Latest news about Bitcoin and all cryptocurrencies. Your daily crypto news habit.
Some Thoughts About Security Token Networks [Part II]
This is the second part of an article that explore ideas about the emerging field of security token networks. The first part discussed some of the economical and technological foundations of the security token network thesis. Today, I would like to focus on the technical building blocks of such solutions and their relevance to security tokens.
Recapitulating some of the ideas outlined in the previous article, security token networks are likely to become one of the most interesting trends in the near future of security tokens. Conceptually, security token networks are permissioned blockchains that provide the native constructs to issue, distribute and trade security tokens. An important aspect to notice is that the ultimate manifestation of security token networks should be a small number of large blockchains that bring together retail investors and institutions and that enable access control and privacy across different segments of the network. In its initial incarnation, there are three fundamental elements to the value proposition of security token networks:
1) Network Effects: Security token networks might be the only way to foment true network effects within crypto-securities.
2) On-Chain Assets: Security token networks might be the most effective mechanism to ensure the creation of on-chain first security tokens.
3) True Disintermediation: Security token networks have the opportunity to set a foundation for removing the unnecessary middle man of the securities market.
While the value proposition of security token networks might seem clear, the technical materializations of it are not very trivial. In the current state of the market, building a security token network is as much as a technological challenge as a financial and regulatory one. From that perspective, let’s explore some of the key features that should be present in the first iteration of security token networks.
Key Capabilities of Security Token Networks
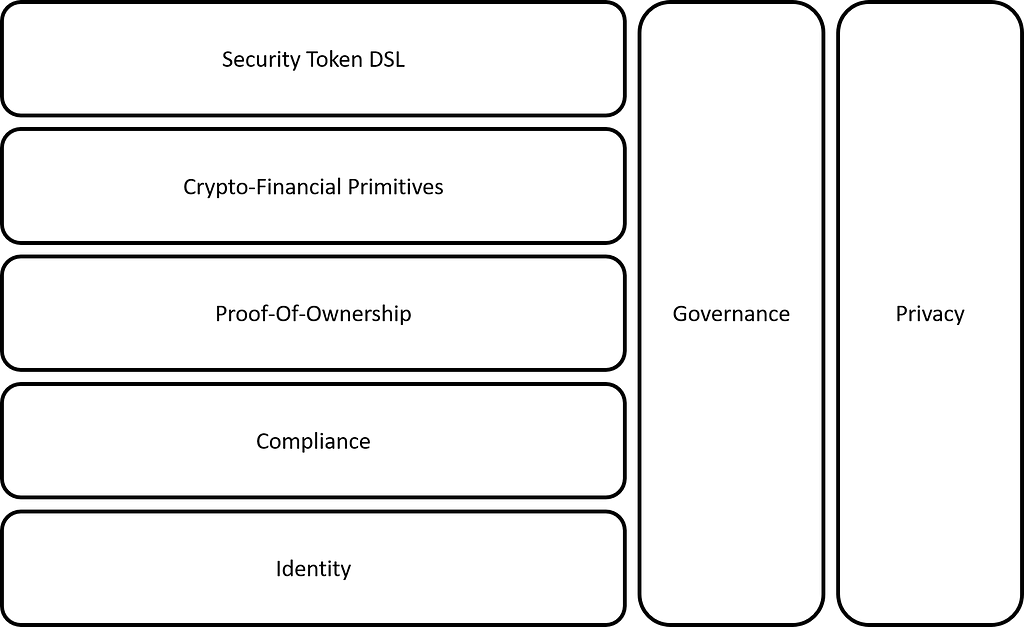
The goal of security token networks is to provide a native foundation to manage the lifecycle of crypto-securities. From a technological standpoint, that vision requires a series of building blocks that abstract native capabilities of security tokens as well as the corresponding experiences to enable the creation and post-issuance management of security tokens. Designing a security token network is a balancing act between enabling a rich feature-set and recognizing what’s technologically viable in the short term. From the many technical capabilities that could be relevant to a security token network, I’ve selected a small subset that I think are essential in the first iteration of this type of platforms.
If there is a single capability that a security token network should ensure is the correlation between a token transfer and a transfer of ownership. Today, a transfer of a security token needs to be correlated with off-chain processes that establish a transfer of ownership. Even though when many will argue that a security token transfer is a perfectly legal mechanism to transfer ownership, the technical foundation is still missing.
