Latest news about Bitcoin and all cryptocurrencies. Your daily crypto news habit.
IP Geolocation in Cybersecurity Investigations
Location has always been a definite asset for tracking and apprehending criminals — so far.
In a world where illegal activities increasingly take place through digital means, cyber perpetrators often remain steps ahead in sophistication compared to those who are chasing after them.
Therefore, it’s only natural to expect that the ill-intended people of the web would be clever enough to conceal their whereabouts to avoid getting caught.
Still, we keep hearing about the benefits of IP geolocation APIs for cybersecurity, notably to prevent fraud and identity theft and counter-attack other known threats. So where does IP geolocation fit into this battle of wits?
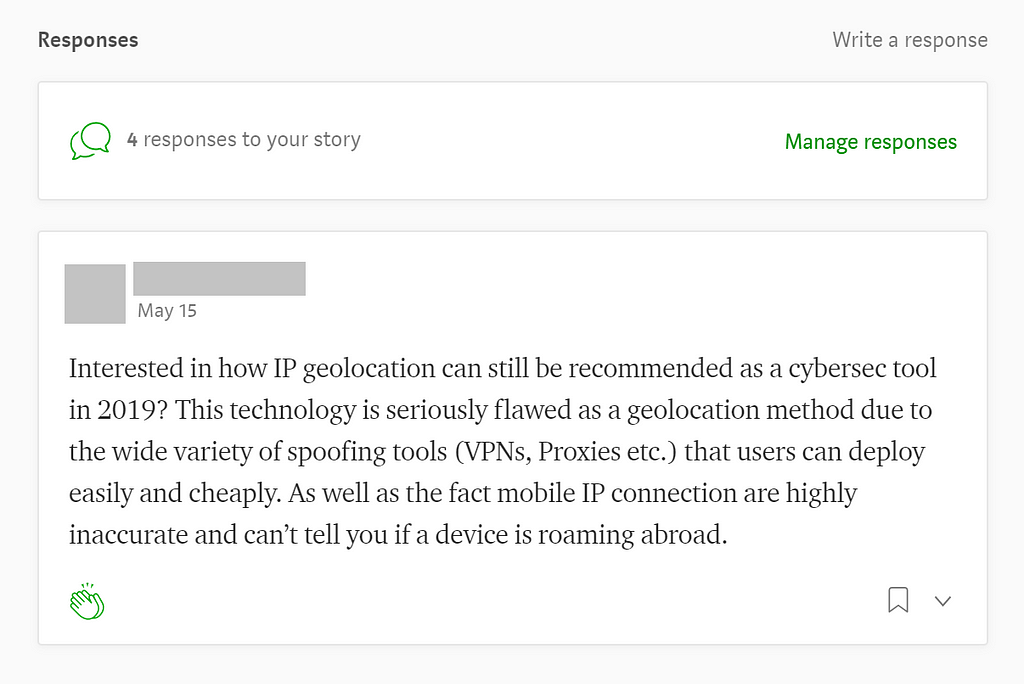
In the detractors’ corner, IP geolocation has been criticized for its lack of accuracy and the different ways attackers can circumvent the technology. Here is a comment left on a post I published recently:
On the other hand, there are a series of real-life events where the use of IP geolocation has proved useful for cybersecurity professionals and law enforcement agents to zero in on known bad actors and their networks. Let’s look at the following cases to illustrate this point.
Hansa: Dismantling Europe’s Largest Drug Marketplace in the Dark Web
Hansa lorded it over on the Dark Web as the largest drug market in Europe with 3,600 dealers and 24,000 products including cocaine, heroin, and ecstasy. To dismantle the trade, Dutch investigators initiated Operation Bayonet, which led to the identification of Hansa’s two administrators and their accounts — effectively allowing to seize full control of the site.
While Hansa’s buyers and sellers were placed under surveillance, ethical hackers subtly rewrote the site’s codes to get every user’s password and save the geolocation data of every picture. And here’s the masterstroke — the police tricked the anonymous users into opening a beacon file on their computers thereby giving away their locations. The operation resulted in authorities logging data on 10,000 malicious IP addresses and 420,000 users.
Silk Road: How it Met a Dead End
The notorious online black market for drugs operated for two years and proved elusive. The FBI finally closed it down after tracking the physical location of its servers via Tor. There is a debate on how the authorities were able to find a site like Silk Road which was hosted anonymously, but it is believed that the agency hacked the site and discovered related IP address.
Having done that, it wasn’t difficult to put a pin on the map. Indeed, the FBI got in touch with the hosting company and managed to image the server and plant tracking systems on it, which in turn permitted tracing all those that logged on and transacted on the site.
The LulzSec Takedown: Compartmentation Failure
The notorious hacking group that masterminded the high-profile attacks on the CIA and Sony Pictures was brought to its knees because of one wrong move from its leader. More precisely, Hector Xavier Monsegur failed to mask his IP address when he logged into an Internet relay chat room using his known pseudonym, “Sabu.”
That mistake helped authorities to trace the ISP and corresponding records assigned to that address — in the process also redirecting them to a connected subdomain page where Sabu posted a picture of his car.
So, Is IP Geolocation a Valid Tool of the Cybersecurity Trade?
As the foregoing cases demonstrate, tracking IPs can lead to users, their dubious operations, as well as the criminal network behind. However, IP geolocation is unlikely to be a silver bullet or should not be blindly trusted.
Cybercriminals do avoid leaving breadcrumbs that could redirect to their illicit affairs — most of the time involving the use of proxies and VPNs. That’s a fact. But it doesn’t mean that perpetrators and their systems are flawless.
Like any human being, they may let down their guard and make an error of judgment with the effect of revealing details on their whereabouts. IP geolocation may also prove itself useful only after other techniques such as ethical hacking have been exercised to weaken or knock down protective measures barring location detection.
Moreover, IP data might be erroneous due to different reasons. For example, invalidated registry data which leads to inconsistencies or IP geolocation service providers may not refresh their database with enough frequency. What’s more, a decline in accuracy is to be expected once we narrow down geo-searches from a country to the state, city, or neighborhood level.
That said, in today’s ever-complex cybersecurity landscape, it’s improbable that any system or source of data used in isolation will provide a universal picture to counteract threats and attackers — that’s actually one of the drivers behind the emergence of threat intelligence platforms and other composite security products which combine multiple capabilities for more meaningful analysis.
As such, the decision of whether or not to include IP geolocation as part of one’s cybersecurity plans very much depends on the technology’s ability to fill a gap left by other applications and alternatives.
Bottom line: IP geolocation is not a perfect source of data. But it can still significantly contribute to the identification of suspicious characters, often in combination with other techniques and cybersecurity components.
IP Geolocation: Can It Still Support Cybersecurity Investigations? was originally published in Hacker Noon on Medium, where people are continuing the conversation by highlighting and responding to this story.
Disclaimer
The views and opinions expressed in this article are solely those of the authors and do not reflect the views of Bitcoin Insider. Every investment and trading move involves risk - this is especially true for cryptocurrencies given their volatility. We strongly advise our readers to conduct their own research when making a decision.