Latest news about Bitcoin and all cryptocurrencies. Your daily crypto news habit.
Unveiling Blockchain’s full Potential — A new Era of Internet Protocols and Applications
What you can expect from the read:
- Introduction to cryptoeconomic mechanism design, a new art of designing protocols next to cryptography or machine learning, including what it is and what is the rationality, and how you can leverage it in your own applications and protocols
- A discussion why Blockchain is the missing technological piece to harness cryptoeconomic mechanisms in Internet applications and services
- Two example HTTP protocols showcasing the power and practicability
- Summary of future emerging killer applications resulting from the application of cryptoeconomics
 courtesy of Kristina Flour
courtesy of Kristina Flour
Cryptoeconomic mechanism designing is the true ingenuity of Blockchain. In this article we explore the opportunities to reshape Internet protocols assuming a Blockchain is in place. We discuss how cryptoeconomic incentives can be used to make HTTP resilient against Distributed Denial-of-Service and Man-in-the-Middle attacks.
1. Introduction
Blockchain has emerged to one of the most promising technologies of the digital society. In fact, it has all ingredients to change the Internet as of today and foster novel application and services.
As a cryptographer and cryptography professor, I have been following Blockchain technologies with much excitement from almost day one. I am pleased to witness how the concept of a decentralized cryptocurrency, as for example put forth by Bitcoin, evolved into a fully distributed computing environment. When one calls Bitcoin the mother of cryptocurrency technologies, Ethereum clearly must be named here as the foundational technology to a distributed computing infrastructure and the initiator of next-generation Blockchains. In a wonderful and impressive way the Ethereum community lifted the idea of payment transactions into full fledge, distributed programs (known as smart contracts). Although the principals of distributed computing have been researched (to the best of knowledge) since the 80s, although they have become a pillar of theory in computer science, and are represented in almost every computer science curriculum nowadays, it is the first time the concepts receive mainstream attention.
When a new, technological paradigm awakes, a critical question must arise:
What can one build with a Blockchain?
While the question rather is formulated with a techie’s jargon, it shall imply the curiosity of striving for new applications, services, business models and markets. In fact, I can’t remember the vast number of research reports, whitepapers, panel discussions and conferences aiming at answering exactly this question. I have seen experts on stage trying to justify new use cases with Blockchains where they relied on the immutability properties of a distributed database (in other words, you can store data in the blockchain and nobody can revert the entry). It was never clear to me — I have to admit — why a distributed database like Cassandra does not do the job. I had rather the impression people were trying to ride on the hype without having fully grasped and unveiled the magnitude of next-generation Blockchains like Ethereum, Cardano, Hyperledger, etc. For ease of presentation, I will refer to next-generation Blockchains in the following simply as Blockchains.
2. Blockchain is the New Application Layer
The Blockchain changes the way we perceive the Internet and gives a radically new approach to designing Internet protocols, applications and services. In terms of the TCP/IP reference model one can think of Blockchains adding a new layer (let’s call it the ‘Blockchain layer’) on top of the network layer such that novel protocol and application layers build atop or more interestingly aside (blue marked layer, cf. Fig below).