In a security token network, a proof-of-ownership(PoO) protocol would be responsible for ensuring the legal transfer of the ownership of an asset as part of a token transfer. A PoO protocol could be part of the consensus mechanism of a security token network requiring multiple nodes to vote on the transfer of ownership of the underlying assets of a crypto-security.
Compliance Protocols
Compliance is, arguably, the most obvious component of a security token network. The current version of security token platforms are fundamentally focused on compliance models and, frankly, the majority of them looks some of those protocols could be adapted to a broader security token network.
One important thing to notice is that we shouldn’t expect a single compliance protocol but a group of several protocols that address specific compliance needs. In a security token networks, issuers should be able to combine different protocols to address their compliance requirements without the need of writing brand new smart contracts.
Security Token DSL
A security token network needs a way to program security tokens. Assuming that most security token networks will be built on top of tier1 blockchains, they would rely on the underlying smart contract language for the creation of security tokens. However, a new runtime for crypto-securities should be accompanied by a new language to model these new instruments.
A domain specific language(DSL) for security tokens is a declarative model that abstracts the capabilities of crypto-securities. The outcome of the DSL should translate into executable code in the underlying smart contract language. In addition to abstracting the creation of security tokens, the DSL model would serve as a queryable, searchable definition of security tokens in the network.
Privacy
Access control and data privacy should be key building blocks of a security token networks. To some extent, privacy can be considered the main roadblock for the adoption of public blockchains as a runtime for security tokens. While we think a security token network should be publicly available to retail investors, it should provide access control and privacy mechanisms for different issuers or sections of the network.
Privacy protocols should be a first class citizen of security token networks. Embedding techniques such as zero-knowledge-proofs in privacy protocols could ensure the privacy of the data associated with security token transfers without necessarily sacrificing compliance requirements. At the same time, a security token network should enforce access control policies across different segments of the network to allow the safe interaction between issuers and investors.
Identity
A security token network can’t operate without an identity representation. Capabilities such as consensus, compliance or governance rely heavily on a common identity model that uniquely represents participants in a security token network. As identity gets established as a first class citizen in a security token network, the need for computationally expensive consensus mechanisms becomes less relevant.
An identity protocol must be an essential building block of a security token network. Representing the identity of issuers, investors and other nodes in the network in a portable and enforceable format will be an enabler for new forms of compliance and privacy protocols that address sophisticated use cases for security tokens.
Governance Protocols & Incentives
Any network requires governance models to ensure the correct behavior of its participants. The simple process of onboarding or offboarding nodes requires some governance structures to avoid gamified attacks. In the context of security tokens, governance is even more important given the regulated nature of the ecosystem.
A governance protocol should be another foundational element of a security token network. The role of the governance protocol would be to enforce voting decisions to regulate the correct behavior of the network. Depending the level of decentralization, a governance protocol might need a form of tokenized incentives to reward the participation of nodes in the governance dynamics of the network.
Crypto Financial Primitives
Security tokens are, ultimately, a programmable representation of a financial model such as debt, equity, convertible bonds or dozens of others. Today, most security tokens require the implementation of that logic by hand in the underlying smart contracts. As the space evolves, many of these dynamics will be abstracted as reusable protocols.
To streamline the issuance and lifecycle management of crypto-securities, a security token network should provide first-class protocols that abstract the behavior of key asset classes. These crypto-financial protocols can be arbitrarily combined to build more sophisticated forms of crypto-securities providing a true foundation for programmable finance.
Well, there you have it. Those are some of my favorite capabilities for the first wave of security token networks. It seems inevitable that these forms of tier2 decentralized networks will become an important element of the security token ecosystems. Getting the technological foundation right will be key determining the viability of this new form of crypto-securities runtime.
Some Thoughts About Security Token Networks Part II was originally published in Hacker Noon on Medium, where people are continuing the conversation by highlighting and responding to this story.
Disclaimer
The views and opinions expressed in this article are solely those of the authors and do not reflect the views of Bitcoin Insider. Every investment and trading move involves risk - this is especially true for cryptocurrencies given their volatility. We strongly advise our readers to conduct their own research when making a decision.