Latest news about Bitcoin and all cryptocurrencies. Your daily crypto news habit.
 Photo by Markus Spiske on Unsplash
Photo by Markus Spiske on Unsplash
Last year I wrote an article about the pain of Secrets Management in ECS, but the world’s now a brighter place with some ECS upgrades from AWS.
The big change? Secrets now have 1st class support in ECS task definitions. They can be passed in from either AWS secrets manager or SSM parameter store depending on your use case. Better yet, none of these values will show up in the Task summary of the ECS console. For those using the CLI or Boto3, use the secrets section in your containerDefinitions and specify the full ARN of the secret as seen below. If you’re using an SSM parameter from the same region, you can use the parameter name rather than the full ARN.
If you’re more into ClickOps™, you can specify secrets in the task definition console as well. Instead of having their own section, they fall under the regular Environment variables tab using the valueFrom field. Unlike the initial implementation of this feature, when you visit the summary of any running task, any variables that use the valueFrom type won’t show up in the Environment variable listing (which is what you’d expect from a Secret).
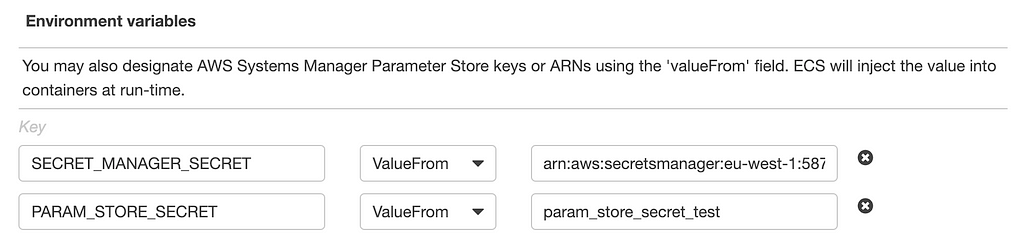 AWS Console — Task Definition Container Configuration
AWS Console — Task Definition Container Configuration
You’ll also need to add some new permissions to your ECS task execution role to make use of this feature. The following inline policy should be all you need to get started. secretsManager:GetSecretValue and ssm:GetParameters permissions are required depending on where you’re pulling secrets from, while the kms:Decrypt is only required if you’re using a custom KMS key in Secrets Manager.
Initially, this approach was rolled out only for the EC2 launch type but as of Fargate version 1.3.0, Fargate users can also make use of the secrets support. As always, it’s important to keep pricing in mind, especially with Secrets manager coming in at $0.40 per secret per month. It shouldn’t be an issue if you only run a few services with a few secrets each, but it doesn’t scale too nicely, especially if you’re on a tight budget.
CloudFormation for this feature is unfortunately slightly behind but has been confirmed working in certain regions as per the Feature Request. To keep up to date with changes to ECS secrets, or anything else across ECS, ECR, and EKS, check out the official Container Roadmap below.
Links:
ECS Secrets Done Right was originally published in Hacker Noon on Medium, where people are continuing the conversation by highlighting and responding to this story.
Disclaimer
The views and opinions expressed in this article are solely those of the authors and do not reflect the views of Bitcoin Insider. Every investment and trading move involves risk - this is especially true for cryptocurrencies given their volatility. We strongly advise our readers to conduct their own research when making a decision.