in a digitalized era
Customers across industries are used to personalized and instantaneous services, and their expectations are ever-changing. New digital channels provide exposure of digital assets. Together with regulatory constraints and increased competitiveness, the trends create the necessity to digitize risk management. In other words, at times when customer journeys and operations are digitized, risk management cannot remain analog.
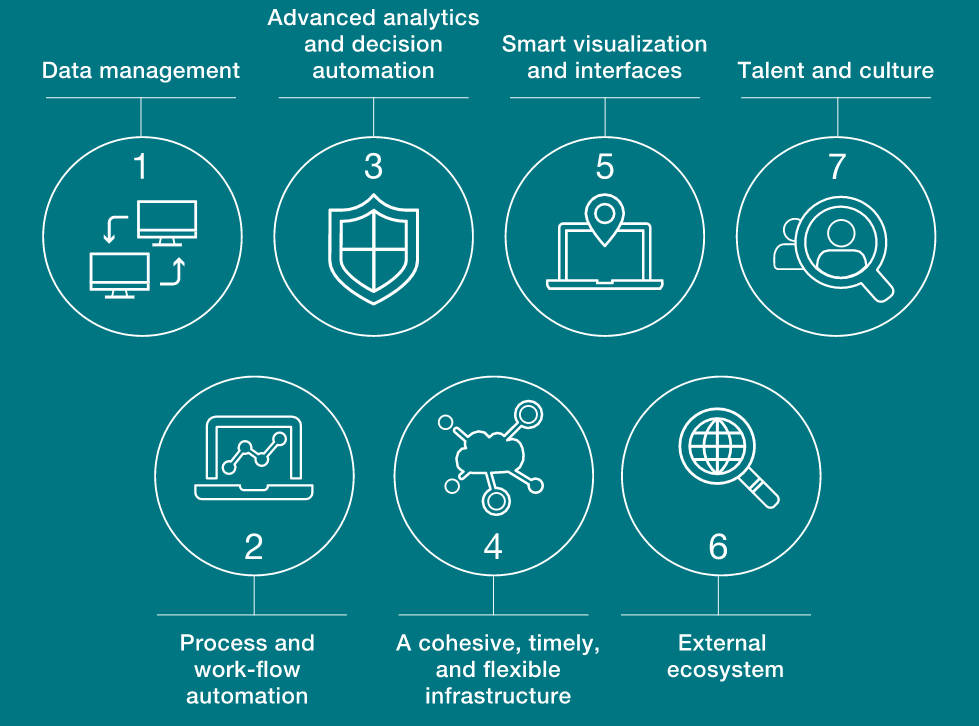
In the context of digital finance, risk management efforts imply three tiers of defense: front line staff working with customers, chief compliance officers and risk officers responsible for oversight, and last but not least — corporate audit. The design of the new digital systems relies on the integration of the appropriate risk controls across areas. Digitizing risk means extracting and managing insights from rich datasets. The flexibility of risk data architecture means embedding risk solutions elsewhere: in applications, corporate platforms, as well as strategic planning.
Source: McKinskey
As can be seen from the graph, digital risk management is a complex and multi-faceted system. These seven pillars of digital risk do not necessarily demand excellent in each. It is essential for the entity to prioritize the ones that are crucial and unique for each specific strategy. Successful risk digitization involves creating digital risk vision — how the role of risk will evolve with the passage of time. Digitization opportunities must be assessed — how digital tools will be applied to certain activities. Ultimately, these opportunities must be aligned with strategic objectives. Analytical approaches should be tested systematically, as ensuring their safety is an ongoing process.
Data safety as the fuel for business
The security status of digital product is linked with a competitive edge of the entire business. Users provide sensitive data to get personalized and superior service in return. When security is manifested as one of the core corporate values, the business is credible, thus, it can be trusted. Since people are not just buying products/services, but are building relationships, trust is the most valuable business asset — it is intangible and can make or break the company. Reputational damage from a data breach is immense, as negative experiences spread via word of mouth and social media like wildfire. Trusted security posture drives customer retention and loyalty.
Businesses with a strong security framework are more confident in themselves when it comes to market expansion. Scaling up requires a business to be agile and flexible, to be able to withstand stiff competition and implement new products. Having data security as part of corporate DNA, a company can smoothly move to new areas of development.
