Latest news about Bitcoin and all cryptocurrencies. Your daily crypto news habit.

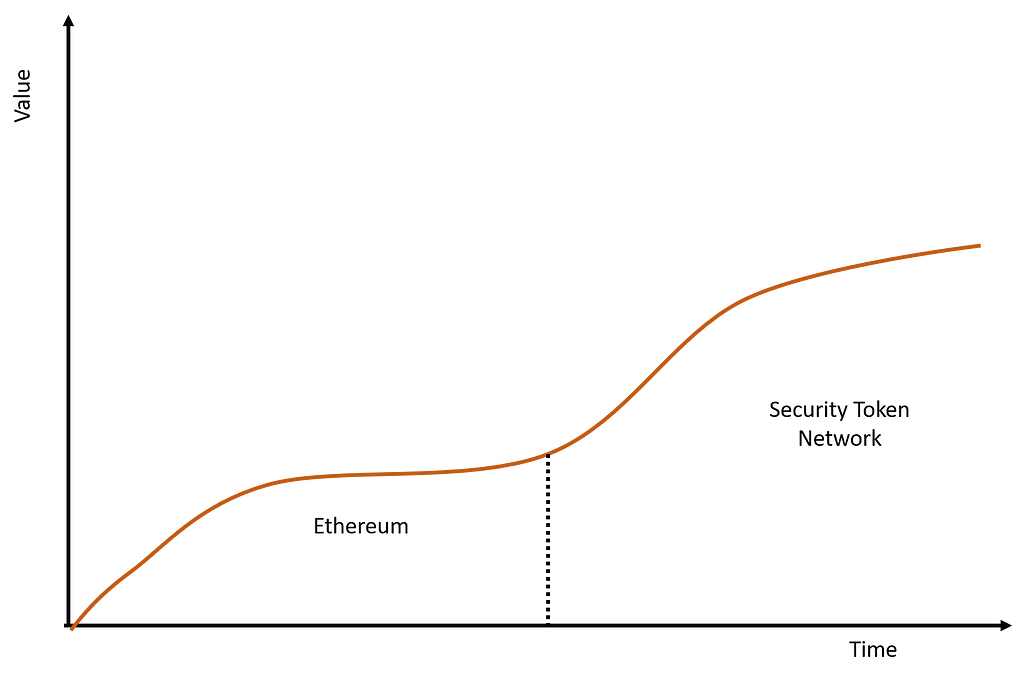
Recently, I wrote about the emergence of security tokens in permissioned blockchains as a “local maximum” phenomenon or an approach with strong short term perspectives but with questionable viability long term. The last part of that article explores the idea of a security token network that enables public availability with privacy constraints to link together the different participants in the security token ecosystem. Coincidentally, shortly after my article came out, we saw the news of Provenance raising $20 million on a security token offering(STO) to build a very similar model. Today, I would like to explore some ideas about the thesis of security token networks, its value proposition and risks.
As a market dynamic, the emergence of security token networks might be influenced by two conflicting phenomenon’s:
· Tier1 Blockchain Limitations for Security Tokens: Building crypto-securities today requires constant interaction with tier1 mechanics of runtimes like Ethereum which impose severe dependencies on the behavior of the smart contracts. It is only a matter of time before the limitations of tier1 blockchain like Ethereum become a roadblock for the implementation of specific security token scenarios.
· Privacy Requirements of Large Asset Owners: For the security token market to get past the current stage, it needs the participation of large institutional investors and asset owners. While these institutions can clearly see the benefits of crypto-securities, the current models based on public blockchains introduce privacy concerns that outweigh many of the benefits of this new asset vehicle.
· The Constraints of Permissioned Blockchain Models: The obvious answer to the privacy challenges of public blockchain is to rely on permissioned blockchain models and, in fact, this is an approach being explored by several large institutions and some startups venturing into the security token space. In my opinion, completely permissioned models results too constrained to achieve any level of relevance in the long term security token market.
From the value creation perspective, security token networks might be the rightful successor to Ethereum in the security token space. While the Ethereum network will accrue a significant percentage of the value created by security tokens in the short term, that value will steadily move towards tier2 security token networks.
