Latest news about Bitcoin and all cryptocurrencies. Your daily crypto news habit.
Don’t Be a Menace to ROKKEX: Example of An Impersonation Attack
Back in the 1980s, the internet was a peaceful place where people were friendly and quaint. The whole atmosphere reminded Gene Kelly singing in the rain: the speed and connection made you uncomfortable, but anyway you were happy to have it as it was.
Nothing seemed to pose a danger; email servers were configured as open relays, meaning they allowed anyone connecting to send emails to anywhere. This practice was abandoned years later when cybercriminals began exploiting open relays.
Today, almost 30 years later, there is still no univocal solution to counter spammers, and so the businesses are left vulnerable to social engineering, and impersonation in particular.
Social Engineering and Impersonation
To begin with, let’s recall what is social engineering and which of its methods we’ll talk about today.
Social engineering is a science of manipulative psychological techniques and methods to trick users. It has many faces, such as phishing, spoofing, impersonation, and others.
Impersonation as such is an act of impersonating a trusted individual. Adams, in his Encyclopedia of Cryptography and Security, described impersonation attack like the one when a criminal successfully assumes the identity of one of the legitimate parties in a system or a communications protocol.
Needless to say that such attacks are generally targeted at corporate employees to receive large sums of money or sensitive information.
The Structure of Impersonation Attack
As every attack, impersonation is usually planned and structured. It doesn’t mean that a criminal nurtures a plan for as long as Le Comte de Monte-Cristo did but anyway the more money is at stake, the more sophisticated the plan is (let’s not forget that the recent Binance hack was possible thanks to specific social engineering techniques). Most of the social engineering attacks are executed in a further way:
- Set a Goal
Usually, the attacker intends to make a victim perform actions that will violate the borders of personal cybersecurity, for instance:
- make money transfers to pay fake invoices;
- share sensitive data related to a company or its clients;
- click on hyperlinks to take over the computer and/or steal user credentials;
- open a file attachment to install ransomware and encrypt files on the company’s internal network and hold them for a ransom.
2. Find A Target
Be alert, social media profiles such as Facebook, LinkedIn, Instagram, or Twitter are the most accessible mediums to collect information about a future victim as they’re the most popular ones. The attackers easily fetch your name, email address, school, friends, job title, job duties, location, etc. Social engineering attacks don’t require profound technical skills, as all the information needed is freely accessible online.
3. Build Credibility
After examining the target, an attacker now has to wear a mask of whom they are going to impersonate, resorting to social engineering research again. It can be the target’s boss, a company selling the services, or an influencer. A perfect “mask” is found during the research; a vulnerable place is identified and pointed.
4. Execute an Attack
The final step is to launch an impersonation attack. The scammer starts communication with the victim, proving the credibility and building trust step by step. How is the attack performed exactly? See below!
Example of Impersonation Attack
Being a new company in the market means that many people offer you their marketing services. Everyone promises to give the best exposure and assures that their methods are innovative and efficient. However, there is one more group of people — scammers — who want to make a profit without giving anything back.
At least several dozens of scammers have contacted ROKKEX for the past few months, and today we want to tell you how to identify an impersonator and not let your employees spend money in vain.
Let’s start from the basics. CoinTelegraph is a widely-known media outlet in the cryptocurrency world. Unique and catchy pictures, up-to-date news, and quality analytics have made the platform a “Forbes” in the cryptocurrency. A review on a new blockchain project costs at least 1 BTC but will bring much value and exposure. CoinTelegraph is one of the first outlets that come to mind when advertising a project.