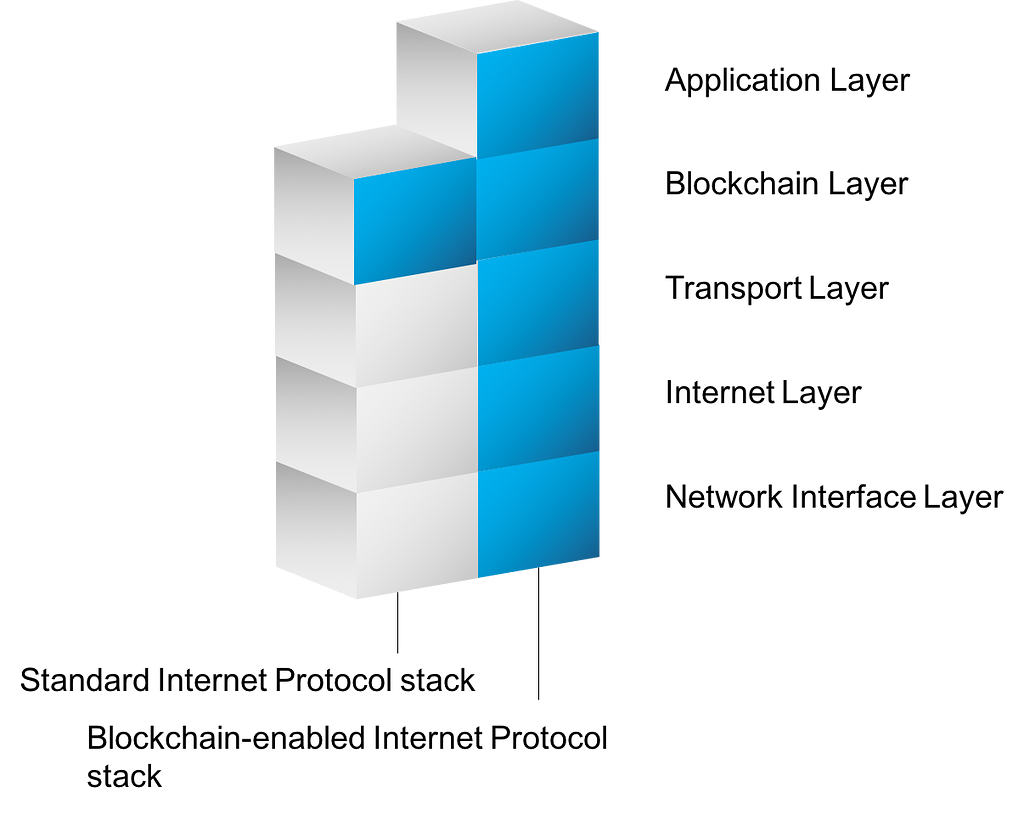 TCP/IP model on the Internet (left); Blockchain-enabled Internet model (right)
TCP/IP model on the Internet (left); Blockchain-enabled Internet model (right)
The opportunities are overwhelming. One can develop on top of the Blockchain layer communication protocols, private and public networks, applications and businesses with novel and innovative properties. (Below I sketch how to design with aid of the Blockchain layer a variant of the HTTP protocol resistant against denial-or-service — a major weakness of the Internet design — as well as a variant with the provision to cryptographically authenticate the client.) The point that needs to be stressed here is that the Blockchain layer co-exists with the other Internet layers and is useful to enrich their functionality, interoperability, and security.
Before delving into technicalities, let’s elaborate on the functions and services the Blockchain layer leverages for the design of Internet protocols and applications:
- Incentive Mechanism. A Blockchain allows to design protocols and applications based on incentives and gives raise to a new class of Internet protocols and applications in presence of rational network participants. Rational players are selfish. They cheat, lie, are unfair as long as they maximize their incentives.
- Unique Identity. A Blockchain gives a cryptographic identity useful for identification, authentication or access control.
While the Blockchain layer offers additional services like a byzantine fault-tolerant storage, an immutable data structure, a distributed program execution environment, and some other interesting features, this article aims at discussing the above properties, which I believe have the greatest impact on protocol and application design of the future Internet.
3. On Cryptoeconomic Mechanism Design and a Denial-of-Service resilient HTTP Protocol
The term cryptoeconomic mechanism design has been ambiguously used in context of Blockchains. Mechanism design is a research field in the intersection of economics and computer science that deals with the question of designing protocols (games) with the premise to incentivize the players to reach a desirable outcome. Mechanism design is seen as the dual to game theory which analyzes the protocol outcome according to the players’ utility. It is also different from cryptographic protocol design which aims to reach a desired outcome in presence of malicious players (as opposed to rational players in the mechanism design model). The term cryptoeconomic refers to incentives implementable, loosely speaking, through the Blockchain (or more precisely, the sparsity of the intrinsic token).
