Latest news about Bitcoin and all cryptocurrencies. Your daily crypto news habit.

The adoption of permissioned blockchain technologies in the enterprise is a road full of challenges. The so called Web3 stack based on decentralized ledgers is still fundamentally immature to enable sophisticated enterprise business processes. Among the building blocks missing from enterprise blockchain platforms, identity raises to the top of the list as one of the omnipresent challenges of this new generation of enterprise solutions. At Invector Labs, we are regularly faced with the challenges of enabling identity management capabilities in permissioned blockchain solutions. As a result, we have developed certain ideas of the key capabilities and models of an identity layer for enterprise blockchain solutions which I would like to outline in this article.
Over the last five years, the identity management space experienced a renaissance with the emergence of a new generation of technologies that transition from complex systems such as CA or Microsoft Active Directory to more open, API driven platforms like Okta, Ping Identity, One Login as well as the corresponding stacks in the cloud platforms like AWS, Azure or Google Cloud. These platforms shifted the capabilities of identity from proprietary systems to open protocols such as SAML, OpenID Connect and others. However, this doesn’t mean enterprise identity management technologies are simple and easy to use. Quite the opposite, with the evolution of identity capabilities it also came an increase in the complexity of the requirements of identity management solutions. If look at the current spectrum of identity management architectures in the enterprise, there are a few characteristics that are worth highlighting:
· Based on Centralized Identity Providers: Enterprise identity management solutions typically rely on centralized identity providers that receive some form of user credentials as input and output an identity token.
· Based on Identity Protocols: At the moment, a significant percentage of enterprise identity management solutions leverage protocols like SAML, OAuth2 for its interactions.
· Fractionalized: The identity of users in enterprise environments is spread across different line of business systems or user directories. As a result, different applications tend to interact with different representations of a user’s identity.
Fundamental Frictions to Enable Identity in Permissioned Blockchains
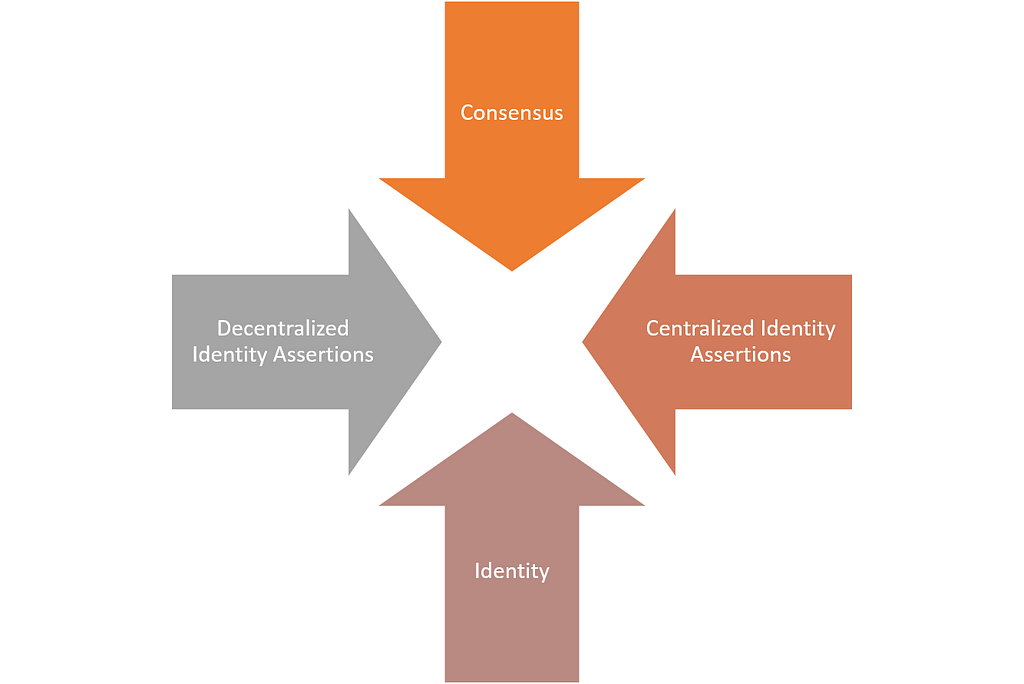
Putting all these pieces together, we get a picture in which the identity of users in the enterprise is distributed across many systems but enforced by central identity providers. When comes to identity, there are two fundamental frictions that need to be addressed between the current architecture of enterprise systems and the universe of blockchain technologies.
