Latest news about Bitcoin and all cryptocurrencies. Your daily crypto news habit.

Yesterday, blockchain privacy startup Enigma announced the availability of its second testnet. Incubated in the Massachusetts Institute of Technology(MIT) Media Lab, Enigma takes a very unique angle to address privacy and scalability in blockchain applications. To accompanied the new release, I’ve updated an article I published about Enigma almost a year to date.
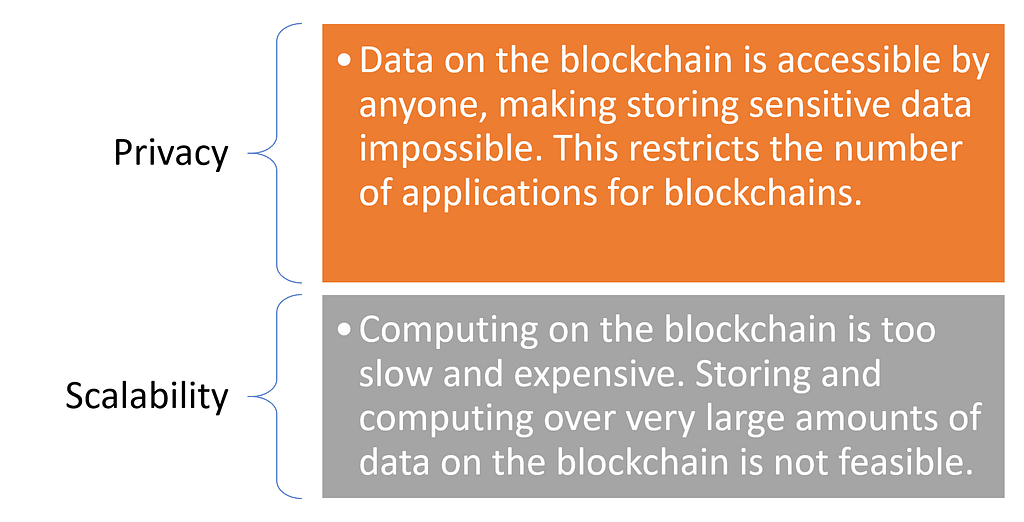
Blockchains might be the most ground-breaking technologies in several generations but its mainstream adoption remains relatively limited compared to other technology trends. The blockchain community is very aware that there are several challenges that need to be solved in order to streamline the adoption of blockchain technologies. Among those challenges, none two are more important than privacy and scalability.
There are several efforts within the blockchain community that are trying to address these issues but most of them rely on creating brand new blockchain infrastructures. A few years ago, security researchers from the Massachusetts Institute of Technology(MIT) Media Lab published a paper that outlined a different computation model that can solve those two problems for any blockchain. They called the technology Enigma presumably in honor of the German cryptographic machine used to cipher messages during World War II that play an important role in the beginning of computer industry. A few months after, the MIT team decided to venture beyond the academy a launched Enigma in order to bring privacy and scalability to any blockchain.
How Does Enigma Solves Privacy?
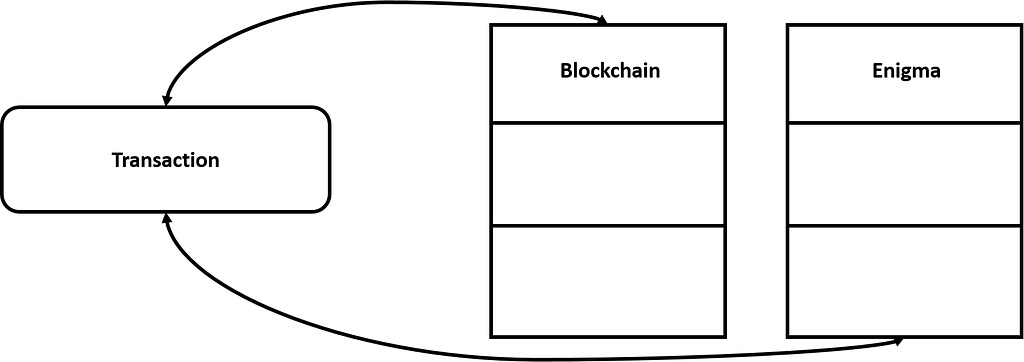
From the conceptual standpoint, Enigma is designed to connect to any blockchain and off-load private and intensive computations to an off-chain network. All transactions are facilitated by the blockchain, which enforces access-control based on digital signatures and programmable permissions.
The key idea that Enigma brings to the table is the ability to run computations on data without having access to the data itself. More specifically, the type of computations Enigma focuses on are smart contracts which, in the context of Enigma, are known as Secret Contracts given the additional level of privacy achieved with the stack. When using Enigma, Secret Contracts execute their public version on the blockchain while relying on Enigma for the private or computationally intensive parts.