Mechanism design works under the assumption that the players share the common belief some object (e.g., material, good or service) has a value. Further we assume that players naturally demand for the object and fear the moment of losing the object. Following the fundamental principles of (free-market) economies, when demand for the object increases, the value (e.g., price) goes up as well. Hence, making the object sparse will increase its value.
Sparsity of objects in mechanism design is a splendid tool to incentivize the players to behave in certain ways, based upon their private information, that leads to (socially) desired outcomes. It is exactly this economic entanglement that is powerful enough to design protocols with a particular outcome. The basic idea follows a trigger strategy:
- Incentivize a desired outcome through rewarding the player by increasing the supply of the object
- Disincentivize a desired outcome through punishing the player by reducing the supply of the object
3.1 Straightforward Application: The Parent-Child-Pocket Money Protocol
Though all of this may sound very academic, the underlying ideas of incentive strategies to achieve a particular outcome are ubiquitous and find daily application. Governments use fine and tax reductions to enforce laws of their constitution. Groceries use vouchers to incentivize customers to shop at their store and disincentive them to buy the same good in a different store. Parents naturally leverage incentive strategies to educate their children. Let’s have a closer look at a classical parental mechanism design.
Protocol Goal: Make sure their kid gets good grades in weekly math exams such that the final grade is an ‘A’. The kid needs at least 125 bucks within the next 10 weeks to buy the playstation.
Protocol Assumption: Kid highly appreciates every cent of pocket money as it badly wants to buy a playstation. The kid is talented, eager and a good mathematician. The average grade is a ‘B’ so going for an ‘A’ is realistic. For ease of presentation, let’s assume the teacher’s grading system consists of two grades only (‘A’ and ‘B’).
Protocol Setup: The kid gets 10 bucks per week pocket money.
Protocol: Mum and Dad get together and agree with their child on the following mechanism:
- If the kid passes the weekly exam with an ‘A’, it gets a rewarded 10 bucks on top of the pocket money.
- If the kid passes the weekly exam worse than an ‘A’, a penalty of 5 bucks is taken from the pocket money. (Note, the penalty is only for exposition. It would break my heart to punish my kids.)
Analyzing the mechanism, let’s consider the case that out of 10 exams, the kid gets 5 times an ‘A’ and 5 times a ‘B’. That’s the threshold for the teacher to issue an ‘A’ on average. This way the kid makes 125 bucks and reaches the target goal. Should it miss the ‘A’ on average after the final exam, the kid misses also the opportunity to buy the playstation. Likewise it will miss the goal of owning a playstation in 10 weeks, if it denies to participate in the game.
3.2 Cryptoeconomic Mechanism Design through (or thanks) the Blockchain
One of the main beauties and in my opinion the real sensation of Blockchains is that they give us exactly the ingredients to design protocols and applications based on incentive strategies:
- Tokens. Although a token is a sequence of bit-strings along a digital signature, it is widely accepted as an object with value. It can be traded and exchanged for fiat. There exists already a strong ecosystem to turn tokens into assets and it has proven to work.
- Blockchain Network. A Blockchain network offers the necessary infrastructure not only to design, but also to implement and enforce incentives. Smart contracts readily give us the tool to describe and execute protocols based on incentive strategies.
It are exactly these two properties that make the Blockchain paradigm so powerful. Blockchains lay the foundation for Internet protocols and applications based upon game-theoretic principals. In conjunction with cryptography and artificial intelligence, developers have a third technique in their portfolio to implement protocols and applications with novel properties that indisputably broaden the utility and practicability of the Internet and which were unattainable with prior techniques (such as cryptography). That’s why the Blockchain paradigm can change the Internet as of today.
Incentive-based mechanisms have already been identified by the Blockchain community and we witness their adaption in some promising projects (cf., Brooklyn project). Among them probably the most prominent usage so far have found Proof-of-Stake consensus protocols like Ethereum’s Casper or Cardano’s Ouroboros. Proof-of-Stake protocols implement a mechanism design known as staking to achieve an agreement on the next block. The high-level idea behind staking is as follows.