What is a Security Token Network?
Conceptually, a security token network is a public and permissioned network of participants in the issuance and trading of security tokens. A security token network should provide a topology for the buy-side and sell-side of crypto-securities to interact without unnecessary gatekeepers. In principle, there are three key characteristics of security token networks that should be present in any implementation of this model:
· Public: A security token network should be publicly available to retail investors as well as large institutions and asset owners.
· Permissioned: A security token network should enable access control models that constraint access to different elements of the network based on specific permissions.
· Security-Token-Specific: A security token network should be based on tier2 protocols, tools and frameworks that abstract the lifecycle of crypto-securities. Tier1 protocols should be completely abstracted at this level.
· Decentralized with Validators: A security token network should not be controlled by a central authority and should enforce governance models for the fair interaction between its different nodes. Complementary, this type of network model should allow nodes with different levels of permissions to enforce rules on the network.
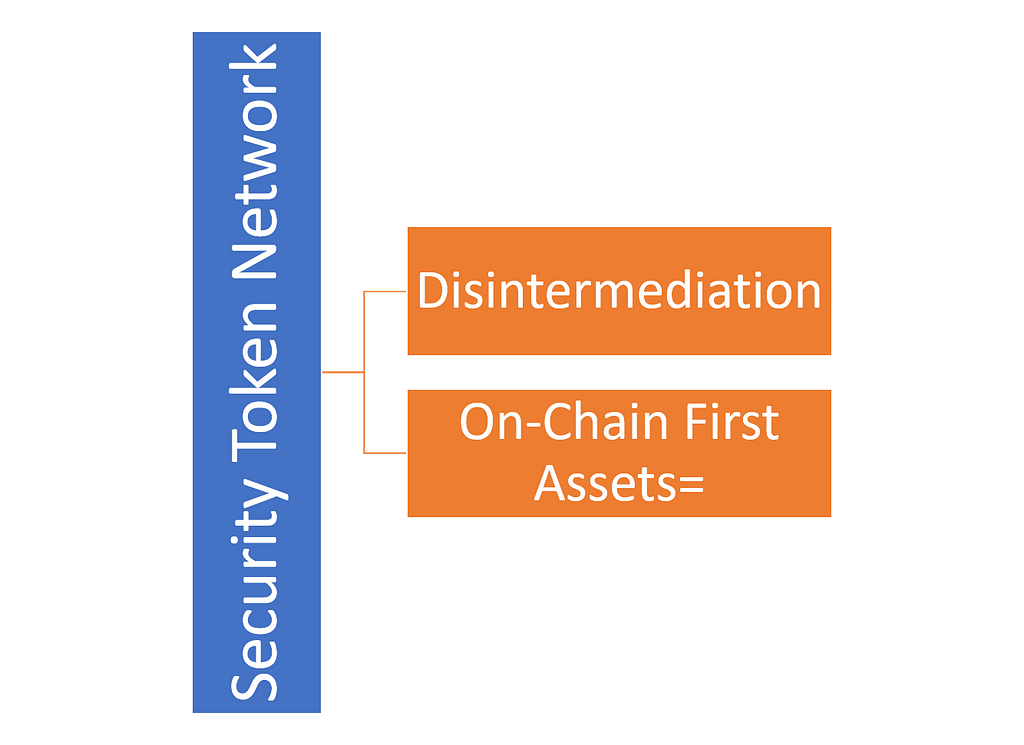
The Two Biggest Values Propositions of Security Token Networks: Disintermediation and On-Chain First Assets
When I think about the major benefits that can be unlocked with the creation of security token networks, there are two ideas that top the list: true disintermediation and issuance of on-chain first crypto-securities.
One of the favorite talking points of security token purists is the disintermediation of the financial systems. In theory, security tokens provide the mechanisms that can help to bypass many of the unnecessary intermediaries in the securities transaction. While we keep praising the value of disintermediation we continue building centralized systems that almost encourage the presence of intermediaries. Its not a surprise that many of the traditional financial intermediaries, that we are so desperately trying to remove, are coming up with offers for security tokens.
