Latest news about Bitcoin and all cryptocurrencies. Your daily crypto news habit.
 KF
KF
The creation, accumulation and exchange of value via protocols is one of the most important attributes of the crypto ecosystem. From fat to thin protocols, the dynamics of crypto-networks are centered on the transferability of value across different parties and those dynamics permeate into higher level components such as DApps. Security tokens are, arguably, the first group of blockchain protocols that have bypassed the value creation architecture of public blockchains. In the current generation of security token solutions, the protocol layer captures little to no value which creates an increasing friction with the underlying blockchain layers. I like to refer to this dysfunctional dynamic as value leaking protocols and I think is one of the biggest existential challenges to the security token ecosystem.
Joel Monegro’s Fat Protocols thesis became one of the seminal papers in the first generation of blockchain applications. If you read this blog, you know that I disagree with many of the premises of the fat protocol thesis and I’ve written several papers refuting some of its core ideas. However, I would be the first one to acknowledge that there is an important subset of the fat protocol ideas that have held true across the evolution of the blockchain ecosystem. One of those foundation ideas state that, in blockchain applications, the protocol layer will accumulate some form of value. I explicitly state “some form of value” because I think that the idea that the lower protocol layers will accrue the biggest value is highly questionable and technologically and economically flawed. From that perspective, the different layers of protocols enabling a DApp will capture value in distinct but correlated ways. For instance, the value created in an utility token transfer has some correlation with the value captured by the ERC20 protocol which has some correlation with the value created by the Ethereum network.
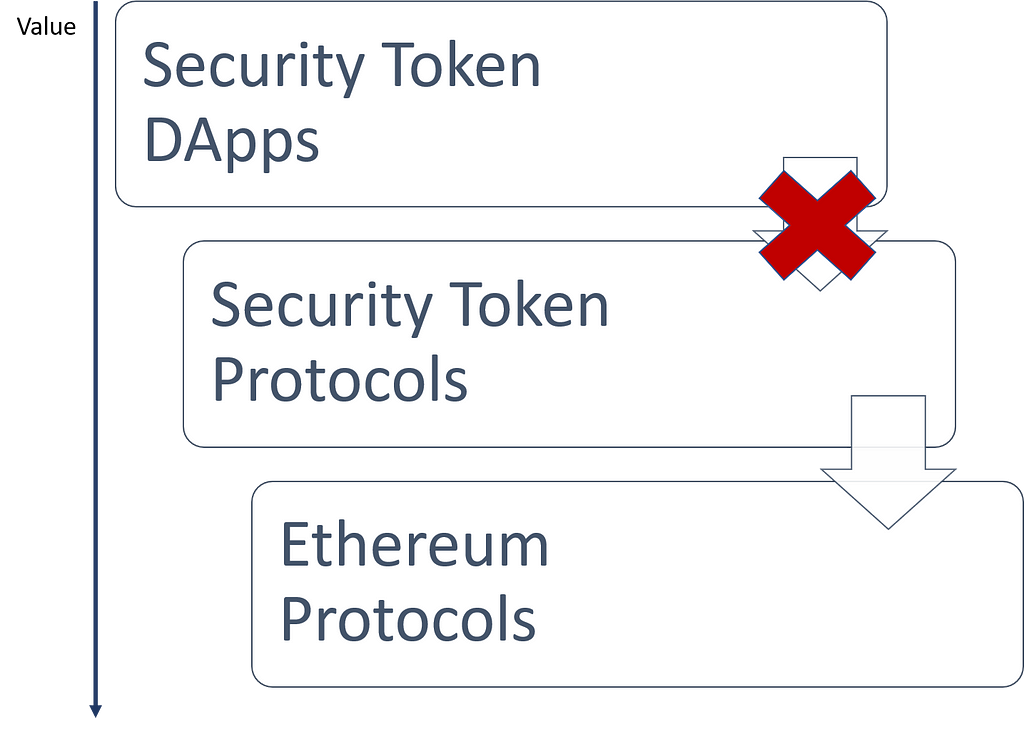
Extrapolating the value creation ideas of the fat protocol thesis to the universe of security tokens give us a very strange picture. Security tokens today are based on compliance protocols built on top of the ERC20 standard. However, the current ecosystem of security token protocols does not provide any native mechanism neither to capture the value created in the higher layers of the stack nor to transfer that value to the blockchain protocols in the lower layers. In a strange value-leaking dynamic, the value created by security token applications such as marketplaces or exchanges leaks through the protocol layer onto the lower layers of the stack. In that sense, security token protocols break the value creation chain of traditional DApps.
