Latest news about Bitcoin and all cryptocurrencies. Your daily crypto news habit.
Technology is a rapidly evolving field, with new changes coming in at a very fast pace, and digital security as a subset of that field is growing even faster. It makes sense too — we’re putting more and more of our lives in the hands of machines, many of which are highly vulnerable to various kinds of attacks that sometimes don’t even get discovered for a very long time.
The situation can only get worse unless we take matters into our own hands, and it’s important to stay aware of the various new trends in the field of security, such as zero trust security, something that’s been a hot topic lately.
What Is Zero Trust Security?
It wasn’t that long ago that we used to treat our digital devices with a high sense of trust, assuming that as long as data and processes remained in a closed cycle, nothing could get compromised. We didn’t need memory protection, because it was assumed that no application would try to mess with the memory of another. A device on a closed network didn’t verify the data and commands coming in from other devices, as it was assumed that nobody else could get on that network and start communicating.
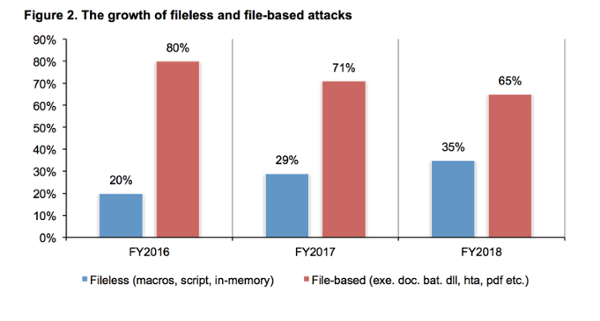
But now, things are very different. Internal attacks have become a common attack vector for many hackers, and we’re only seeing the tip of the iceberg. Zero trust strategies simply add an extra barrier of security in places where it wasn’t present before, such as requiring every bit of data and every transmitted and received a command to be verified and sanitized before being processed.
Benefits
The most obvious benefit of zero trust security is that you’re relieving yourself of a huge portion of the responsibility with regards to maintaining the different relationships between devices and other elements in the security group. This makes it easier for administrators to go about their duties too, as they won’t need to manually sanitize the data they’ve received from various sources.
When applied in a consistent manner, this can become a very effective underlying strategy for the overall security of your organization, no matter how large it may be. Every new device or element that gets added later on will have to comply with your zero trust policies, meaning that they will automatically be more secure.
Implementation Guidelines
There are various ways to implement zero trust security in your operations, and many of them are largely dependent on the specifics of your systems. Sanitizing data at every step should be one of your top priorities — don’t just assume that information is going to arrive in the correct format because it’s been sent from a “trusted” device. That’s how injection attacks and other similar problems occur, and it may take you a long time before you’ve even noticed that something is wrong, if the ones attacking you are clever enough about concealing their tracks.
You should also run occasional tests that mask the source of various kinds of data to see how your networks will react. A proper residential proxy can be an invaluable tool in these kinds of tests, as it can allow you to mask the origin of a connection to see what kind of response you’re going to get from the network or devices. It’s important to ensure that you’re using residential proxies whenever possible though, as regular commercial ones may be flagged by more advanced attacking tools and may compromise the results of your tests.
Future Developments
It’s hard to tell where this will all end up in the future, but one thing is certain — the notion of trusting devices and actors by default is fading away very quickly, and it’s likely going to be a distant memory not too long from now. Security experts keep exploring various approaches to general security practices that are supposed to make the situation more stable for everyone, without complicating the nature of their own work, but that’s a fine line to tread and it requires a lot of expertise to come up with viable plans.
Those who are worried about having to make major changes to their own systems shouldn’t be on an edge though. Chances are, these kinds of changes are going to be introduced gradually and over multiple revisions, both in terms of software and hardware. Staying compliant with common zero trust practices isn’t that difficult if you just keep an eye on new developments in that field, and there is plenty of information online about the current state of this part of security. Not to mention, if you’re confident with your knowledge of digital security yourself, and have come up with a more innovative strategy for tackling trust issues within your network, you can easily share what you’ve learned and contribute to those developments. That’s how we’ve reached this state in the first place, after all.
Zero Trust Security Strategies: Is This a Rising Trend? was originally published in Hacker Noon on Medium, where people are continuing the conversation by highlighting and responding to this story.
Disclaimer
The views and opinions expressed in this article are solely those of the authors and do not reflect the views of Bitcoin Insider. Every investment and trading move involves risk - this is especially true for cryptocurrencies given their volatility. We strongly advise our readers to conduct their own research when making a decision.
