Latest news about Bitcoin and all cryptocurrencies. Your daily crypto news habit.

This past June news.Bitcoin.com reported on a demonstration that took place at the world famous hacker conference in Las Vegas, Def Con 25, which claimed to show the audience how to break a bitcoin hardware wallet. Now according to a recent blog post, the presentation revealed to attendees found glitches in a Trezor that revealed a user’s private keys.
Also read: Bitcoin Cash 8MB Block Clears Over 37,000 Transactions
Trezor Releases New Firmware for a Security Vulnerability Revealed by ‘Responsible Disclosure’
 Hardware wallet owners got shook up this week when the company Satoshi Labs published a “Firmware Security Update” which stated a vulnerability was found which affected all models. However, the blog post was rather cryptic and stated the security issue was brought to the startup’s attention through “responsible disclosure.” The firmware is optional says the announcement, but the company recommends all users update their devices. Further, the vulnerability can only be executed if an attacker has possession of the hardware wallet and time to disassemble the Trezor.
Hardware wallet owners got shook up this week when the company Satoshi Labs published a “Firmware Security Update” which stated a vulnerability was found which affected all models. However, the blog post was rather cryptic and stated the security issue was brought to the startup’s attention through “responsible disclosure.” The firmware is optional says the announcement, but the company recommends all users update their devices. Further, the vulnerability can only be executed if an attacker has possession of the hardware wallet and time to disassemble the Trezor.
“It is important to note that this is not a remote execution attack,” explains the Trezor manufacturer Satoshi Labs. “To exploit this issue, an attacker would need physical access to a disassembled Trezor device with uncovered electronics. It is impossible to do this without destroying the plastic case.”
If your device does not leave your presence, your coins are safe. Moreover, if you have a passphrase enabled and actively use it, your coins are safe. Yet, we strongly recommend you to update your Trezor anyway.
An Alleged ‘Fifteen Second Hack’ Reveals Private Keys With No PIN Necessary
Following the announcement from Satoshi Labs, a report posted to Medium gives full details to how a Trezor can be exploited. The author explains that the Def Con 25 demonstration revealed that these attacks are possible because “Trezor is using non-secure chips made by STMicroelectronics.” The post details that this hack is so easy it can be done in 15 seconds, and if your device is stolen attackers have ample time to empty the hardware wallet.
“There is absolutely nothing that Trezor can do about it,” explains the Medium post. “They can’t replace all existing hardware. And the really bad news is that this also applies to Keepkey and to the upcoming Trezor v2 — it also uses similar STMicroelectronics chip!”
Is the ST32F05 vulnerable to fault injection? Absolutely, yes! — that’s the answer we got at Def Con 25. So, the ST32F05 chip is really doomed.
The post then describes a detailed walkthrough with pictures of how a Trezor can be attacked. The demonstration sets up a new device and creates a longer nine digit PIN, but the author details there is “no need to remember the PIN anyway.” Then the attacker shuts the device down and “simply connects two pins inside the Trezor device at the right time”, or to make it a lot easier they can disassemble the device but “no disassembly is required.” When this is done a scan, using firmware they created and that can be found in the post, reveals a Trezor’s entire seed phrase, the PIN, and the name of the device.
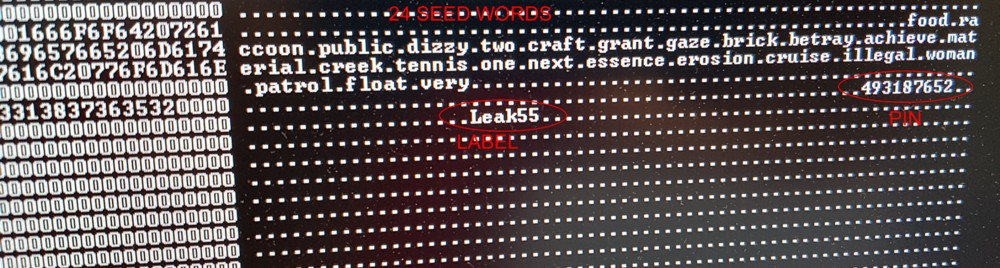 The attacker’s screenshot of an alleged attack that shows the device name, PIN, and 24-word seed.
The attacker’s screenshot of an alleged attack that shows the device name, PIN, and 24-word seed.
Satoshi Labs: ‘This Attack Vector Was Fixed in Firmware 1.5.2 — We Are Inclined to Call This Article FUD’
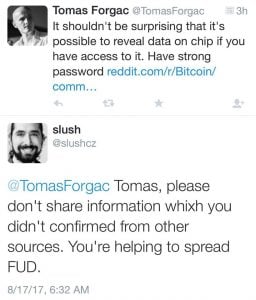 Satoshi Labs CEO Marek Palatinus (Slush) calling the article “FUD.”