The magic behind secret contracts is achieved by leveraging a novel technique known as secure multi-party computation (sMPC or MPC). In this computation model, data queries are computed in a distributed way, without a trusted third party. Data is split between different nodes, and they compute functions together without leaking information to other nodes. Specifically, no single party ever has access to data in its entirety; instead, every party has a random piece of it. MPC can be seen as a solution to the famous millionaires problem in computer science that describes two millionaires interested in knowing which one of them is richer, without revealing their actual net worth.
How Does Enigma Solves Scalability?
The key building block in the Enigma architecture that ensures scalability is the off-chain storage model. Enigma includes a decentralized off-chain distributed hash-table (or DHT) that is accessible through the adjacent blockchain. In that model, the blockchain stores references to the data but not the data themselves. Private data should be encrypted on the client-side before storage and access-control protocols are programmed into the blockchain.
From the storage standpoint, Enigma can be thought of as a collection of distributed nodes. Each node has a distinct view of shares and encrypted data so that the computation process is guaranteed to be privacy-preserving and fault tolerant.
The Enigma Architecture
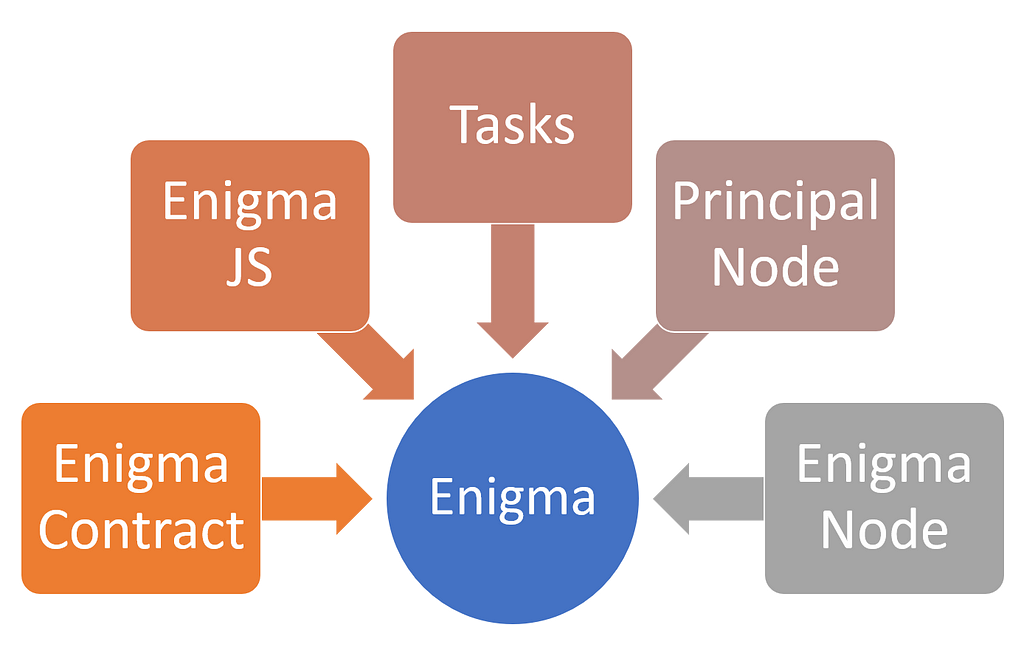
The current version of Enigma includes several key components focused on enabling privacy and scalability capabilities in decentralized applications.
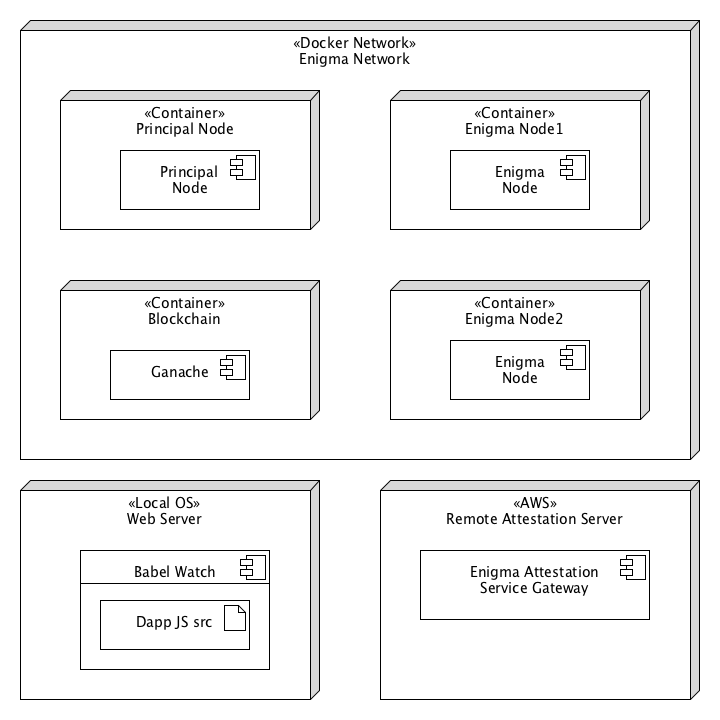
· Enigma Contract: The Enigma contract primarily contains logic to secure the network. To do this, it has a list of registered worker nodes. It receives computation task requests from Dapps, and broadcasts them to the Enigma Network.