- The network chooses the primary typically according to her willingness to stake a high amount of tokens. By staking we mean the mechanism of locking the tokens as a collateral to backup a future decision (namely the next block).
- The primary has the task to define the next block. Her proposal is challenged by a group of validators who co-stake, each validator an amount of tokens proportional to the size of the group, and verify the proposal.
- Validators challenge the proposal of the primary by a majority voting and share the stake of the parties deviating from the quorum. This implies that the primary fortifies her stake in case of a correct proposal; she looses her stake in case of a dishonest proposal (like approving a double-spending transaction).
Analyzing the staking mechanism, we observe that the primary’s incentive is to make an honest block proposal. Otherwise she looses a significant amount of her stake. Further she has a natural incentive to volunteer as a primary. She owns a significant portion of the total stake and if it turns out the network is unstable the value of all of her tokens diminishes. Validators have the incentive to vote honestly as they risk to loose their stake in case of decision against the quorum. The fact they potentially receive a reward is an incentive to engage in the validation process.
The staking mechanism has much in common with the principles underlying our parents-child-pocket money protocol. Good behavior is rewarded while bad behavior is punished.
3.3 A non-straightforward Application: Denial-of-Service resilient HTTP Protocol
The Internet is clearly one of the greatest inventions of the last millennium, and much of its success must be accredited to the people of the IETF and related standardization bodies that over decades maintained an interoperable protocol stack. In the light of all the astonishing work, probably one of the design weaknesses of the Internet is less than stellar protection against denial-of-service attacks. These cyberattacks harm the stability of the Internet. In a denial-of-service attack, one repeatedly requests a service from the target server until the numerous requests outperform the server’s capability to process the requests. As a consequence the server stops to operate and typically is no more reachable on the Internet. Think of the consequences the digital society would experience, for example, when google search, facebook or amazon deny their services, for example.
Let us elaborate upon a protocol using the above principles of cryptoeconomic mechanism designing to dis-incentivize the attack.
Protocol Goal: Alice requests a Web site from Bob’s server. The desideratum is that Alice or any other party does not exhaust Bob’s server.
Protocol Setup: Alice and Bob are in possession of a Wallet address and thus are able to transact tokens. Further we assume a staking smart contract associated with Bob. As a collateral, Bob has staked the contract with a sufficiently amount of tokens, say quadratic to the number of users expected to visit the server.
Protocol: The protocol runs between Alice and Bob in parallel on the Blockchain and application layer as follows:
Sub-protocol running on the Blockchain layer (e.g. Ethereum)
- Alice deposits a stake by calling Bob’s staking contract. (One could imagine to extend the DNS protocol not only to provide Bob’s IP address, but also the id of Bob’s staking smart contract.)
- The staking results in a transaction identifiable through some transaction id. Typically it is the hash over the transaction and as the transaction comprises some random values we may assume the transaction id is a sufficiently good random number.
Sub-protocol running on the application layer
- Alice sends an HTTP request to Bob by adding to the URL a variable containing Alice’s transaction id.
- Upon reception of the HTTP request, Bob parses from the URL Alice’s transaction id.
Sub-protocol running on the Blockchain layer (e.g. Ethereum)
- Bob verifies that the transaction is within the last n blocks of the Blockchain. If the transaction is not within the blocks, it aborts. (Here the idea is to use the block generation as a clock to timestamp the transaction).
- Bob unlocks the stake after n blocks in case it has not encountered a denial-of-service attack.
Sub-protocol running on the application layer
- If the transaction id is valid, Bob grants Alice access to the desired resource. Otherwise, it rejects Alice’s request.
