Latest news about Bitcoin and all cryptocurrencies. Your daily crypto news habit.
Outline
1. Why you should care about Cryptoeconomics2. Use cases and why we need Cryptoeconomics3. Social Contracts & Crypto4. Goals5. Security Models6. The Two Pillars of Cryptoeconomics7. Cryptographic Tools: hashes, digital signatures8. Economic Tools: tokens, block rewards, consensus mechanisms9. Possible Attacks 10. Summary11. Further readings
Why you should care about cryptoeconomics
We often imagine Bitcoin and other cryptocurrencies like the Wild Wild West: no rules, no social norms, only greed, selfishness and mining. This perceived lack of law and order makes the crypto world scary to many people. However, in reality, there are rules that govern decentralized peer-to-peer (p2p) networks such as Bitcoin. These rules are coded into protocols and deliver the framework for how participants of a network interact with each other. They help us create a secure, trustworthy and valuable system, just like laws deliver a framework for a better society. Cryptoeconomics asks the question of how we can design these rules and incentives, so that the networks stay secure and create value for everyone. Cryptoeconomics uses cryptographic tools, game theory and economic incentives to achieve this goal.
In order to understand how complex and valuable these decentralized p2p networks are we need to understand some basic cryptoeconomics behind them. If you have a better grasp of basic cryptoeconomics, you will understand why the emergence of cryptocurrencies is more than just hype.
Why I’m writing this
While both cryptography and economics are established academic subjects, cryptoeconomics is a new field. One could say it’s a little shy of 10 years old (since the inception of Bitcoin). Because it’s such an emerging field it is constantly evolving and there is no solid academic degree one could obtain in order to understand cryptoeconomics better. I’m writing this because I myself wanted to learn more about the design process of Bitcoin and other crypto networks. There are many great articles and even online courses, but it takes a while to go through them and piece the information together, so I wrote an intro for myself and for you. I’ll link further reading recommendations below.
Why is cryptoeconomics so important, what are its use cases and why do we even need it?
Even if you have never heard the term “decentralized p2p network”, you’ve likely used one or at least heard of it in the form of former filesharing websites, like Napster or BitTorrent. Generally, they’re systems in which humans interact with each other and exchange value. Value can be anything we collectively deem valuable, like a material item or service. Most people would probably think of fiat currency as valuable because it is widely accepted as such and because we trust in its stability and longevity. Nowadays, even cryptocurrencies like bitcoin partly fulfill this role.
These systems are designed, much like our nation states, governments and democracies, by writing down and enforcing laws. Unlike our nation states, decentralized p2p networks are designed by writing code into protocols. Unlike our nation states, we put trust in the code rather than the government.
How we design these protocols influences how we interact with each other in these systems and thus how much value we can create and share. Ultimately cryptoeconomics lays the foundations for everything that happens in decentralized p2p networks.
When designing these protocols, we make certain assumptions and theorize about how the protocols will be used and how they might be misused. We try to use these assumptions to maximize the value of the system for its participants.
Social Contracts and Crypto

Imagine: we don’t have any rules in our society and everyone just does what they want. I think we can all agree that if you can kill or rob without consequences, our society wouldn’t function well. It’d be like The Purge every day. Thomas Hobbes described life in this so-called Original State of Nature as a “solitary, poor, nasty, brutish, and short” and then goes on to theorize about social contracts.
Just as in real life, we want our digital networks to provide value, security and help us thrive as a collective. So, the most basic goal of a decentralized p2p network is not only to add value but also with security and longevity. We want to maximize the security of our network, just like we want to do that in our nation state.
In nation states, security is granted through the state’s monopoly on violence through the police and army. This violence is used to keep security and thus to keep our society valuable to us (in theory at least…). For example, the state enforces laws through their ability to punish you, which is enabled through their ability to be violent towards you (e.g. put you in handcuffs or imprison you). So, by being part of your society you give up some power in order to work towards a better society. You do so because you trust that the government and system will indeed provide security and added-value versus being out on your own in the woods. Obviously, this is all theoretical because in reality most of us don’t actively decide that we want to live in a nation state, we are born into it. We also don’t explicitly consent to give up our rights and we don’t always trust our governments to protect us.
In the crypto world, programmed protocols enforce rules within decentralized p2p networks and therefore ensure value and security. In comparison to our larger nation states, the nice thing about decentralized p2p networks is that:
- Nobody can force you to participate.