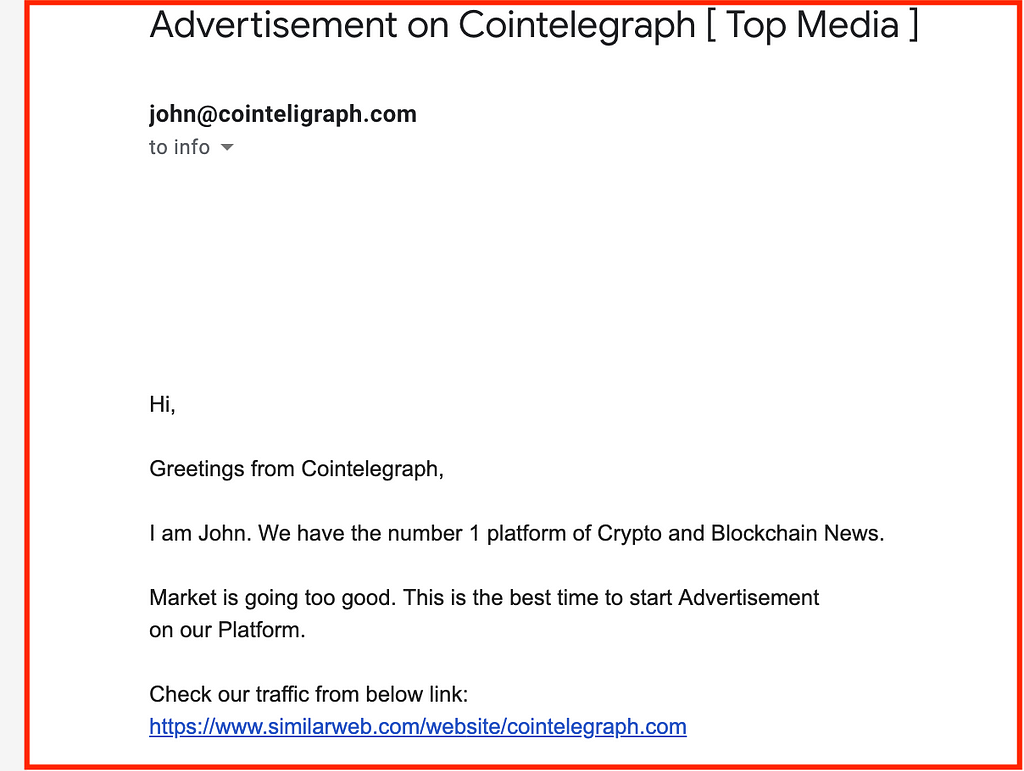
That’s why it’s so juicy for a criminal to pretend that they’re CoinTelegraph sales forces. Check the email we got this morning:
A savvy specialist will notice that the email is informal and unprofessional. Yes, in the cryptocurrency world, we’re slangy but not enough to sell the service with the expression “Market is going too good.” Besides, the link.
Seriously? A person working in Tier 1 media outlet should provide you with insights from GA at least and not make you DYOR (do your own research). Okay, these are minor details, and they don’t usually point out to scammers (some companies do have a poor email communication).
There is another significant hint that makes us no longer doubt that a scammer is targeting us.
Compare:
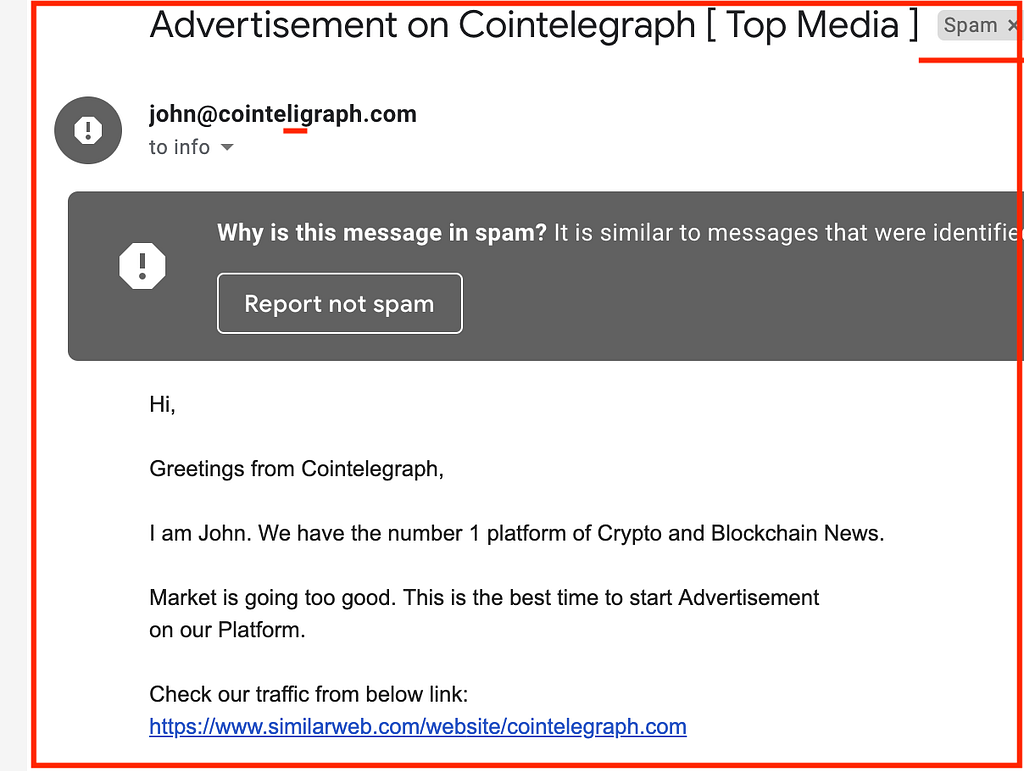
Telegraph VS Teligraph. One tiny letter makes a huge difference.