· Consensus vs. Identity
· Centralized vs. Decentralized Identity Assertions
Enabling identity management capabilities in permissioned blockchain scenarios goes beyond a technical challenge creates a friction with one of the fundamental principles of decentralized layers. The biggest contribution of blockchain technologies was that, for the first time in the history of computer science, we have a model in which we can trust math and cryptography instead of centralized parties. Using that principle as a foundation, blockchain architectures evolved based on consensus protocols such as proof-of-work(PoW) or proof-of-stake(PoS) that rely on computations in order to make decisions. In that decentralized world, identity hasn’t been a fundamental building block as the dynamics of the network should arrive to an optimal decision-making process.
The computation-based consensus models of blockchain stacks fundamentally contrasts with the enterprise solutions in which the identities of the participants are well known. In that sense, you can argue that consensus protocols deliver very little in a world of known identities.
Centralized vs. Decentralized Identity Assertions
The current architecture of enterprise identity management systems relies on centralized gatekeepers to create assertions about user’s identities. Reconciling that model with distributed ledger architectures in which the assertions will be distributed across a network of participants is far from trivial. Ideally, we need a model in which identity assertions are placed on-chain encoded in a cryptographically secured way and distributed to the relevant network entities.
The Building Blocks of Decentralized Identity in Permissioned Blockchains
To address some of the challenges listed in the previous section, there are a few technological components that we have found incredibly relevant in permissioned blockchain architectures.
Proof-Of-Authority
Proof-Of-Authority(PoA) is a type of consensus mechanism that relies on identity as a first class citizens. In PoA networks, consensus is achieved by referring to a list of validators (referred to as authorities when they are linked to physical entities). Validators are a group of accounts/nodes that are allowed to participate in the consensus; they validate the transactions and blocks. PoA doesn’t require solving computationally expensive puzzles to commit a transaction. Instead, a transaction simply has to be signed off by the majority of validators, in which case it becomes a part of the permanent record.
When adapted to enterprise blockchain scenarios, PoA consensus is very relevant as can leverage the existing identity of users and systems instead of relying on computational puzzles. There are several implementations of PoA consensus that are relevant to permissioned blockchains including Parity’s and Microsoft Azure
Decentralized Identity Protocols
The emerging field of decentralized identities looks to leverage decades of technological progress in identity methods and standards in the new world of decentralized runtimes. To achieve that, identity needs to be reconstructed using an architecture moves a lot of the traditional identity dynamics into a decentralized network of participants.
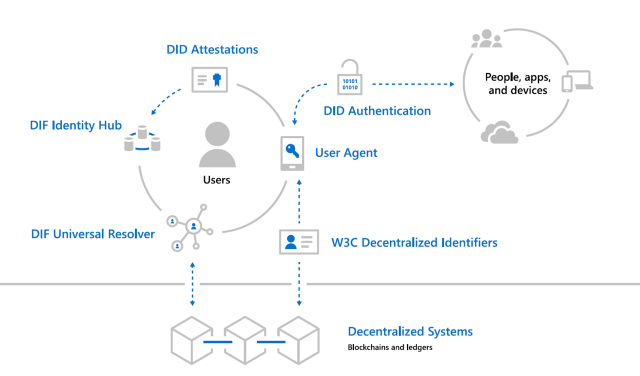
Microsoft has been one of the leaders in the identity management space for the last 20 years but even they realize that blockchain runtimes require a new identity models. Inspired by DIF, Microsoft recently proposed a forward-thinking architecture to enable decentralized identities in blockchain runtimes. The Microsoft architecture includes the following components:
· W3C Decentralized Identifiers (DIDs): IDs users create, own, and control independently of any organization or government. DIDs are globally unique identifiers linked to Decentralized Public Key Infrastructure (DPKI) metadata composed of JSON documents that contain public key material, authentication descriptors, and service endpoints.
