Latest news about Bitcoin and all cryptocurrencies. Your daily crypto news habit.

Security is one of the capabilities that is often mentioned as one of the hallmarks of digital securities even though while it remains rather absent from the current generation of security token platforms. Security is one of those terms that is important to be ignored and too generic to be meaningful by itself so is often used out context. Today, I would like to explore some of the main security capabilities and building blocks that are relevant in the context of digital securities.
The idea that security tokens require more robust security capabilities seems incredibly intuitive but is not so obvious when we try to implement it in practice. For starters, security tokens today are constrained to the Ethereum public blockchain which doesn’t include a security layer beyond what’s provided by the trustless computation model. Even more important is the fact that some of the core building blocks of security architectures introduce some tangible frictions with the principles of public blockchains. More importantly, we need to answer the question of what security really means in the context of security tokens.
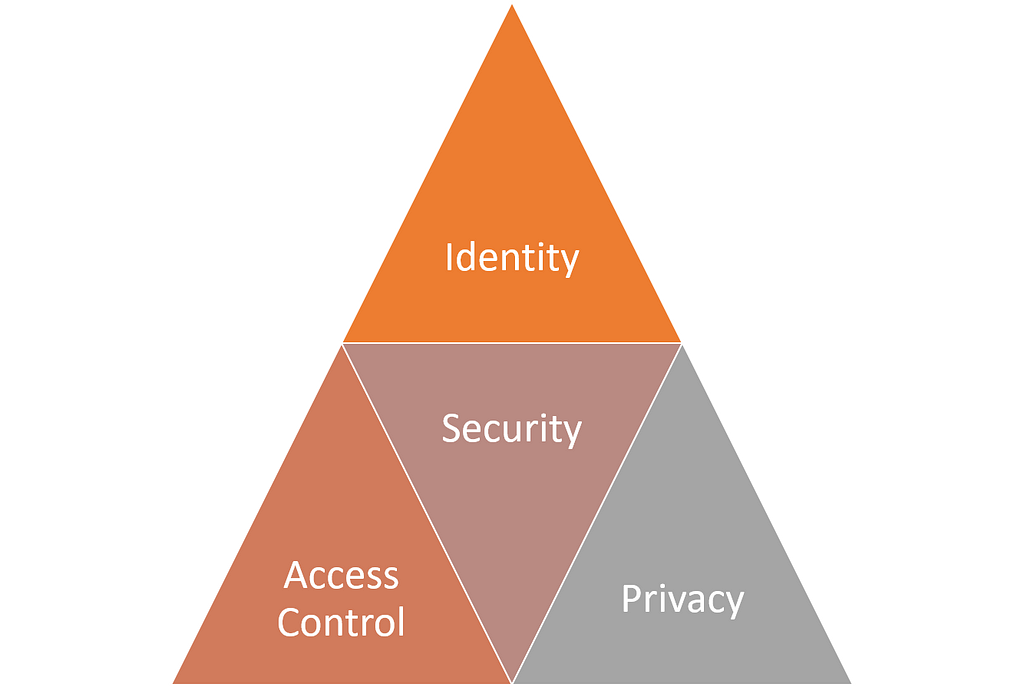
The Security Triangle in Digital Securities
The term security if often used indiscriminately and could mean different things to different people. From the perspective of security tokens, there are three relevant segments that constitute the key pillars of security architectures:
· Identity: This capability focuses on uniquely identifying the participants in a security token transactions.
· Privacy: This capability focuses on protecting the information related to specific security tokens.
· Access Control: This capabilities focuses having different levels of authorization for different participants in a security token network.