Analyzing the above protocol, Alice is disincentivized to exploit Bob’s server as it directly leads to the loss of her stake. The above protocol may need also a mechanism to incentivize Bob to unlock Alice’s stake in case of good behavior. We can leverage the previously described voting scheme to challenge Bob. Validators challenge Bob by scrutinizing the Blockchain for transactions made to the staking contract and transactions unlocking the stake. Here again the Blockchain comes to help as it records an immutable history of the transactions and gives validators valuable information to participate in the voting process.
4. Unveiling the Power of Blockchains — How do Cryptoeconomic Mechanisms enable new Business Applications
One of the cardinal questions is why should a Blockchain incentivized Internet protocol or application work? The answer is quite simple. If incentive mechanisms work to educate our kids and a whole society, they work also in the digital world. Incentive mechanisms are in our genes, they are part of our culture, and a proven strategy of our evolution.
If cryptoeconomic mechanism design offers new opportunities to re-design the Internet, how can we harness this gift in concrete applications and business models? Let me share some of my thoughts along some simple use cases:
- Quality-of-Data. Data is the new oil and has a value. The problem is that nowadays we cannot trust the origin of the data. Recall the issues with fake news on social media. In the same vein fake data is producible and it is hard to assess the truthfulness, making it merely infeasible to determine the true value. Now how can we incentivize data producers to harvest and supply high-quality data? Reward them for generating high-quality data, and punish them for disseminating fake data.
- Quality-of-Trading. Many services have commercial intentions. They offer some good, product or service and their business model builds upon exclusivity of that good. That’s why it is of utmost importance for the businesses to protect their exclusivity through patents, trademarks, etc. On the other hand, they face problems related to infringements and plagiarism that dump the value of their exclusive product. They deal with replication of their products and violations of patents and trademarks due to time and money consuming law suits. Now how do we incentive a digital economy to prevent this unfair behavior? Reward the generation of quality products and punish the attempt to imitate the same product.
- Quality-of-Delivery. Mobility is one of the key technologies that will dramatically change the way we receive our parcels today and the way we travel. Improvements go into the direction of abbreviating the time-of-delivery or the reduction of traffic jams and congestions. How can we incentivize punctual delivery? Simply reward delivery on time and punish delays.
While the above ideas are only food for thought and the implementation of theses incentive mechanisms would require to solve challenges like data and device identification, data attestation, infringement and plagiarism detection and verification, to name a few, it is clear that they add significant value to the existing products and services.
5. On Identities and a simple Blockchain-enabled Authentication HTTP Protocol
The de-facto identity on the Internet is the IP address. However, IP addresses provide the weakest form of identity as they may dynamically change. For the Internet infrastructure consisting of routers and servers a necessary property, but for end-users and Web applications a rather a cumbersome property which led to problems related to entity impersonation and identity theft. In fact, when one looks at recent cyberattacks, identity theft is among the top ranked Internet thefts these days. The Blockchain layer provides a unique identity (e.g. the Wallet address). It comes in the strongest form, namely a cryptographic proof of knowing a corresponding secret and public-key pair.
So how can we leverage the fact that thanks to the Blockchain layer every participant has unique identity and owns some cryptographic keys. Let’s design a simple blockchain-enabled authentication protocol on top of HTTP.
Protocol Goal: Alice wants to authenticate to Bob’s Web site. Bob is interested in her age to make sure she visits age-specific content.
Protocol Setup: Alice and Bob are in possession of a Wallet address (and thus a secret and public signing key). Further we assume an identity smart contract where Alice stores her name, age, etc. Given Alice’s address one can look up her name, her public key and all other information she deposited in the contract. In the same vein, Bob registers his address.
Interleaved Protocol: The protocol runs between Alice and Bob in parallel on the Blockchain and application layer as follows:
Sub-protocol running on the Blockchain layer (e.g. Ethereum)
- Alice looks up through the registry Bob’s address.
- Alice derives a nonce by computing a hash over the last n blocks of the Blockchain (let’s assume for now we derive this way a sufficiently random number)
- Alice concatenates the nonce with Bob’s address and signs the hash thereof
Sub-protocol running on the application layer
- Alice sends an HTTP request to Bob by adding to the URL a variable containing Alice’s address and the previously computed signature
- Upon reception of the HTTP request, Bob parses from the URL Alice’s address and signature
Sub-protocol running on the Blockchain layer (e.g. Ethereum)
- Bob retrieves from the registry smart contract Alice’s public-key, name and shipping address.