· Decentralized systems: DIDs are rooted in decentralized systems that provide the mechanism and features required for DPKI.
· DID User Agents: Applications that enable real people to use decentralized identities. User Agent apps aid in creating DIDs, managing data and permissions, and signing/validating DID-linked claims.
· DIF Universal Resolver: A server that utilizes a collection of DID Drivers to provide a standard means of lookup and resolution for DIDs across implementations and decentralized systems and that returns the DID Document Object (DDO) that encapsulates DPKI metadata associated with a DID.
· DIF Identity Hubs: A replicated mesh of encrypted personal datastores, composed of cloud and edge instances (like mobile phones, PCs or smart speakers), that facilitate identity data storage and identity interactions.
· DID Attestations: DID-signed attestations are based on standard formats and protocols. They enable identity owners to generate, present, and verify claims. This forms the basis of trust between users of the systems.
In the context of permissioned blockchain implementations, decentralized identity protocols present a clear bridge between traditional enterprise identity management systems and blockchain DApps.
The Zero-Knowledge Proof Identity Stores
The concepts of attestations or claims as well as decentralized hubs are some of the most important principles of decentralized identity models. One interesting idea is to combine decentralized hubs with zero-knowledge-proofs protocols such as zk-SNARKs to add another level of privacy to the DIDs while allowing other protocols to validate identity attestations. I like to call this concept zero-knowledge identity stores and has been embraced by protocols like uPort.
In the zero-knowledge identity store model, the assertions related to the user’s identity will be encoded using zk-SNARKs and published on-chain. Smart contracts can validate assertions about the user’s identity without revealing anything about the underlying user’s identity which maintains the execution on-chain while enforcing high levels of privacy.
Some Decentralized Identity Solutions you Should Know About
The space of decentralized identity is certainly very nascent but there are already some relevant efforts that might serve for inspiration to security token protocols. Here are some of my favorites:
· uPort: uPort has been steadily building a series of protocols and solutions for managing identities in decentralized applications. The current stack is compatible with Ethereum smart contracts and can be leveraged in permissioned blockchain applications
· Azure BaaS: The Azure team has done a remarkable job extending the core protocols of different blockchain to leverage Azure Active Directory identities. A recent example of this work was the implementation of the proof-of-authority consensus protocol in Ethereum applications.
· Sidetree: It is a composition of code-level components that include deterministic processing logic, a content addressable storage abstraction, and state validation procedures that can be deployed atop Layer 1 decentralized ledger systems (e.g. public blockchains) to produce permissionless, Layer 2 DID networks.
· Hyperledger Indy: If you live in Hyperledger land, Indy offers one of the most complete stacks to enable identity management capabilities. The current version of Indy includes tools and libraries that implement some of the most common patterns in decentralized identity solutions.
Identity is one of the fundamental building blocks of permissioned blockchain applications and one that needs to be addressed in order to enable the mainstream adoption of these technologies. Efforts such as the decentralized identity foundation(DIF) are leading the way to bridge the gap between traditional identity systems and the new world of blockchains. Although there are some protocols and tools in the space, enabling identity capabilities in enterprise blockchain solutions is still a fairly complex endeavor.
Identity: The Elephant in the Enterprise Blockchain Room was originally published in Hacker Noon on Medium, where people are continuing the conversation by highlighting and responding to this story.
Disclaimer
The views and opinions expressed in this article are solely those of the authors and do not reflect the views of Bitcoin Insider. Every investment and trading move involves risk - this is especially true for cryptocurrencies given their volatility. We strongly advise our readers to conduct their own research when making a decision.