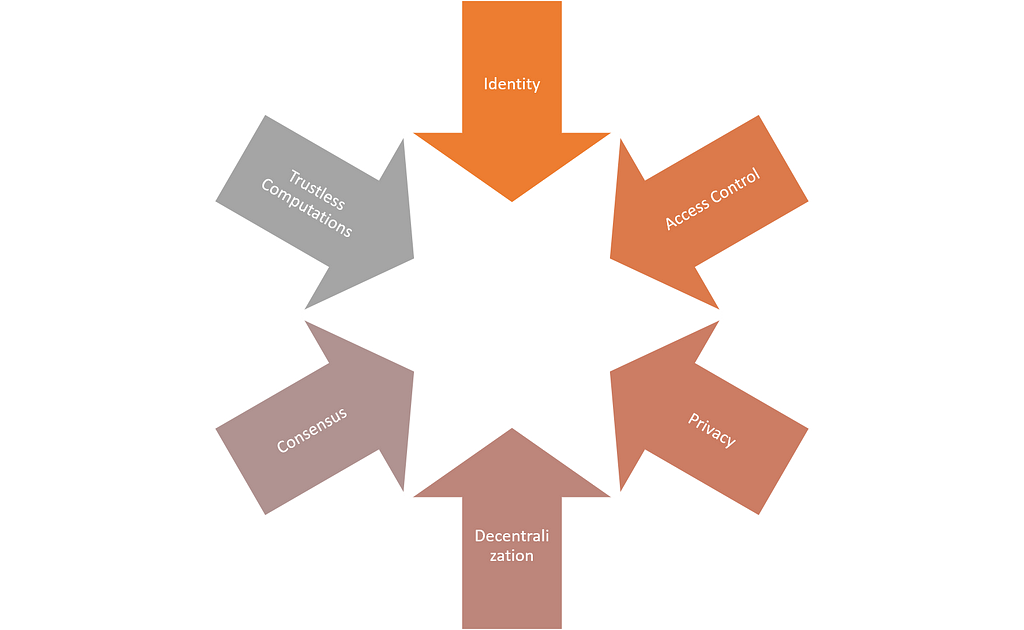
The fascinating thing is that each one of those building blocks of security is in partial contradiction with some of the core blockchain principles. Security tokens are at the center of these dilemmas which makes it even more fascinating.
· Identity vs. Decentralization: The current generation of blockchain runtimes were designed with anonymity as a first class citizen. In fact, consensus protocols are a way to assert identity via decentralized computations. Identity can act as a vector of recentralization in decentralized networks. After all, if the identity of the participants in a network is well known, how much need do we have for expensive computation-based consensus. If identity is a key component of digital securities, then is likely that security token networks might be partially centralized.
· Privacy vs. Trustless Computations: The relationship between privacy and trustless computation is not necessarily contradictory but certainly introduces some interesting friction points. In networks where information in the network is encrypted, then nodes need to accept to trust computations instead of data itself. If privacy protocols become an important component of digital securities, then the computation models of the networks will need to be adapted to those dynamics.
· Access Control vs. Consensus: Blockchains today are democratic ecosystems in which most nodes are created equal. The notion of constrained access control zones within a network directly challenges that assumption by introducing inequality between different participants in the network. In that sense, consensus protocols will need to be adapted to an ecosystem in which not all the validators in a network are able to see all transactions. Access control is an incredibly relevant component of security tokens and, consequently, it challenges the viability of existing consensus protocols for security token networks.
As security becomes an increasingly relevant elements of digital securities, the aforementioned friction points will become more and more visible. Let’s discuss how the three key pillars of security: identity, privacy and access control could be address in the next generation of security token platforms.
Identity
Decentralized identities are becoming one of the most fascinating areas of research in the blockchain ecosystem. In the current generation of security token platforms, identity is constrained to the use of “white lists” which represent a directory of investors approved to perform specific transactions. While white lists enable identity-based capabilities, they do not represent a form of identity in and out itself. As the security token space evolves, identity should evolve as a standalone protocols that are used across different security token platforms. Achieving this requires a careful balance between securities law, the characteristics of distributed ledger runtimes and decades of research in identity management protocols.
From the approaches to solve identity in blockchain solutions, the solutions pioneered by the decentralized identity foundation(DIF) seem to be the most advanced in the market. Adopted by companies like Microsoft, the DIF model to assert identity without sacrificing the core decentralization mechanics of the network. Inspired by DIF, Microsoft recently proposed a forward-thinking architecture to enable decentralized identities in blockchain runtimes. The Microsoft architecture includes the following components:
· W3C Decentralized Identifiers (DIDs): IDs users create, own, and control independently of any organization or government. DIDs are globally unique identifiers linked to Decentralized Public Key Infrastructure (DPKI) metadata composed of JSON documents that contain public key material, authentication descriptors, and service endpoints.
· Decentralized systems: DIDs are rooted in decentralized systems that provide the mechanism and features required for DPKI.
· DID User Agents: Applications that enable real people to use decentralized identities. User Agent apps aid in creating DIDs, managing data and permissions, and signing/validating DID-linked claims.
· DIF Universal Resolver: A server that utilizes a collection of DID Drivers to provide a standard means of lookup and resolution for DIDs across implementations and decentralized systems and that returns the DID Document Object (DDO) that encapsulates DPKI metadata associated with a DID.
· DIF Identity Hubs: A replicated mesh of encrypted personal datastores, composed of cloud and edge instances (like mobile phones, PCs or smart speakers), that facilitate identity data storage and identity interactions.
