Latest news about Bitcoin and all cryptocurrencies. Your daily crypto news habit.
 Jordan Belfort throwing out money made from “penny stocks” in the movie ‘Wolf of Wall Street’
Jordan Belfort throwing out money made from “penny stocks” in the movie ‘Wolf of Wall Street’
On a global level, we are currently exploring the vast implications of the forthcoming security token industry. Security tokens are expected to disrupt finance and access to capital because companies and start-ups will be empowered to turn to the crowd for funding.
While building the ecosystem, together with other companies in the Netherlands, I stumbled upon a particular exception in Dutch law. Many issuers could leverage this exception in the near future, which is very good according to some and very bad according to others.
In this post, I will shed lights on both perspectives, but before we dive in, you need a little bit of corporate and legal context.
Creating freely exchangeable security tokens
Two of the most significant value-adds security tokens offer in comparison to ‘normal securities’ are the so-called liquidity and market depth.
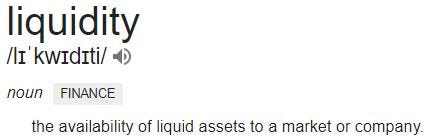
 Definition by Investopedia
Definition by Investopedia
Naturally, you would want to leverage these aspects of security tokens as an issuer because it gives a lot of value to your investors and therefore makes it easier for you to raise funds.
Imagine you own a Limited Liability Company (LLC), incorporated in the Netherlands and you would like to sell some equity in order to grow your LLC (in the Netherlands it is called a B.V.). You are allowed to offer shares of the B.V. to the general public, but these shares are only freely transferable via a notarial deed. This means that tokenizing shares of a B.V. directly does not provide the liquidity and market depth which make security tokens so valuable. You would be able to offer and sell your tokens though, but these will not be freely tradeable on exchanges after your offering.
As often frequent in corporate law, you can utilize other legal structures which will grant you the rights to achieve your goal: the issuance of a super liquid security token.
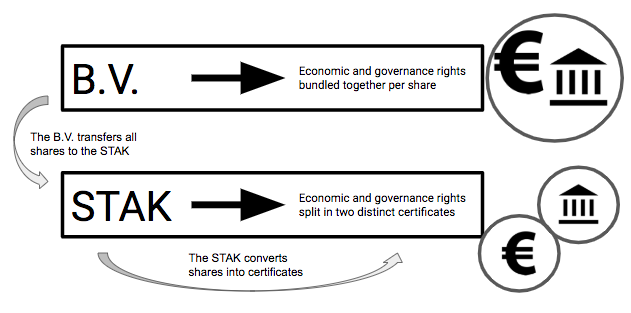
A ‘Stichting administratiekantoor’ (STAK) is a legal form (foundation) which is not attractive to entrepreneurs in the first place, because of the many legal requirements attached to it. The STAK is a legal construction that splits economic and governance rights of a share. So, if you transfer all the shares of your B.V. to the STAK, the STAK can create two types of certificates: one with governance rights and one with economic rights — see the image below:
Using the STAK to convert your shares into two distinct certificates is valuable for three reasons:
- Certificates that represent economic ownership are freely tradable without notarial deed.
- Economic ownership certificates can also include rights to profit.
- The certificates effectively split economic rights from governance rights, allowing the issuer to keep control of the direction of the company while sharing the economic rights with the crowd.
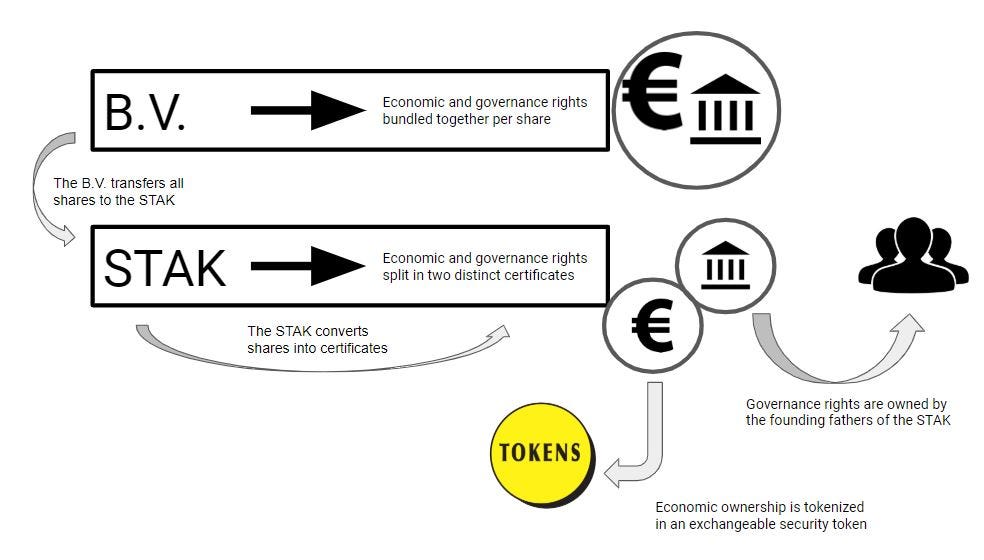
The next step is to tokenize the economic ownership certificates:
You transfer the shares of your B.V. to a STAK, convert your shares into certificates, and you tokenize them. This will provide your investors with a freely tradeable token that represents real value in your company.