- There is no central authority (like a government) who can misuse their monopoly of power (think about the horrid things corrupt and unethical governments have done, like genocide, slavery, discrimination.)
- There is no physical violence used to make participants stick to the rules.
- You trust in open-source code to provide you with security.
The question then arises, what rules and incentives help create and sustain a valuable and secure network? This is exactly the question cryptoeconomics tries to answer.
Now that we have laid the foundations for our understanding of why cryptoeconomics is important, why it exists and why you should care about it, let’s dive into the actual subject matter.
First, we need to understand the more specific goals that we are trying to achieve through cryptoeconomics.
Goals
On a very high level, the goals of a decentralized p2p digital network is to be safe and to provide value. In more concrete terms:
Things we want to encourage:
- Trusted execution (you can trust that your transaction will be executed)
- Open Access (everyone can access and read the code, nothing is locked away to be viewed by a privileged few)
- Fast Finality (transactions are executed quickly and irreversibly)
- Decentralized Control (there is no central authority which controls the protocol and the network)
- Inexpensiveness (encourages many transactions)
Things we want to avoid:
- Safety Failure (e.g. someone steals your tokens)
- Censorship (e.g. someone decides that a certain group of people should not be allowed to transact)
- Slow finality (opposite of fast finality)
- Centralized Control (opposite decentralized control)
- Expensiveness (duh)
On a deeper level, these goals can be achieved by the following:
- Convergence (one block goes on top of the other block and thus keeps the correct sequence in the blockchain)
- Data Availability (open access facilitates decentralization)
- Validity (each transaction is valid, helps avoid double-spending)
- Availability of the network to all, which is equal to censorship resistance
- Timestamping (which helps us determine block sequences, transaction validity and more)
- High performance under several cryptoeconomic security models
Security Models
The very last point, cryptoeconomic security models, is an important fundamental concept. These security models are fundamental to the design of decentralized p2p networks.
Security models are assumptions about the state of the network and its participants. They also more technical challenges that come with the decentralized nature of the network. Security models can speculate what percentage of participants are honest or whether they act individually, whether they can collude, or whether they can be bribed.
I’m not going to elaborate too much on them but here’s a basic overlook with further reading recommendations.
Byzantine Fault Tolerance: A decentralized network has Byzantine Fault Tolerance if it can function despite several failure modes described in the Byzantine General’s Problem (e.g. a certain percentage of participants are dishonest and a threat to the security of the system.) Read more about Byzantine Fault Tolerance in Georgios Konstantopoulos article here.
Uncoordinated Choice Model: An Uncoordinated Choice model assumes that participants make independent decisions and are smaller than a certain size.
In an Uncoordinated Choice Model, we can assume an Honest Majority Model in which no participant has more than 50% of the hashing power. Security is compromised when someone acquires more than 50% of the hashing power. This would enable them to fork the blockchain and include faulty transactions. (This 50% is more nuanced in reality.) The Honest Majority Model is a very optimistic assumption and thus not very resilient when facing the hardships of the real world.
More realistically, it has been proven that the Bitcoin blockchain’s security can be compromised if one attacker has a little more than only 1/3 of hashing power. (Read more about it in Emin Gün Sirer’s Cornell paper.)
In general, it is increasingly unrealistic to assume that there is no collusion at all and that security can be compromised through collusion.
Coordinated Choice Model: The opposite of the Uncoordinated Choice Model. It assumes that most or all actors are colluding through some agent or coalition.
Bribing Attacker Model: The Bribing Attacker Model assumes no coordination amongst network participants. They are bribed to make decisions individually that in the end compromise the network’s security as a total. Vitalik Buterin explains this further in this video around 20min24s.
As you can imagine, these models are the fundamental assumption behind the design of our network. If you assume an Honest Majority Model, you don’t need to take into account as many factors and possible attacks as when you assume a Coordinated Choice Model or Bribing Attacker model. I think we’re going to develop more and more of these with time.
The Two Pillars of Cryptoeconomics
As already mentioned above, cryptoeconomics splits into two pillars:
- Cryptography: techniques that keep messages secure
- Economic incentives: rules and rewards that encourage you to add value to the network
Cryptographic Tools
As mentioned above, cryptographic tools are techniques that keep messages secure and immutable. They are a vital part of Bitcoin and other blockchains and thus of cryptoeconomics. Some of the most basic cryptographic tools (called cryptographic primitives) are hash functions and digital signatures. I will lay out the basics of these two cryptographic primitives because they are so fundamental to blockchain.
