Latest news about Bitcoin and all cryptocurrencies. Your daily crypto news habit.
Time for New Crypto Security Models
By Kris Coward, Chief Scientist at Shyft Network
Are decentralized systems inherently vulnerable to 51% attacks? The recent successful 51% attack against the Ethereum Classic (ETC) network showcases the limits of decentralization and flaws in the current processes of securing digital assets and hints at the ways these risks can be mitigated.
The Ethereum Classic 51% attack (and what it means)
The state of the market, also known as ‘crypto winter’ has had a chilling effect on the industry. In addition to bringing down the prices and eroding margins, the market affected the hash rate required to mine the more secure, POW-based tokens. Since Ethereum mining infrastructure can also be used to mine ETC, it ended up presenting a particularly attractive target for potential attackers. And so it got attacked.
Since ETC exists because of the DAO hack, there’s a certain poetic irony to it being targeted. The DAO (“Decentralized Autonomous Organization”) was groundbreaking but ultimately a flawed attempt to found an entirely new model of totally decentralized governance, and it was built on Ethereum. When a hacker successfully compromised The DAO due to security flaws, the Ethereum community had a choice: roll back the chain to make investors whole again, or accept that the theft occurred and respect the sanctity of the ledger. ETC was the result of the latter camp forking off.
We’ve now seen two fairly cutting-edge networks brought down at least in part by the same principle: “the more decentralized a technology is, the better and freer it is.” Ultimately, that freedom comes with an expensive set of risks that might not be worth the price of admission.
The internet is a dangerous place — and everyone knows it
The same principle applies to any conventional proof-of-work based cryptocurrency; ETC is no exception. There’s no requirement to raise 51% hash power to successfully perform a “51% attack”. Related attacks have been demonstrated using as little as 25% of a POW network’s collective hash power to successfully subvert enough blocks to confirm invalid blocks (note that while these attacks are technically feasible, they’re generally not considered economically viable). The relatively recent advent of rentable computing power via services like NiceHash makes 51% attacks even easier — no more need to rig up an expensive fraud engine at home or the office.
There’s a perfect storm effect at work here: more and more users who either don’t know how to secure their data online or don’t have faith in the tools at their disposal; malicious actors online with increasingly sophisticated and inexpensive means to subvert even sophisticated networks, and an increasingly networked world in which more and more services are coming online.
Information security is a serious concern
For both the crypto world and the broader online ecosystem, current solutions are simply not good enough. The security apparatuses and conventions are not keeping pace.
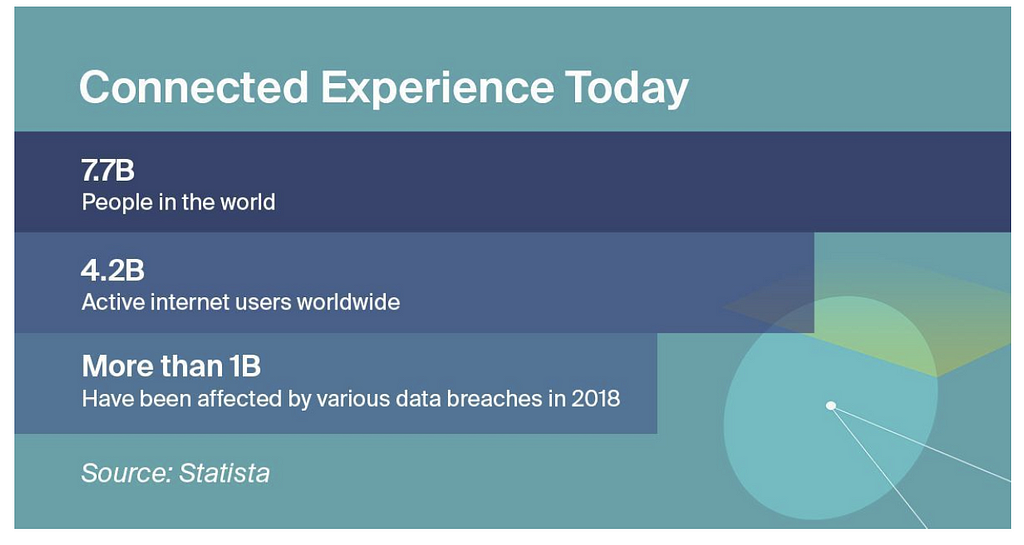
The importance of data security and privacy means we need to think beyond “decentralized everything” and come up with solutions flexible enough to solve for many diverse use cases. Just recently, the World Economic Forum released research showing that the percentage of users who take active measures to protect themselves online is dismal, even while the vast majority acknowledge that information security is a serious concern.
It’s clear that people need better tools to protect and manage their data.
We’ve seen more major data breaches, including the compromise of personal data for essentially the entire German political class. Last March, a breach in India’s ID database exposed biometric information on over 1.1 billion citizens. Another half a billion had their personal information made available to hackers thanks to lax security infrastructure at Marriott hotels. That’s just three major incidents. New major headlines keep coming with distressing regularity.
A more comprehensive solution for both crypto users and average internet users has to be some sort of compromise point between centralization and decentralization. In a blockchain context, this means networks that have some element of authority — whether it’s singular or federated — to be able to, for example, efficiently roll back blocks affected by an attack, or at least to increase the block confirmation threshold.
For example, through an attestation flow that leverages trusted entities, a blockchain network would allow users to attest to their token ownership without exposing their specific identity to the blockchain and introducing further risk. In case of theft or loss of access to private keys, users could then issue a “stop” order to the network to ensure that no funds can be moved until they’re sure the coast is clear.
Relying on existing roadmaps and Improvement Protocols alone won’t suffice. We need to ensure that cryptography and technology that is built to leverage it, like blockchain, can work for everyone.
Usability matters: How cryptography can be made accessible for everyone
For blockchain technology to deliver on its potential, it should be able to reproduce some of the basic usability elements and conveniences people have come to expect from technology, while still leveraging the advantages offered by cryptographic keypair architecture and distributed systems. In other words, lost keys shouldn’t lead to panic and forever-lost funds; attestations on the network should have revocability elements, and there’s a need for a more centralized middle layer to manage keys and attestations. In other words, we can’t expect users to be their own banks, and perhaps not everything needs to be decentralized all of the time.
Security mechanisms and systems that make it easy for regular people to manage and protect their data could be the key to mass adoption.
========================================
Kris Coward is the Chief Scientist of Shyft Network. His journey began in the 90s as a teenage hacker, followed by extensive experience in academia and the corporate world. At Shyft, he combines his technical skills with a keen interest in cryptography, security, and privacy.
Learn more at Shyft.Network or talk to us on Telegram.
Time for new security models in crypto was originally published in Hacker Noon on Medium, where people are continuing the conversation by highlighting and responding to this story.
Disclaimer
The views and opinions expressed in this article are solely those of the authors and do not reflect the views of Bitcoin Insider. Every investment and trading move involves risk - this is especially true for cryptocurrencies given their volatility. We strongly advise our readers to conduct their own research when making a decision.