Being proactive means ditching ‘preventing’ in favor of ‘detecting and responding’. Traditionally, huge budgets were poured into preventive controls which have proven to be ineffective. Having a response program in place increases the company’s productivity by loosening up restrictive posture and focusing on innovation.
Fraud and its implications
Account takeover or ATO belongs to the most common loss cause a digital channel can suffer. A criminal executes identity theft by gaining access to financial information (personal identifiable information or PII) of a victim for gaining profit. This fraud type is related to, but differs from synthetic identity type — when the stolen user’s data is mixed with trumped-up details. The major goal of this type of fraud is to synthesize a fake identity to open a new account. ATO fraud falls into a large number of schemes and strategies.
During password database theft a criminal steals a client’s credentials from the web service in order to use them again for hacking accounts on other websites. Phishing has different forms — spear phishing, smishing, vishing (voice phishing) and whaling — and it refers to the terms ‘social engineering’, when trust is being exploited. Basically, it might look like legitimate communication with a well-established, credible entity. Banking Troijan utilizes Man-in-the-browser (MitB) scheme, altering transactions and page content and rendering browser engine. Man-in-the-middle (MiTM) attack means a criminal is placed between a user and financial entity to take over communication. Man-in-the-mobile (MitMo) vector implies a malware is used for stealing OTPs.
In the first six months of 2018, 4.5 billion customer data records were taken over, making 86% of all user data. What is more saddening, approximately 97% of customers cannot tell the difference between a real letter and phishing email (Absa). In August 2018, India-based Cosmos bank lost $13.5 million — the malware infected ATM server and retrieved users’ data. At the end of 2018, Canada’s Cost Capital Savings fell victim to cybercriminals who conducted phishing attacks. Reportedly, 140 clients lost $3000 to $6000 on average.
But what is the real damage an attack can cause to a financial entity? In the context of risks, financial loss can actually kick you out of business — the remuneration cost is considerable. Besides financial considerations, brand reputation and trust are extremely hard to revitalize after a cyber crime. Bank clients are overwhelmed by the fear that their finances are unsafe. Reputation risk is vital, simply because the balancе between tangible and intangible assets has moved towards the latter. They are hard to manage, handle and compensate.
Datasec in digital finance
Banks belong to those entities which are trusted by clients the most in terms of ensuring personal data safety — leaving behind Apple, Amazon and PayPal. Protecting the reputation of financial service providers means finding the perfect balance between staying innovative and providing the highest tier possible of data security. And of course, this balance cannot but influence each phase of development and testing stages. In practice, software developers are often somewhat separated from the business — the product security and compliance are checked in the end. This is the case when architectural issues are sure to arise, questioning the business scalability.
Digital finance businesses that are engaged in transmitting, or storing the sensitive data of their clients are compliant with Payment Card Industry Data Security Standard or PCI DSS. The set of procedures and policies aimed at transaction security revolves around six key areas: transaction networks security, cardholder data storage protection, vulnerability management, access restriction and control, constant monitoring and testing, and compliance with formal infosec policies.
According to Open Web Application Security Project (OWASP), banking software contains risk areas known as attack surface. It breaks down into the following aspects: the paths amount for commands and data into/out of the app; codes ensuring protection of these paths; valuable data used in app and code that protects this data. OWASP developed checklist for mobile products providing comprehensive assessment. A traditional (manual) approach to testing can and will become a bottleneck for a business. Testing automation allows for pro-activity and filling the code gaps in the process of delivery.
When working on digital product in finance, the distribution of data security across the development stage is vital. App architecture waltzes around security and testing strategies, while a devoted compliance team constantly keeps an eye on the process and works with devops synergetically. Software development lifecycle or SDLC is the spine of secure app: the strategy ensures data security is embedded within the product and it is an ongoing process — maintained and enhanced. Security is the core of the business; it creates a healthy ecosystem when it is pervasive. Security wins customer trust and is the main reason a company is chosen out of the crowd.
Data security through the prism of business risks was originally published in HackerNoon.com on Medium, where people are continuing the conversation by highlighting and responding to this story.
Disclaimer
The views and opinions expressed in this article are solely those of the authors and do not reflect the views of Bitcoin Insider. Every investment and trading move involves risk - this is especially true for cryptocurrencies given their volatility. We strongly advise our readers to conduct their own research when making a decision.