Hash Functions
A hash function is a function that takes an input of any size x and gives you an output with a fixed size H(x). Bitcoin uses the hash function SHA-256, which was designed by the NSA on the basis of the Merkle-Damgard function.
It satisfies three important qualities:
- 1. Collision resistance: A hash function is collision resistant if it is hard to find two different inputs that would hash to the same output. That is, we want to avoid this: H(x) = H(y) while x≠ y.Without collision resistance, an attacker might be able to substitute one original message “a” with a fake one “b” if it produces the same hash H(a) = H(b).
- 2. Hiding: A hash function is hiding if there’s no feasible way to deduct the original input x in H(x). The problem is that if the input comes from a very small range, e.g. it’s one of two possible values, someone could just hash the two possible values and easily guess what the original input x was. So, if we can hide the input x by concatenating it with another input that is from a very large range, it is infeasible to find out x. H (r||x) is hiding where r is a random value.
- 3. Puzzle-friendliness: A hash function is puzzle-friendly if we know a random part of the input and we know the hash H(x), but it is hard to find the rest of the input. We have to try every possibility randomly to find the rest of the input. This property is necessary for Bitcoin mining — miners try to solve for cryptographic puzzles in order to decide the next block.
For more information about hash functions, you can read an easy-to-digest blog post by Hang Lu Su.
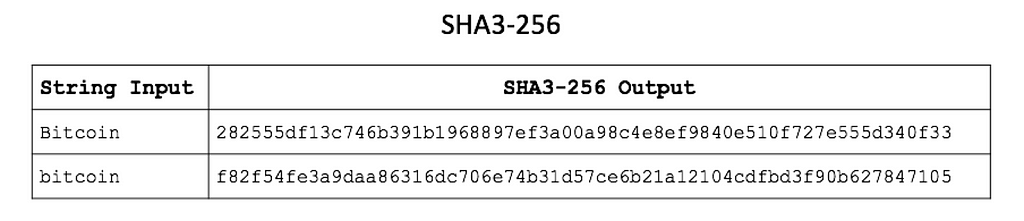 Notice how the smallest difference in the input string generates a completely different hash?Digital Signatures
Notice how the smallest difference in the input string generates a completely different hash?Digital Signatures
A digital signature mimics an analog handwritten signature. A signature binds our identity to a message (e.g. it shows that it is indeed me, Anami Nguyen, who has written a check in your favor). A digital signature has practically the same function in a decentralized p2p network. It helps us identify that certain messages (transactions) come indeed from a certain identity. A digital signature satisfies these three requirements:
1) Only you can make your signature. (Real life analogy: when I write my name down in a certain way, I hope that nobody can write it the same way.)
2) Anyone can verify your signature. (Real life analogy: a random bank employee should be able to verify that the signature is indeed from Anami Nguyen. If they are not able to do so, then the signature is practically useless.)
3) The signature is tied to a specific document. (Real life analogy: my signature can’t be cut off from the check I’ve written and pasted to another document.)
There are three algorithms that comprise a digital signature:
1. (sk, pk):=generateKeys(keysize)The generateKeys method takes a key size and generates a key pair:- sk is the secret key that you keep privately to sign messages. - pk is the public key that’s used to verify the signature by anyone.Application: The public key is your public identity (or, your address in Bitcoin). In order for someone to speak in the name of the identity pk, they must know the corresponding secret key, sk. It’s much like a username and password. That way we avoid that someone claims someone else’s identity and sends messages (and makes transactions) on their behalf.
2. sig := sign(sk, message) The sign method takes a message and a secret key, sk, as its input. Then it outputs a signature for message under sk.Application: As mentioned above, your signature should only be valid for a certain document. The sign method ensures that.
3. isValid := verify(pk, message, sig) The verify method takes a message, a signature, and a public key pk as its input. It returns a boolean value(true/false value), isValid, that will be true if sig is a valid signature for message under public key pk, and false otherwise.Application: this method combines the above components. Anyone should be able to verify whether a certain message (e.g. transaction) was indeed signed by your public key.
Therefore, a valid signature must show that: verify(pk, message, sig(sk, message))== true
For more detail on hash functions and digital signatures, check out Chapter 1 of Princeton’s Bitcoin book. There are further cryptographic tools that help us keep the blockchain secure but they would be beyond the scope of this article. If you are inclined to learn much more about cryptography, Stanford has a free online class Cryptography I.
