Latest news about Bitcoin and all cryptocurrencies. Your daily crypto news habit.
Asymmetric cryptography, also known as public-key cryptography, is one of the key components of blockchain technology. This form of cryptography allows everyone to verify the integrity of transactions, protect funds from hackers and much more. But how does it work?
What is asymmetric cryptography?
To understand asymmetric cryptography it is important to first understand the meaning of cryptography.
Cryptography is a method of using advanced mathematical principles in storing and transmitting data in a particular form so that only those for whom it is intended can read and process it. Encryption is a key concept in cryptography — It is a process whereby a message is encoded in a format that cannot be read or understood by an eavesdropper. The technique is old and was first used by Caesar to encrypt his messages using Caesar cipher. A plain text from a user can be encrypted to a cipher text, then send through a communication channel and no eavesdropper can interfere with the plain text. When it reaches the receiver end, the cipher text is decrypted to the original plain text. — SSL2BUY
Asymmetric cryptography is one of these methods and is a more advanced version of symmetric cryptography, which we will explain first.
Symmetric cryptography
Symmetric cryptography is a ‘simple’ form of cryptography which uses a single key to encrypt and decrypt data. This key can be almost anything, ranging from a number to a word to a random string of characters. This key is then used to encrypt the data after which the data can get sent across a network safely. To decrypt the data the receiver needs the key (the same one that the sender used to encrypt the data).
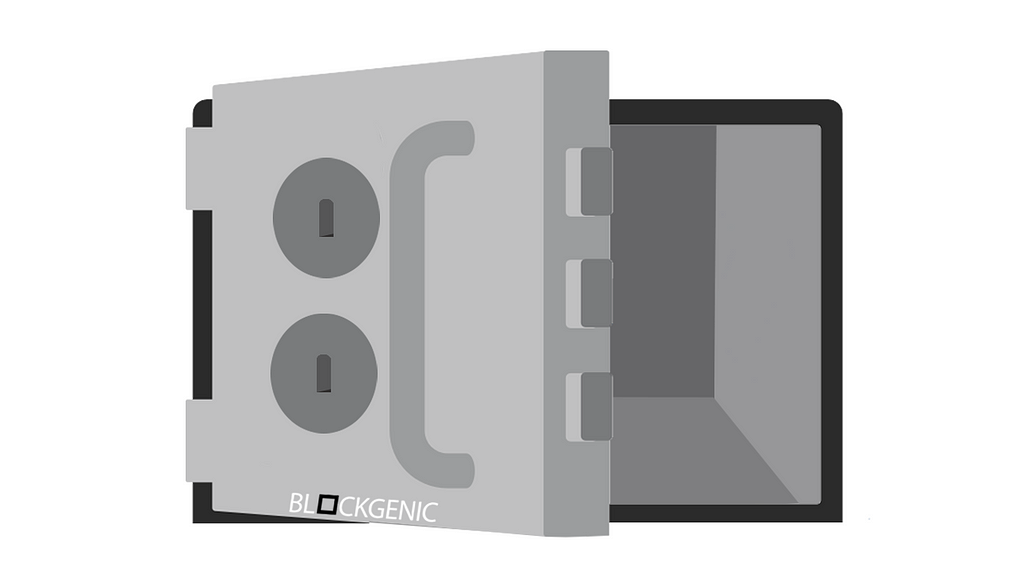
To get a better idea of how this works, we have created a visualization of the process below. First of all the sender encrypts a message with the shared key, the sender then sends the message without having to worry that anybody without the shared key is able to read the message. The receiver then receives the encrypted message and decrypts it (with the same shared key).
 Symmetric cryptography visualized
Symmetric cryptography visualized
The main downside of this cryptography method is that the key needs to be shared with everyone who needs to access the data, which can often be quite hard.
Asymmetric cryptography
Now you are familiar with symmetric cryptography, let’s dive into asymmetric cryptography. Asymmetric cryptography is similar to symmetric cryptography, but is a bit more complex and also has a solution to the main downside of symmetric cryptography.
The main distinction from symmetric cryptography is the usage of keypairs. Asymmetric cryptography uses keypairs, instead of a shared key, in order to encrypt and decrypt data.
Keypairs consist of 2 parts, a public key and a private key. A public key can be seen as a username, it is available to everyone, can be shared with everyone, and everyone can view the history of the account with that username. The username is tied to a password (private key), but there is absolutely no way to derive the password (private key) from a username. It is also not possible to authorize any action on the account with just the username.A private key can be seen as a password to an account with a certain username. It is not publicly available and should not be shared with anyone. The private key is used to authorize actions on the accounts. Unlike with ‘normal accounts’, to access the account, or to authorize any action on the account, only the private key is needed.