This email was immediately identified by Gmail as spam and has a grey banner on it, so you’re less likely to ever fall victim of such an amateur scammer.
Nevertheless, remember: always check the sender’s email; it shouldn’t have typos, contractions, numbers, or anything that makes it differ from the original domain name you’re dealing with.
This is how it looked like in ROKKEX mailbox:
Impersonation attacks are known to be executed widely in emails; however, when instant messengers and social media started gaining traction, cybercriminals widened their scope of activity.
Today, you can meet an impersonator everywhere in the digital world: Facebook, Instagram, Viber, WeChat, etc. We met one in Telegram who pretended to be Doug Polk Crypto. One step at a time!
Doug Polk Crypto is a YouTube influencer who created his cryptocurrency channel comparatively recently (slightly more than a year ago) before he had been making videos about poker.
The new channel focuses mostly on denouncing YouTubers who are either promoting Ponzi Schemes or making videos just to maintain viewership. The smaller part of his content is devoted to his informed advice on which coins to buy and sell.
At this time it’s unlikely that Doug Polk Crypto will make a promotional video about a new cryptocurrency project, as that’d mean that he’s changing the focus and becoming one among numerous crypto bloggers; now he’s respected for uncovering Ponzi schemes and shaming unfair players. Nevertheless, our second scammer didn’t have that in mind when contacting us.
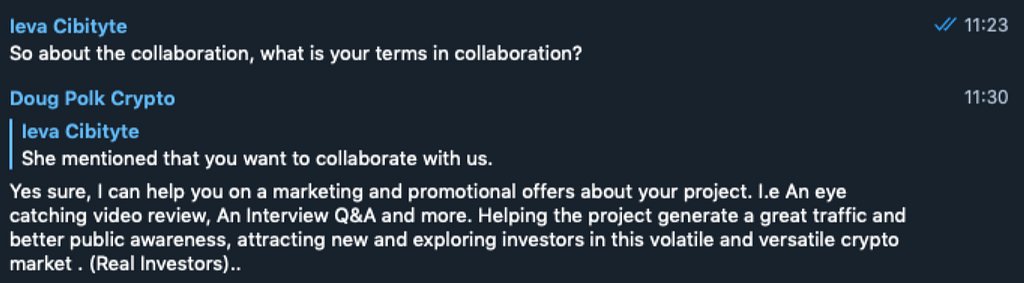
So, on May 28 somebody named @Dougcrypto_02 wrote Hello to ROKKEX.
*The nickname is not complete and this “02”. Who are you? A devoted fan? Or maybe a scammer?
We didn’t have a second thought and jumped into the game. It promised to be fun 😈 (spoiler: and it did!).
The guy immediately offered us “an eye-catching video review and Q&A interview.” Doug Polk Crypto has never done that before in his YouTube channel, and we were honored to be the first. Well, that’s flattering! Thank you, scammer.
Here comes my favorite part. For the review, a fake Doug Polk Crypto charged 7 ETH ($1 889,419 on May 28). Our marketing specialist is an efficient person (and with a good sense of humor), she decided to continue the conversation and bargain a bit.
She told we could pay only $300. You know what? He agreed! Without thinking twice, he agreed to make 2 videos for $600 (he was definitely passionately in love with ROKKEX; unfortunately, scammer, that’s not mutual).
A respected and famous YouTuber decreased the price for a review by more than 6 times! Why? , the scam didn’t require many resources (if any); that’s why it was better to win at least $300 rather than $0. Oh yes, we asked to pay in fiat; surprisingly, he rejected 😒.