- Bob re-computes the nonce by hashing the last n blocks
Sub-protocol running on the application layer
- Bob verifies Alice’s signature with the retrieved public-key and nonce.
- If the verification fails, it aborts the transaction. Otherwise, Bob proceeds with the purchase using the provided shipping address
(Disclaimer: The above protocol serves only the purpose of demonstrating the versatility of the Blockchain layer. There are several other ways to achieve the above protocol goal. For example, Alice transacts a negligibly small amount to Bob and uses the transaction identifier as variable.)
Let’s compare the above protocol with standard approach HTTP over SSL (aka HTTPS).
- HTTPS requires the user to install an X.509 digital client certificate; the above protocol makes use of the fact that the Blockchain gives the user a cryptographic key pair. X.509 client certificate have not prevailed in practice due to their unease use. Hope is that future Blockchain clients and interfaces like metamask.io will remedy the usability problem.
- An X.509 client certificate follows a standard syntax and the input fields are limited; in the above protocol the smart contract defines the syntax and gives the format for the information Alice can deposit (e.g., name, age, shipping address). This gives much more flexibility.
- HTTPS is a complex security protocol with a high latency on mobile networks (have you ever wondered why HTTPS is so slow on your mobile device?). It comprises a key exchange and mechanisms to establish a confidential communication channel; the above protocol clearly does not provide a confidential communication, but it authenticates Alice with less communication rounds (to be precise, in a single round instead of five). Improvements in the communication rounds clearly lead to a lower latency and better user experience.
- For a stronger assurance of Alice’s identity information like her name, shipping address etc. the registry needs to verify the real identity of Alice. In which case, the registry contract effectively implements the function of a certificate authority. But we may also think of decentralized approaches to assess Alice’s identity. One idea is a cryptoeconomic reputation system. We incentivize Alice to curate over time (say through good transactions and participation with other services) a good reputation. With that reputation she obtains rewards (e.g. access to premium services, discounts). Loosing her reputation (because she provided false identities) may result in dropping her from the reputation system what effectively diminishes her privileges.
- The above protocol heavily depends on the throughput of the Blockchain network and its scalability, as it requires information for the application layer sub-protocol. Although the Blockchain sub-protocol “reads” only from the network, it may delay the actual HTTP protocol. As Blockchain technologies make significant progress to solve scalability issues, one may expect that Blockchain-intrinsic network delays will be solved in near future.
6. Conclusion
We have argued that the true advantages and benefits Blockchain offer have not been unveiled yet. Specifically the ability to design protocols and applications based on token-incentives shows that the Blockchain layer can bring novel opportunities to re-design the Internet. To demonstrate the plausibility of this hypotheses, we presented variants of the HTTP protocol. With help of the Blockchain layer, we showed a mechanism design to prevent denial-of-service. We also showed authentication over HTTP with help of the Blockchain layer.
Incentive strategies can help in many other promising domains, such as
- enforcement of governance
- curation of high-quality registries, reputation systems
- establishment of truthful data that can be commercializable through marketplaces
- assessing network stability by preventing the exploitation of network resources. In the next article, I will dive more into the new application domains. I will discuss how cryptoeconomics can help to stabilize networks, create high-quality markets and prevent infringement and plagiarism. These are key properties to the success of many vibrant business models.
Unveiling Blockchain’s full Potential was originally published in Hacker Noon on Medium, where people are continuing the conversation by highlighting and responding to this story.
Disclaimer
The views and opinions expressed in this article are solely those of the authors and do not reflect the views of Bitcoin Insider. Every investment and trading move involves risk - this is especially true for cryptocurrencies given their volatility. We strongly advise our readers to conduct their own research when making a decision.