In the graphic below you can see how these keys work in practice, when sending a message to somebody securely. First of all the sender encrypts the message with the public key of the receiver, the sender can then send the (encrypted) message safely, as the only way to view the message is to decrypt it with the corresponding private key which only the receiver has. The receiver then receives the message and is able to decrypt it using the private key.
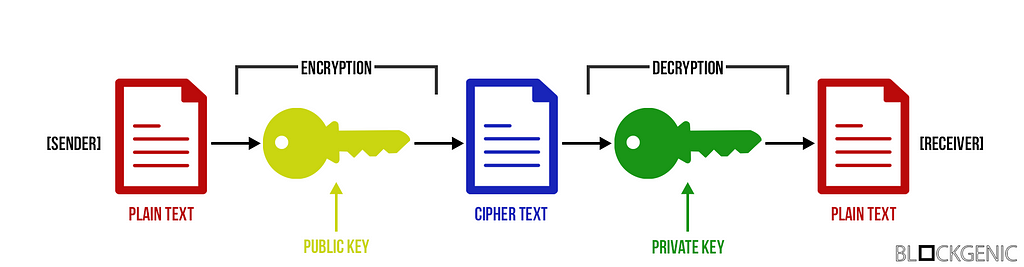 Asymmetric cryptography visualized
Asymmetric cryptography visualized
Due to the usage of keypairs asymmetric cryptography is a (much) safer way to encrypt data and make sure only those who are supposed to receive it are able to receive it. These keypairs also allow themselves to be used for authentication purposes, which we will talk more about below.
Digital signatures
Digital signatures are essentially signatures that provide integrity using asymmetric cryptography. They are widely used in many protocols for authentication purposes and have already proven to be both very useful and secure.
Digital signatures are incorruptible and easily verifiable thanks to their usage of asymmetric cryptography. Since they use asymmetric cryptography (and a private key is only linked to a single person) digital signatures also have the quality of non-repudiation, meaning they can be as legally binding as a normal signature. But how can you verify the integrity of certain messages, or how could you ensure others are able to verify the integrity of your message?
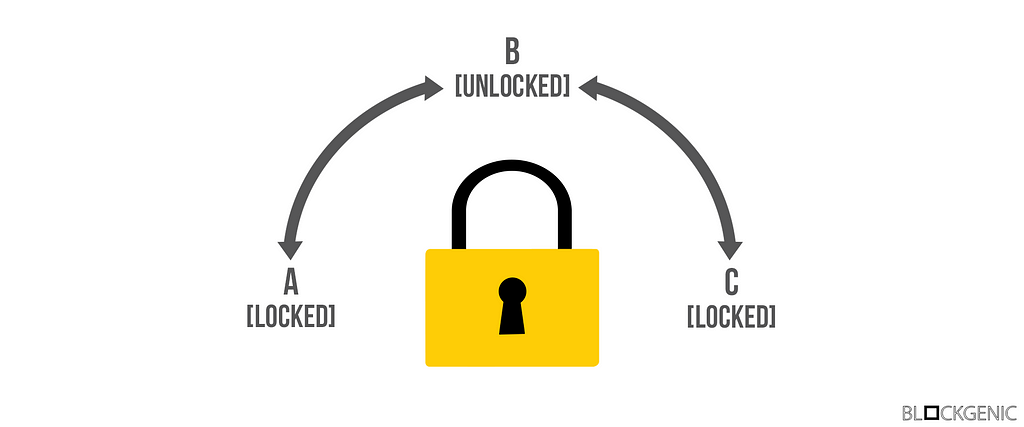 Public and private key functionality visualized
Public and private key functionality visualized
The answer to these questions is rather simple and can be explained with the image above. The lock in the image above has 2 keys, the public key, which can only turn counterclockwise, and a private key, which can only turn clockwise. We assume the public key of each lock is widely available.
Let’s say Alice wants to send an unencrypted message to Bob, but Bob wants to ensure Alice has sent the message. Alice puts the message in a box and then puts the lock on the box. She then locks the lock using her own private key (from B to C). After locking the box she sends it to Bob. Bob then receives the box and can verify the integrity (and sender) of the message using Alice’s public key. If Alice’s public key does not open the box the integrity of the message and box should be considered violated.