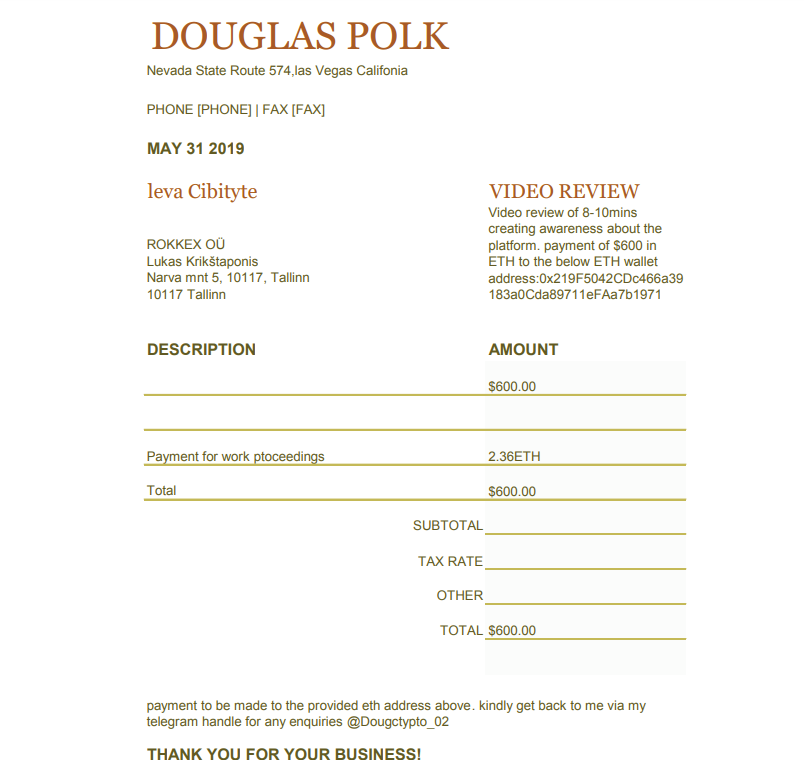
Then, we asked to give his credentials for us to prepare a service agreement. Yes, ROKKEX is law-abiding, so we’re making business according to law and regulations paying taxes and being 100% transparent not only in the cryptocurrency world. He sent us an invoice.
Check it:
Let’s agree, not everyone can prepare a decent invoice, but this is the real masterpiece of haste and carelessness.
We decided to check the address. Get ready for it!
In the middle of Nevada desert!
At that point, 3 days later, we already got tired of him. We stopped answering the messages when a few days later, a fake Doug Polk Crypto called himself.
We heard an Indian accent asking when we were going to send the payment. In reply, we stated that no cent from ROKKEX would fund his malevolent venture. Some days later, @Dougcrypto_02 deleted his account in Telegram.
Why Are Impersonation Attacks Hard to Detect?
A major reason impersonation attack is hardly detected by users is ignorance and lack of attention to details. A tiny spelling “mistake” makes a huge difference, and seemingly a legit party appears to be an evil scammer.
Sometimes it’s hard to figure out the irregularity, especially when you have a hectic schedule at work and many distractions. However, employees should be made aware of this type of attack not to put the company at risk. Just consider the numbers:
- In 2017, the U.S. Federal Bureau of Investigation (FBI) warned businesses about the growing threat of impersonation attacks and estimated that such attacks had caused losses of approximately $5.3 billion globally.
- According to ACCC’s Scamwatch revealed Australia alone reported over $4.7 million losses caused by impersonation attacks that year.
We gave examples of 2 different impersonation attacks: one conducted via email and the second via instant messenger — Telegram. Both were obvious scams from the very beginning; nevertheless, our cumulative experience in cybersecurity is 20 years, and we trace such scams easier than an average user, but it’s not always like that.
Cybercriminals are witty, in chase of profit they can spend a lot of efforts and resources. You can never claim that you’re 100% safe from a hack.
Preventative Measures
There is no univocal remedy against social engineering and impersonation attack in particular; however, there are measures that educate employees and make them prepare that they may be targeted.
- SOP. The SOP is an abbreviation from a standard operating procedure. It is a set of step-by-step instructions compiled by a company to help its employees carry out complex routine operations. Your company should have this kind of guide in cybersecurity to define how an employee should carry out communication or perform their duties. SOP usually saves not only hundreds of working hours but also hundreds of thousands $.
- 2FA. We do trust this measure and mention two-factor authentication almost in every our article for a reason. Adding 2FA to email where possible protects your business email from unauthorized access.
- Privacy. They say that when you have a profile in social media, you can no longer stay private. True. That’s why, as a company manager, you may implement a corporate policy of not sharing work-related information online. Remember, the more information is publicly available about your company, the easier for an attacker to find a scope for the attack.
You may also Like
Not Only You Have Access To Your Messenger
8 Ways to be Tricked when Buying Cryptocurrency on P2P Platforms
At ROKKEX, we take security extremely seriously, and our crypto exchange is built on ‘Security First’ principle. We want to share our expertise with the broader public for the world to become happy, safe, and wise :)
If you have any ideas and suggestions, contact us at
Website . LinkedIn . Facebook . Twitter . Telegram . Reddit . Instagram
Don’t Be a Menace to ROKKEX: Example of Impersonation Attack was originally published in Hacker Noon on Medium, where people are continuing the conversation by highlighting and responding to this story.
Disclaimer
The views and opinions expressed in this article are solely those of the authors and do not reflect the views of Bitcoin Insider. Every investment and trading move involves risk - this is especially true for cryptocurrencies given their volatility. We strongly advise our readers to conduct their own research when making a decision.