Latest news about Bitcoin and all cryptocurrencies. Your daily crypto news habit.

An integral part of winning new customers is their confidence in your expertise, and the best route to becoming an expert is learning by experience. With cyber threats such as phishing on the rise, information security (infosec) is now a prerequisite within most projects we work on; it’s at the forefront of customers minds.
To put the issue into perspective, the American IRS reported a 60% surge in phishing attacks in 2018, while the 2018 Phishing Trends Report by PhishLabs highlights a 237% increase in attacks targeting SaaS systems.
In response, there’s a definite shift towards educating the broader public through awareness campaigns and sources such as Watch Your Hack. Frankly, I don’t think this process of education can happen fast enough — most of the C-suite customers I speak to know about hacking and the damage it can do, but still can’t pick out the tell-tale signs when a phishing email lands in their inbox.
What can be done?
Technical filters can provide a degree of defence against phishing attacks, but a large proportion of the security burden still falls on the individual, which is why education matters.
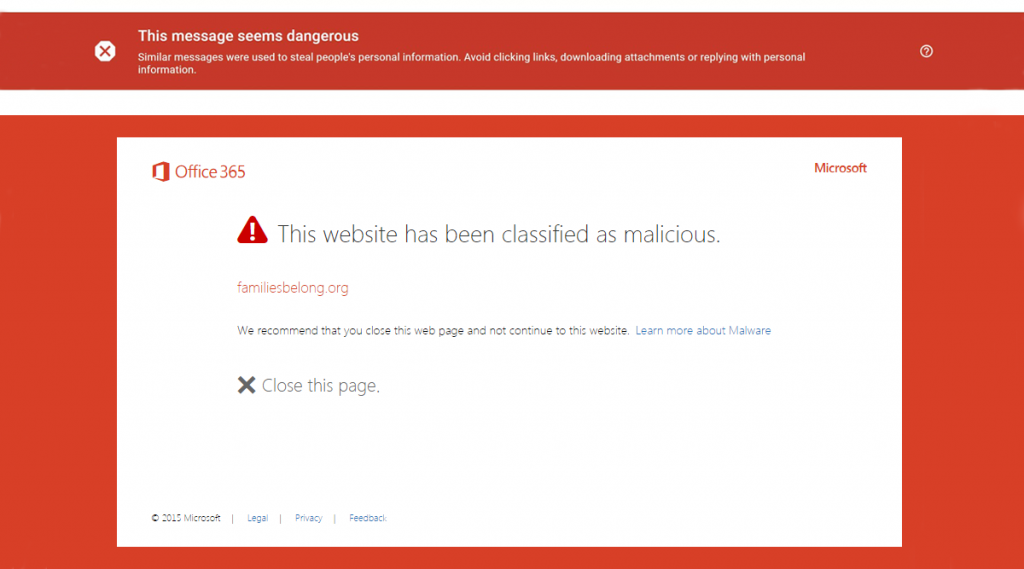 Technical filters such as those from Gmail (top) and Office 365 (bottom) can prove effective but should be supported with staff training.
Technical filters such as those from Gmail (top) and Office 365 (bottom) can prove effective but should be supported with staff training.
That’s why for the past few years I’ve been championing our infosec running red flag exercises and scheduling education workshops to help maintain our level of readiness. The intention is that everyone we work with knows what to spot, what to do, and when to ask for help in the event of an incident.
It’s now baked into our everyday routine. Moreover, it’s become part of our strategic approach when working with customers to architect, design and build their digital solutions. In addition to this, we’re also able to offer added value by educating their team and stakeholders on cyber threats.
But, I digress, let’s get back to the point of this article.
Gone phishing
So, my anecdotal evidence suggests that most C-suite customers don’t know how to pick out a phishing email from a genuine message, but I wanted to explore this theory further. Who better to test it on than my own unwitting company…
Our bi-annual JAMS hackathon provided me with a few days of tinkering time to plan the exercise and, with the assistance of a trusted cyber partner, we designed a series of phishing scams that were aimed to test the Browser team’s readiness.
 It took the two days of our JAMS session to build the test. I had to fib about what I was working on and make excuses about why I didn’t have anything to show the team at the end of the hackathon.
It took the two days of our JAMS session to build the test. I had to fib about what I was working on and make excuses about why I didn’t have anything to show the team at the end of the hackathon.