If you encrypt (“lock”) something with your private key, anyone can decrypt it (“unlock”), but this serves as a proof you encrypted it: it’s “digitally signed” by you. — Panayotis Vryonis
If Alice wants to send an encrypted message to Bob, and only Bob should be able to both decrypt the message and verify the identity of the sender, she would have to take some extra steps. First of all Alice puts the message in a box and puts a lock on the box, she then locks the box using her own private key (from B to C). She then puts the (locked) box in a new box and puts a new lock on the box. She locks the new lock using Bob’s public key (from B to A). After Alice is done she sends the box to Bob. Once Bob receives the box he can open the outer box with his private key, he can then open the inner box with Alice’s public key. If the inner box can not be opened with Alice’s public key the the integrity of the message and box should, yet again, be considered violated.
These ‘locks’ are called digital signatures.
Note that in reality both a signature generation algorithm, which takes a key and data, and a signature verification algorithm, which takes a message and signature, are needed to do the things explained above.
The usage in blockchains
While both asymmetric cryptography and digital signatures have been popular ever since they were invented, they are probably most known for their implementations in blockchains. Since blockchains are essentially widely distributed ledgers, it is of the essence that the cryptography used is both reliable and functional.
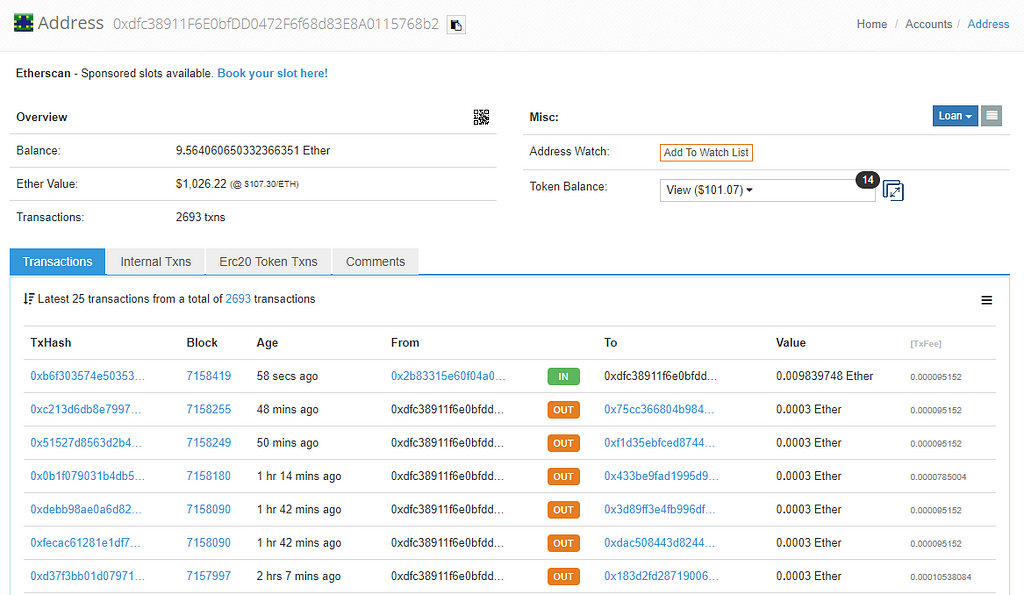
Most cryptocurrencies use keypairs (and thus asymmetric cryptography) to manage ‘addresses’ on the blockchain. The public key is the address, which ‘holds’ the tokens and it can be viewed by anyone. The private key is used to access the address and authorize actions for the ‘address’. Below is an example of an arbitrary address on the Ethereum blockchain.
Digital signatures are also widely used in cryptocurrencies. They can be used to sign transactions more safely (offline) and are also used in multisignature contracts and wallets. These multisignature contracts and wallets require digital signatures from multiple (different) private keys before any action can be executed. For a more detailed explanation read this article.
These examples are just the tip of the iceberg though, as asymmetric cryptography has many more uses in blockchains, ranging from implementations in simple smart contracts to advanced permission structures, with many more exciting developments on the horizon.
About us
We are Blockgenic, a network of world class technology entrepreneurs and investors looking to make a positive impact on blockchain technology. You can find us here:EOS Block Producer name: ‘blockgenicbp’WebsiteTwitterYoutube Reddit
Asymmetric Cryptography In Blockchains was originally published in Hacker Noon on Medium, where people are continuing the conversation by highlighting and responding to this story.
Disclaimer
The views and opinions expressed in this article are solely those of the authors and do not reflect the views of Bitcoin Insider. Every investment and trading move involves risk - this is especially true for cryptocurrencies given their volatility. We strongly advise our readers to conduct their own research when making a decision.