· DID Attestations: DID-signed attestations are based on standard formats and protocols. They enable identity owners to generate, present, and verify claims. This forms the basis of trust between users of the systems.
This type of DID based architecture can be easily adapted to security tokens as one of the main mechanisms to represent and assert identity in digital securities.
Privacy
Privacy is one of the capabilities that is desperately needed in the security token platforms. From investor onboarding compliance checkpoints such as know-your-customer(KYC) to the protecting aspects of transactions, privacy is a relevant capability of the lifecycle of digital securities. While implementing privacy capabilities in security token platforms is certainly challenging, the ecosystem can benefit from the recent advancements in privacy protocols in the blockchain ecosystem.
· CryptoNote & Ring Signatures: One of the grandfathers of blockchain privacy, CryptoNote(CryptoNight) is the protocol behind Monero. Conceptually, CryptoNote leverages a cryptographic technique known as traceable ring signatures to obfuscate messages among a group of nodes in a decentralized network. Improvements in the CryptoNote protocol have proven able to produce high degrees of anonymity while operating at scalable levels. In the context of security tokens, CryptoNote can be used enforce privacy for specific portions of a security token exchange.
· zk-SNARKS: The protocol behind ZCash, zk-Snarks is a novel form of zero-knowledge cryptography that allows one party (the prover) to prove to another (the verifier) that a statement is true, without revealing any information beyond the validity of the statement itself. Since the launch of ZCash, zk-Snarks have been adapted on different blockchain technologies such as J.P Morgan Quorum. Security tokens can incorporate zk-SNARKS as a first class block to protect data in a security token transfer.
· zk-STARKS: Following our triangle thesis, one of the challenges of zk-Snarks is that is hard to be applied at scale as the complexity of the proofs scale linearly with the size of the database. Earlier this year, professor Eli-Ben Sasson from the Technion-Israel Institute of Technology published a highly-anticipated paper that describes a faster alternative to zk-Snarks which (to keep things confusing) he decided to call zk-Starks. From the paper professor Ben Sasson explains that “zk-SNARKs use public key (asymmetric) cryptography to establish security. zk-STARKs instead requires a leaner symmetric cryptography, namely, collision resistant hash functions, and thus removes the need for a trusted setup. These same techniques also eliminate the number-theoretic assumptions of zk-SNARKs (and BulletProofs) that are computationally expensive and prone to attack by quantum computers. This makes zk-STARKs both faster to generate and post-quantum secure.”
· TEE: Trusted Execution Environments(TEE) have emerged as a popular way to offload confidential computations in blockchain technologies. TEE technologies such as Intel’s Software Guard Extensions (SGX) isolated code execution, remote attestation, secure provisioning, secure storage of data and trusted paths for execution of code. Applications that run in TEEs are securely protected and almost impossible to be accessed by third parties. Security tokens can use TEEs to offload privacy computations from the core blockchain.
· Secure Multi-Party Computations: The protocol behind the Enigma blockchain, secure multi-party computations(SMC) is a cryptographic techniques that allows to execute computations against a set of inputs while keeping the inputs private. SMC can be used for parties in a security token exchange to trade assertions about information while keeping the actual information private.
· Buletproofs: Recently adopted by Monero, Bulletproofs provide a high performance protocol for confidential transactions. Bulletproofs addresses some of the limitations of protocols like zk-Snarks to enable the validation of transactions. A simpler version of Bulletproofs can be implemented on security token platforms to enable different levels of privacy in crypto-securities.
Access Control
Authorization and access control are probably the less developed areas of blockchain protocols that can be applied to security tokens. The principle of segregating access to different parties or transactions in a security token network seems like an obvious requirement of security token networks. Unfortunately, the protocols and techniques to enable access control in blockchain networks remain relatively nascent. Some of the techniques used by JP Morgan Quorum for node access control might be applicable to security tokens.
As the digital securities space evolve, the need for establishing a foundation for security capabilities becomes more important. In the context of security tokens, security can be expressed in three fundamental dimensions: identity, access control and privacy. The recent advancements in identity and privacy protocols can yield immediate benefits in the next wave of digital securities. While access control remains relatively limited, we should see some improvements in that area in the near future.
Demystifying Security of Security Tokens was originally published in Hacker Noon on Medium, where people are continuing the conversation by highlighting and responding to this story.
Disclaimer
The views and opinions expressed in this article are solely those of the authors and do not reflect the views of Bitcoin Insider. Every investment and trading move involves risk - this is especially true for cryptocurrencies given their volatility. We strongly advise our readers to conduct their own research when making a decision.