The Challenges of Value-Leaking Protocols
By now, you might be wondering what’s the big deal about security token protocols not capturing any value. After all, the internet if the biggest software architecture ever created and relies on protocols that don’t accumulate any form of value. However, the biggest difference between the internet and public blockchain applications is that the latter relies on tier1 protocols that require monetary exchanges to operate. In other words, can you imagine how different would be the architecture of the internet if TCPIP would have had its own digital currency? Public blockchain applications like security tokens are not only a technological architecture but a value creation system and building a value creation model on a broken value chain is a very difficult proposition.
Imagine an economy in which a layer such as the stock market are disconnected from the underlying monetary system. Trading dynamics will be disconnected from economic movements such as inflation, deflation, currency devaluation, etc. Can you imagine? Would be like a video game created by Hayek, Keynes and Marx 😉
Beyond the crazy theories, there are some very tangible challenges that a broken chain of value introduces in security token solutions.
Misaligned Value Creation Incentives
The most obvious challenge of value-leaking protocol is that they create a complete misalignment between the economic incentives in a tier1 network like Ethereum and the higher level security toke DApps. As a network like Ethereum growths, any monetary policies will directly impact security tokens. In an ideal ecosystem, the security token protocol layer should be able to regulate that impact to certain degree. Would be like if the US Federal Reserves could create monetary policy without considering the impact in the public securities market.
No Incentives to Build Security Token Protocols
Without a value creation model, there are minimum to none incentives to build and growth security token protocols and networks. The most successful Ethereum-based protocols have been the result of clear incentive models that align well with the underlying value creation in the Ethereum network. With a value-leaking model, it’s hard to envision security token protocols that will evolve beyond the effort of isolated vendors.
Inflation-Deflation Dependency
Value-leaking security token protocols makes higher level security token apps vulnerable to the inflation-deflation dynamics of the underlying blockchain network. What is even worse, this vulnerability is masked through a protocol layer so there is no clear way to plan for it. If the cost of Gas increases, that will have an impact on the business of security token exchanges but that whole interaction is hidden behind a security token protocol.
Vulnerability to Architecture Changes
It’s hard to envision the impact that architecture changes such as Plasma, proof-of-stack or sharding will have in security token applications. However, one is certain, any impact in terms of value creation or exchange will reflect directly in security token applications because the intermediate protocols don’t have any control over. Literally, security token DApps are vulnerable to an architecture layer that they don’t directly interact with.
It Gets Worse with Growth
Value-leaking protocol is the type of nightmare that gets worse as the surrounding environment growths. In this scenario, the value creation models for security tokens are going to become more challenging with the growth of both the Ethereum network as well as the security token ecosystem. Given that Ethereum is growing an order of magnitude faster than security tokens, the challenge is even worse.
Fixing Value-Leaking Security Token Protocols
The challenge of value-leaking security token protocol is far from trivial and there doesn’t seem to be any imminent solution. However, I would like to present a few basic ideas that might help to get the debate started:
1) Integrate Security Token Protocols with Existing Ethereum Tier2 Protocols: Integrating security token protocols into other tier2 protocols with clear value creation models could help mitigate some of the value-leaking dynamics.
2) Introduce Incentives Into Security Token Protocols: Obviously if security token protocols find a way to introduce clear incentive mechanisms, that would help to create a value model at that layer.
3) Build Value via Open Source Communities: Open source technologies have developed an entire playbook of creating value in forms that are not directly aligned with underlying layers of the stack. Building strong communities around security token protocols could be another form of value creation.
4) Build a Different Network: The most drastic form of value creation for security tokens would be to create a completely different network not dependent on the monetary system of the underlying blockchain. That effort is both risky and technological challenging but can yield significant dividends.
Providing clear mechanisms for creating and accumulating value remains one of the biggest challenges of the current generation of security token platforms. In the absence of that, the entire security token ecosystem becomes increasingly vulnerable to the monetary dynamics of the underlying network. We might not have fat security token protocols but some sort of value creation would be nice.
Value-Leaking Protocols and Security Tokens was originally published in Hacker Noon on Medium, where people are continuing the conversation by highlighting and responding to this story.
Disclaimer
The views and opinions expressed in this article are solely those of the authors and do not reflect the views of Bitcoin Insider. Every investment and trading move involves risk - this is especially true for cryptocurrencies given their volatility. We strongly advise our readers to conduct their own research when making a decision.