Latest news about Bitcoin and all cryptocurrencies. Your daily crypto news habit.
 caption : https://www.thesslstore.com/blog/difference-sha-1-sha-2-sha-256-hash-algorithms/
caption : https://www.thesslstore.com/blog/difference-sha-1-sha-2-sha-256-hash-algorithms/
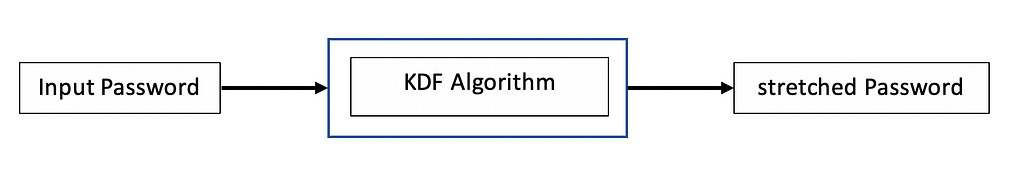
A Key Derivation function also called password stretching is a major part in a cryptographic application such as blockchain, anonymous p2p application, e.t.c and its goal is to take a password or key then generate a cryptographic ally strong and hardened key based on the number of bytes selected in the configuration.
Password are not the most secure pattern to use directly in an encryption system, KDF algorithms are usually used to create more random with longer key from an input password.
There are different KDF algorithm, Bcrypt for example will not return same output for then same given input. which means that it is not possible to generate same key from a given password using Bcrypt. Others will always returns the same result every time for a given input which in turns means that it is possible to generate same key from a given password.
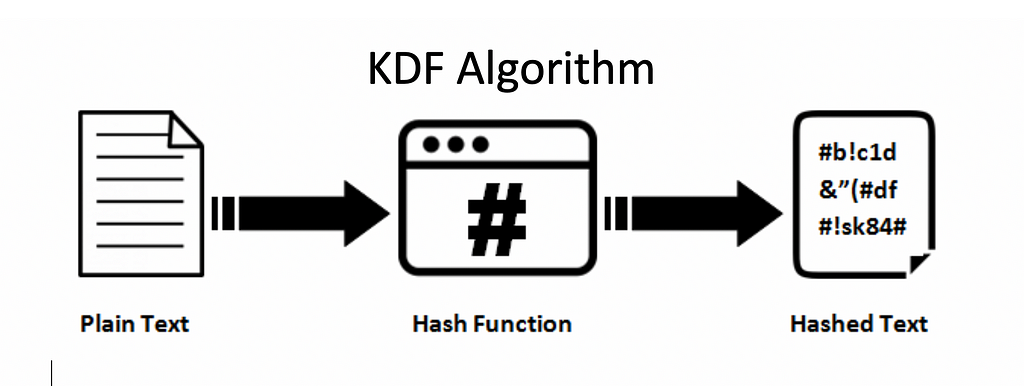
KDF algorithm are based on cryptographic hash function such as SHA-256, BLAKE-2B or Block ciphers used in AES encryption and they make use of the concepts of salt and pepper.
KDF Algorithm can be implemented in almost all programming language but in this post, I will be making use of the GoLang programming language.
we will use the pkdf package from the GoLang to generate our key and the link of the package is https://godoc.org/golang.org/x/crypto/pbkdf2
Below is the codebase for the implementation of our KDF algorithm.
The code is self explanatory based on the fact that it was well commented, But I will explain more about about few things in the implementation.
In Line 3 –10, we imported the required packages to be used in our application.Line 17 gets the user’s password in byte from the terminal in a masked format.Line 25 creates a salt in byte to be used in out program. This can be any random salt chosen by the user.Line 28 prints out the original password entered by the user.Line 32–34 compute the sha-256 hash of the imputed password and print it out on the terminal.Line 43 gets the derived key based on the input parameter.
func Key(password, salt []byte, iter, keyLen int, h func() hash.Hash) []byte
The Key function provided by the package allows us to customize the level of hardening of out input key. below are the parameter provided for us to change.
Password : This the input password to be be stretched, type must be byte.Salt : Salt is the extra layer added to the input password to make it more hardened. Type must be in byteiter : Iteration is the number of times it iterated while computing the hash of the derived key. Type must be IntKeyLen : This is the length of the proposed key to be returned. Type must be Int.h : This is the hash function to used while generating the keyWhich then returns an output containing the derived password.
Line 46 prints out the derived Key, which will be a very long key, so we need to bring it down to 32 bytes by passing it into a SHA-256 hash function which was done in line 49.Finally, we printed out the value of the hashed of the derived key.
Running the application by executing go run main.go produce the below outputs.
1.) Original Password :-> mySecurePassword
2.) Hashed Password :-> b6573a02de91d76cc442a6f42aa749c6eee0982c148bb7e9116ee44f93e6807a
3.) KDF Key :-> cdf347254e0fb199015a2721110c0a1b1bfc4f66f718a712930173f93290ed783e08e5655c57fd608da39269a10708fbe191b1141c6ea9d97d02f6bfbbd90580a3aed101a627e8e96d5cb5c51e24dbe1d5e2dca531c9f658de77080352a0394bb48af8636b840358314bfea2c0eb6a411ea36212bd13bd552a29be78e59fab17
4.) Hashed Derived Key :-> e6e562be28fc935a2ea2e57f21b018237098aeab64c2621d11627be4e9dfe601
You may be thinking that the second and fourth answers produced the same length even though the length. You are right and the reason is that Hash functions always return a fix length size irrespective of the size of the input.
Another question that you may want to ask is that why cant we just use an hash function for key stretching if they produce some sort of randomness and also key stretching. The answer to that is that it is easier to brute force the result of an hash function while brute forcing a KDF algorithm is computational expensive based.
Feel free to download the codebase from the link below and extends it to suit your need.
Thanks for your read!
Do support and show some love (Claps)
princesegzy01/kdf-implementation
Password Stretching using Key Derivation Function(KDF) was originally published in Hacker Noon on Medium, where people are continuing the conversation by highlighting and responding to this story.
Disclaimer
The views and opinions expressed in this article are solely those of the authors and do not reflect the views of Bitcoin Insider. Every investment and trading move involves risk - this is especially true for cryptocurrencies given their volatility. We strongly advise our readers to conduct their own research when making a decision.