Economic Tools
Now that we know more about some basic cryptographic tools, let’s get to the second part of cryptoeconomics. Economic tools are incentives that encourage and discourage certain behavior amongst network participants.
The most basic economic tool is the use of tokens and consensus mechanisms.
Tokens
Tokens are exchangeable goods within the decentralized p2p network. The most famous token in the crypto world is Bitcoin.
Beyond Bitcoin, tokens can be exchanged for a variety of goods and services. For example, you can rent out your excess CPU/GPU cycles via the Golem Network and get paid by the GNT (Golem Network Token) as a reward for your service. The presence of tokens creates a shared value amongst network participants, which makes decentralized p2p networks more like separate economies or ecosystems.
Now let’s see how tokens are used to incentivize desirable behavior in the Bitcoin network.
Block rewards
Let’s say you are a node that creates a new block to be included in the Bitcoin blockchain. You are rewarded for your work by being allowed to include a special transaction (coinbase transaction). This transaction allows you to send a block reward to your own address. Currently (June 2018) miners receive a block reward of 12.5 bitcoins. (The block reward decreases at a set rate, which you can explore here. I might write more about the whole deflation/inflation issue later, stay tuned!)
You will only be able to reap the reward if the new block is accepted by the rest of the network. Other nodes express their acceptance by including your new block’s hash in the next block they create. This incentivizes them to only include blocks with valid transactions. Because you believe they won’t accept your new block if you include faulty transactions, you are incentivized to include only valid transactions if you want the block reward.
Transaction fees
As I mentioned above, the block reward for creating new blocks decreases at a set rate, which means that there is a finite amount of bitcoins. But what incentivizes participants to continue building the Bitcoin blockchain and to execute transactions if they don’t get rewarded by being able to mine new bitcoin? Simple: they receive transaction fees for each transaction they include in their block.
Transaction fees also disincentivize participants from slowing down the network by sending transactions from and to their own accounts.
Consensus Mechanisms
Participants in a decentralized p2p network need to agree — they need to reach consensus — about the state of the network and about what blocks and transactions to include on the blockchain. We need a mechanism that helps eliminate issues that arise from decentralization and the possible presence of adversaries.
A consensus mechanism is a protocol on top of the blockchain that takes each node’s proposed block as an input and selects a valid block as an output.
Let’s take a look at Bitcoin’s Proof-of-Work consensus mechanism. Simply put, miners must expend a great amount of computational power to prove they have “skin in the game” and then they are allowed to propose a new block. They expend this computational power by solving hash puzzles that are based on the properties of hash functions I’ve mentioned earlier. I’m not going to dive into the technical details of these hash puzzles but you can read more on pages 64–67 of the Princeton Bitcoin book. From a cryptoeconomics perspective, it is important to note that miners must expense fiat currency to buy computing power (nowadays in the form of highly specialized and high-performance ASIC chips). With that, they have expensed significant resources that they would lose if their block wouldn’t be included on the blockchain.
Another popular consensus mechanism is Proof-of-stake. Generally, this consensus mechanism works by having a set of validators take turns proposing and voting on the next block, and the weight of each validator’s vote depends on the size of their staked deposit. They lose their stake if the block is not included in the blockchain and are therefore incentivized to vote on blocks that include only valid transactions. If you want to read more about Proof-of-Stake, I suggest perusing the writings of Vlad Zamfir and Vitalik Buterin, who are championing PoS for Ethereum (which currently runs on PoW).
Possible Attacks to the Network
What are attacks? An attack to the blockchain happens when someone threatens the security, credibility and worth of the blockchain by trying to include faulty transactions (e.g. double-spend transactions). Alternatively, someone could try to attack a blockchain out of pure malice or political reasons. I will give a brief overview of some hypothetical attacks to the Bitcoin blockchain.
51% attack (Honest Majority Level)
One of the most straightforward ways of enabling double-spend or faulty transactions is to fork the blockchain and then to include or exclude certain transactions. For this, nodes must accept the new block that includes faulty transactions and build on top of it. The forked chain must overtake the current chain by growing faster and becoming longer because nodes usually place new blocks on top of the longest blockchain. This attack can happen if someone has a majority — over 50% — of the hashing power. We assume the Bitcoin blockchain is secure because we assume an Honest Majority Model in which over 50% of participants are honest. It is the most well-known theoretical attack to the Bitcoin blockchain. There are many nuances to be considered in reality. For one, an attack might work even if the attacker has less than 50% of the hashing power.