Mathematically, the process of disintermediation implies an increasing level of decentralization. In the context of security tokens, that means that creating a leaner, simpler securities ecosystems requires some form of a security token network with the right incentives to prevent middle-man to control the network. Without a network, we are taking the risk of recreating the same mess we have today on top of a blockchain.
The second benefit that I find fascinating about the prospect of a security token network is the issuance of on-chain first securities. Today, most security tokens live in this weird on-chain, off-chain dichotomy which is nearly impossible to reconcile at scale. There are plenty of off-chain mechanisms that are not represented on the blockchain and on-chain processes that require uncoordinated off-chain activities. A clear answer to that problem is to create security tokens that live exclusively on-chain and rely on minimum off-chain processes.
The main limitation to the creation of on-chain first security tokens is the absence of a network with the key roles in the securities ecosystem. At the current stage, security tokens require off-chain processes not only because they are created as tokenized representations of off-chain securities but also because many of the elements of its lifecycle live only outside a blockchain. The moment those elements create an on-chain presence in a security token network, we will be taking the first step towards the creation of on-chain first security tokens.
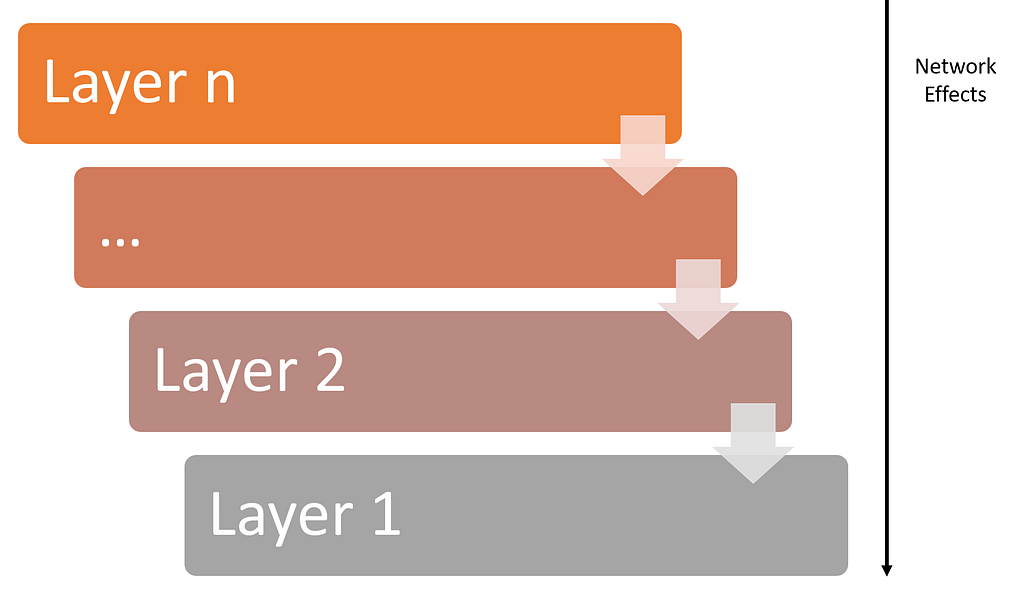
Security Tokens Need Tier2 Network Effects
The lack of network effects is one of the biggest threats to the viability of the security token ecosystem. As a tier2 blockchain stack, security tokens can’t rely on tier1 network effects. That’s completely illogical, network effects flow from higher to lower layers on a tech stack not the other way around. Without network effects, the security token ecosystem remains incredibly vulnerable to disruption by incumbents and at the risk of no creating long term value. Security tokens need network effects and network effects require a network.
If we agree on the value of a security token network, the next step is to brainstorm some of its technical capabilities. That will be the subject of the next part of this article.
Some Thoughts About Security Token Networks: Part I was originally published in Hacker Noon on Medium, where people are continuing the conversation by highlighting and responding to this story.
Disclaimer
The views and opinions expressed in this article are solely those of the authors and do not reflect the views of Bitcoin Insider. Every investment and trading move involves risk - this is especially true for cryptocurrencies given their volatility. We strongly advise our readers to conduct their own research when making a decision.