Satoshi Labs CEO Marek Palatinus (Slush) calling the article “FUD.”
The author of the post explains that as soon as a hardware wallet is connected to a power source, without entering the PIN, the device firmware loads up its SRAMN with the device’s private key data. “Even more troublesome is the fact that during the firmware update, the bootloader is doing exactly the same thing! This goes against all security best practices that we know about,” explains the post.
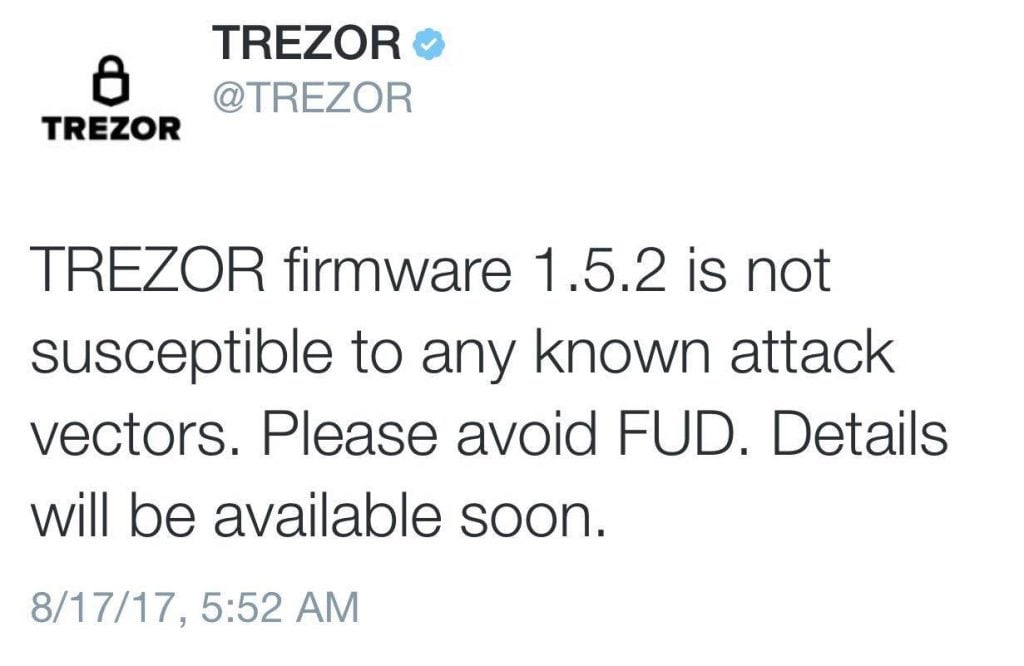
Trezor has announced that its latest firmware 1.5.2 removes the vulnerability and believes the article published is primarily the spreading of fear, uncertainty, and doubt (FUD). An employee of Trezor, called, ‘Xbach,’ who often gives people support on Reddit confirmed the post was a bit exaggerated.
“This attack vector was fixed in firmware 1.5.2,” explains the Trezor employee Xbach. “The claims in the post are not 100% correct. While it is true that this vulnerability affects devices with firmware versions earlier than 1.5.2, it was fixed in the latest update. Moreover, an attacker would need more than 15 seconds: they need to be physically present and a special firmware.”
We will go into depth in a report, which we will release later. As of this moment, we are inclined to call this article FUD. The fact that one needs to pay for source does not increase its credibility.
‘An Odd Way of Releasing an Alleged Hack’
Trezor’s official Twitter page also states that the news is “FUD,” alongside Satoshi Lab’s CEO & IT Architect, Marek Palatinus (Slush). The company’s representative, Xbach says the post was an “odd way how to release an alleged hack.” Further, he states the post skips much of the attack process and also mentions “Def Con, which is unrelated to this vulnerability,” explains Xbach.
“If there is really such a hack, then they could have contacted us, we have Responsible Disclosure and a reward system,” adds the Trezor representative.
What do you think about the alleged hack that accesses hardware wallet private keys? Let us know what you think in the comments below.
Images via Shutterstock, Medium, and Twitter.
Do you like to research and read about Bitcoin technology? Check out Bitcoin.com’s Wiki page for an in-depth look at Bitcoin’s innovative technology and interesting history.
The post Trezor Calls an Article That Claims to Break Bitcoin Hardware Wallets “FUD” appeared first on Bitcoin News.
Disclaimer
The views and opinions expressed in this article are solely those of the authors and do not reflect the views of Bitcoin Insider. Every investment and trading move involves risk - this is especially true for cryptocurrencies given their volatility. We strongly advise our readers to conduct their own research when making a decision.