· Enigma JS Library: The Enigma client library, Enigma-js is a javascript library that interfaces with the Enigma protocol. The API for this library describes tasks that a dApp will require to interact with Enigma, such as encryption and verification.
· Tasks: Enigma represents computations using the Task struct. Each active task item contains the computation fee paid by the Dapp user.
· Principal Node: The principal node is a temporary centralized node which performs two key functions:
1) Generate random seeds for worker selection;
2) Propagate the encryption key to other nodes joining the network.
· Enigma Node: Each Enigma node is based on two main components: Surface and Core. Surface is the untrusted component of an Enigma node which has the primary function of coordinating computation tasks between the Enigma Contract and Core. Surface is involved in worker selection and computation tasks. Core is the trusted component of the Enigma network, and executes computation tasks.
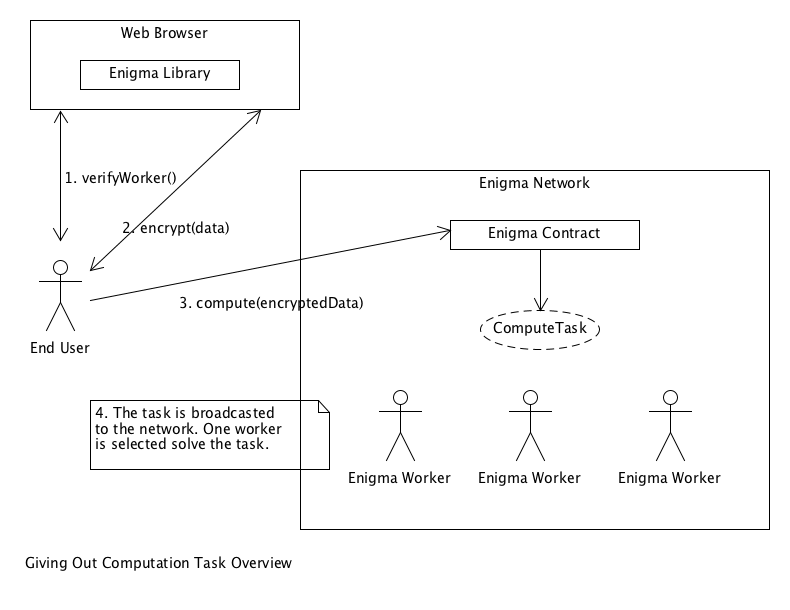
The aforementioned components in a clever architecture that ensures privacy and scalability for Ethereum smart contracts. Functionally, Enigma offloads computation tasks from an Ethereum blockchain. . Using the Enigma-JS client library, an Ethereum developer can either safely encrypt sensitive data in-memory for immediate use or storage as well as obtaining an authoritative proof that the target worker is securely running trusted hardware (SGX) prior to sending data and paying fees. The computation tasks are passed to the Enigma Contract whicn then broadcasts the task in the Enigma network. At that point, the registered workers execute a random sampling lottery algorithm to determine whether they should execute the task. The selected worker leverages its trusted hardware to unpack the task, decrypt its arguments and delegate execution to its internal EVM. After execution, a hash of the task attributes (ex: inputs, code and outputs) is signed with a private key that exists only in the trusted hardware. This data is then committed on-chain where its provenance and integrity are cryptographically verified.
The current version of Enigma runs as a self-container docker network that includes multiple containers with the different components of the platform as well as some complementary technologies.
Enigma is not the only platform trying to address the privacy and scalability challenge in blockchain applications( I’ve recently published an overview of some of the most promising technologies in the space). Regardless of being in a competitive space, Enigma provides a unique angle by ensuring compatibly with Ethereum and providing the first practical implementation of some of the most advanced research in cryptography of the last few decades.
Reimagining Privacy in Blockchains: An MIT-Incubated Solution was originally published in Hacker Noon on Medium, where people are continuing the conversation by highlighting and responding to this story.
Disclaimer
The views and opinions expressed in this article are solely those of the authors and do not reflect the views of Bitcoin Insider. Every investment and trading move involves risk - this is especially true for cryptocurrencies given their volatility. We strongly advise our readers to conduct their own research when making a decision.