So far, so good right? Nothing exceptional about this process.
Before you may start offering these tokens to the public, you must be certain that the tokens are owned by “legit owners”. This is why KYC and AML procedures exist.
Security tokens and KYC and AML compliance
Know Your Customer (KYC) and Anti-Money Laundering procedures are made to prevent bad actors, such as criminals and terrorists, from making their illegally gained proceedings appear legal or financing their malicious acts.
Security issuers must therefore always be aware of those who own their security and where their financial means come from — This applies to roughly every jurisdiction globally.
Similarly, security token issuers must have a whitelist of “KYC and AML compliant” people, and entities that are allowed to own their security tokens.
This is where it comes…
Owners of certificates, issued by the STAK, do not have to be identified…
In other words, KYC and AML procedures do not apply to the people buying, owning or trading security tokens that represent the economic ownership certificates we discussed earlier.
Legally, the KYC and AML procedures already took place when the shares were transferred from the B.V. to the STAK: In that process, the B.V. must be aware of who the owners of the STAK are and where they get their money from.
When buying assets, like shares in a BV, you must be registered at the Dutch chamber of commerce. Contrarily, you can buy certificates from a STAK, anonymously, without registering at the Dutch chamber of commerce.
The owners of the STAK may decide what suffices as KYC and AML procedures for the owners of their certificates. This could be similar to “regular” KYC and AML procedures, but the owners can also decide that solely a name and e-mail address suffice, thereby enabling issuers to make the process of acquiring a security token as convenient as possible. One could argue that this is good because it fosters the adoption of the security token industry. However, one could also say that this leads to shady processes and scams as we have seen in the early days of ICOs.
One loophole — Two perspectives
To publish this post, I was particularly inspired, by a short discussion that occurred at a security token event in Eindhoven, the Netherlands. Two individuals who are both engaged in providing pre- and post-STO services shared their distinct visions on the matter.
In short:
Herman Vissia, CEO/founder of Byelex, is in favor of the ability of STAK owners to determine their own KYC and AML rules. He argues that an issuer should not be bothered by laws that would unnecessarily toughen the process of acquiring a security token. He believes that adoption is essential to the security token industry in the first place. Finally, he argues that many KYC and AML procedures are based on a lot of paranoia caused by the media and the way they represent the news about terrorists and criminals, for instance. He estimates the chance of a malicious actor buying in on security tokens negligible. Herman says this applies to investments below €15.000 If an issuer is accepting more than that amount, he should perform thorough KYC and AML procedures.
Mohan Rao, CEO/co-founder of KRG and project lead at tokenise.eu, argues that companies involved in STOs should be focused on being the best, rather than being the first. He believes that rushing for adoption now, will yield bad results in the future. Even if the chance of malicious actors investing in security tokens is negligible, we should not allow it. We are currently on the verge of getting regulatory buy-ins on the formation of this new industry. If we rush now, by using sketchy loopholes in the law, we stand a chance of messing it up for all the issuers to come in the future. We do not want to replay the saga of scams and junky projects we have seen in the ICO era.
Conclusion
For as far as you are concerned, I agree with the latter argument that states we should not rush to adoption while neglecting a solid legal foundation.
I do believe that there is still a lot for us “security token fanatics” to figure out. I imagine there are many more national jurisdictions that provide unique conditions for this new industry.
Fact is that:
Many of these loopholes have never been prominent, because there was never a way to make assets as liquid as now, via security tokens and blockchain technology.
I am curious to see how this and many other instances worldwide will evolve and I would be happy to discuss and explore the possible scenarios together. Feel free to connect with me on Linkedin or Telegram: @adriaan_vmc.
Security tokens and the loophole in corporate law was originally published in Hacker Noon on Medium, where people are continuing the conversation by highlighting and responding to this story.
Disclaimer
The views and opinions expressed in this article are solely those of the authors and do not reflect the views of Bitcoin Insider. Every investment and trading move involves risk - this is especially true for cryptocurrencies given their volatility. We strongly advise our readers to conduct their own research when making a decision.