At the end of two-day JAMS we were happy with the proposed test. We’d whitelisted an email server, designed a fake HTML email (design to closely mimic one of our 3rd party digital services), created a phoney landing page and set up a database to record all of the leaked information. At the outset, we’d merely wished to record who in our company opened the phishing email, but at the final go-live we’d added extra data points, including:
- Whether the email was delivered to the individual
- Whether the individual clicked any links within the email
- What sensitive information the individual entered into the landing page
What I also really wanted to know was how well my team had been listening during the previous practical red flag exercises, educational workshops and talks. Thus, I also tracked:
- Who reported it to the information security officer (ISO)
- How long did it take them to report it to the ISO
- Was the incident escalated, and to whom
- What steps were taken to find out if anyone had entered sensitive information
- If a staff member had entered sensitive information, what was done about it
So, how did the team do?
The results gained from the test were fascinating.
Even amongst our team of tech-savvy developers and designers, the email (which was from a plausible but not perfect send address) still managed to fool 36% of recipients into clicking through to the landing page.
Happily, 20% of the team did identify the email as suspicious and quickly warned the wider group. As an aside, I observed that it was simple for our office team to verbally warn each other about the message. Our remote workers, on the other hand, felt a little more at risk. They were physically isolated, so the warning relied on them reading their Slack messages or the warning email before opening the phishing mail.
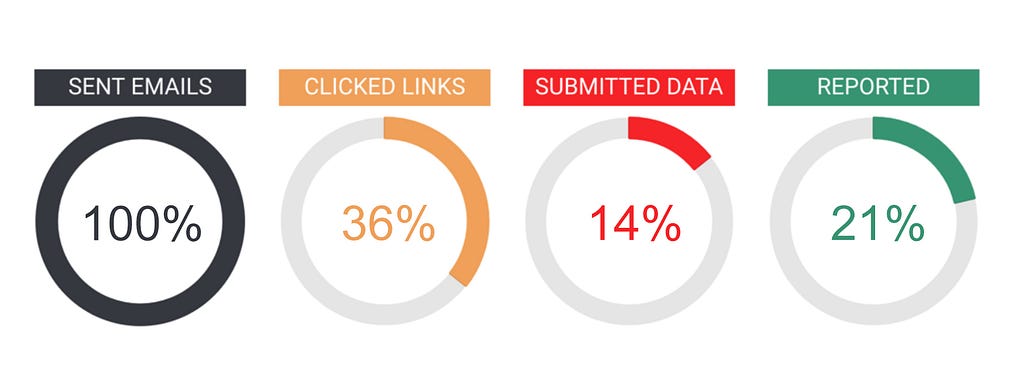 Despite being a team of tech-savvy developers, our scores weren’t perfect
Despite being a team of tech-savvy developers, our scores weren’t perfect
What to watch for
After the test was over, I spoke to those who picked up on the scam and asked what they noticed that made them warn the team. Mostly, it was that the document that the email referenced had a title that seemed implausible (Browser Christmas Plan); it didn’t sound like a document we’d actually create or share. That raised suspicions, and then, when they looked closer at things like the link destination URL and the send address, those suspicions were confirmed.
If I’d have picked a slightly less whimsical document name, more people would have probably been tricked into clicking through and entering their details into our bogus landing page.
Taken as a whole, the results created a picture of our current readiness, but more importantly, they also highlighted new areas where training could help maintain the team’s preparedness, and keep them aware of what to spot, what to do, and when to ask for help in the event of an incident.
Companies of all shapes and sizes are increasingly leaning on technology to support their business. Simultaneously, cyber threats are increasing in terms of persistence and severity, and it’s not going away; cybersecurity is fast becoming one of the most in-demand services. Be it developers, finance, or management everyone will benefit from training, and a phishing test is an excellent way of introducing team members to cyber threats. When it comes to infosec, every company needs to make readiness a priority.
What’s next?
A week or so after the fake attack, I ran a presentation to the team revealing that it was, in fact, a test and detailing the results. As part of this, I also refreshed the team on our official protocol and got everyone to go through a scenario-based questionnaire to help everyone learn and spot a cyber attack. It also reinforced our position on information security, protocol, and tips on how to mitigate the risk outside of work. Naming and shaming don’t help anyone, but education does. Use it to maintain readiness and stay safe to cyber attacks.
If you’re interested in cyber awareness and how I ran the exercise with our cyber partners, then feel free to reach out to me on twitter at @renemorency.
About Browser
We create enterprise web apps for a better, more productive workplace. We’ve helped clients such as Shell, British Airways and UK Gov improve efficiency and streamline their business. Visit us at Browser London.
Originally published at www.browserlondon.com on March 5, 2019.
Phishing My Own Company: An Infosec Lesson for Businesses was originally published in Hacker Noon on Medium, where people are continuing the conversation by highlighting and responding to this story.
Disclaimer
The views and opinions expressed in this article are solely those of the authors and do not reflect the views of Bitcoin Insider. Every investment and trading move involves risk - this is especially true for cryptocurrencies given their volatility. We strongly advise our readers to conduct their own research when making a decision.