Theoretically, an attacker who is purely after economic gain should be deterred from performing a 51% attack because the network value (Bitcoin/fiat exchange rate) would crash immediately after the attack. The attacker would basically shoot themselves in their own foot. However, someone might be motivated by ideological or political reasons to destroy the Bitcoin blockchain. Or, they could short Bitcoin and then launch the attack to profit from the Bitcoin crash. There are many other factors to consider and analyses to be made… unfortunately, they are outside of the scope of this article.
P+Epsilon Attack
The reality is that nobody who owns bitcoin should want the blockchain to be attacked because it would hurt them. However, a typical Tragedy of the Commons could occur if everyone acts on their own selfish incentives and accepts a bribe, which eventually leads to long term losses for all network participants. The Tragedy is that nobody wants to harm the network but it happens anyway.
In a P+ε Attack, someone can bribe network participants at no cost. Let’s say everyone needs to vote on whether 2+2=4 is true, so they’d vote Yes or No. Of course, the honest vote is Yes. If you vote like the majority of the participants, you receive a reward P. If your vote is in the minority, you receive 0. Everyone thinks that the other will vote Yes and therefore everyone votes Yes. We are experiencing a so-called Nash Equilibrium, in which everyone gets what they want.
However, imagine an attacker wants you to vote No. You’d be foolish to do so because everyone else will vote Yes, so your vote will be in the minority and you don’t gain reward P. However, the attacker commits credibly (e.g. via Ethereum contract) to pay you a reward worth P+ε (the original reward plus a little extra) if you vote No and if you’re in the minority. Suddenly, it is in your best interest to vote No: If you’re in the majority, you’ll win P and if you’re in the minority you’ll win P+ε. On the other hand, if you vote Yes, you’ll only win if you’re in the majority but you’ll lose if you’re in the minority. Now, because of the bribe, everyone will vote No. Suddenly, No-voters are in the majority and the attacker doesn’t even have to pay any No-voter because they’re in the majority.
In decentralized p2p networks that maintain a blockchain the vote concerns whether to include faulty transactions or not. Participants should not want to include faulty transactions or double-spends but might be bribed to do that.
You can check out some possible ways to mitigate this risk in Vitalik Buterin‘s blogpost.
Maybe you have noticed that most problems I have described can be of technical and/or economic nature. Problems that arise from rational human greed (e.g. Tragedy of the Commons) can be solved with cryptography. Byzantine Fault Tolerance, which is a technical issue, can be solved with economic incentives. I find this intersection of technology and economics particularly challenging and fascinating.
Summary
We’ve learned that cryptoeconomics is the backbone of decentralized p2p networks. Cryptoeconomics combines cryptography with economic incentives to keep the network secure and incentivize participation. We’ve learned that there are assumptions we make about the state of the world when designing crypto networks that are called security models (e.g. Uncoordinated Choice Model, Honest Majority Model, etc). Some of the most basic cryptographic concepts are hash functions and digital signatures, which help prevent security attacks amongst other functions. On the economic incentive side, we might use tokens and consensus mechanisms (like Proof-of-Work) to secure the network and to motivate participants to contribute to it, e.g. by spending USD on computational power to mine Bitcoin. There are many possibilities to attack a decentralized p2p network, like the 51% attack and the P+epsilon attack. As a new and basically non-academic field within the crypto community, cryptoeconomics is constantly evolving and depends on the theorizing and problem-solving skills of everyone in the crypto community. The combination of cryptography and economic incentives makes decentralized p2p networks secure, valuable and trustworthy.
Wait! There is much more to read and learn…
- Vitalik Buterin’s 1hr presentation about cryptoeconomics discusses further cryptoeconomics that I didn’t include here.
- Princeton’s 300 page Bitcoin book
- Unchained: 1hr Podcast about cryptoeconomics with Olaf Carlson Wee and Ryan Zurrer
- Examples 2 and 3 of this article about cryptoeconomics
- Vlad Zamfir’s “History of Casper” article series — Casper is a PoS consensus mechanism, which is currently in the works
- Did I miss some other great further readings? Let me know!
Big thanks to Jacob Eliosoff, Tristan Knight & Igor Krawczuk for your feedback!If your crypto startup or investment team is looking to hire someone with passion, drive and experience in finance and startups, please email me at anami.nguyen at gmail. Let’s connect on LinkedIn (please include why you’re connecting.)
Intro to Cryptoeconomics was originally published in Hacker Noon on Medium, where people are continuing the conversation by highlighting and responding to this story.
Disclaimer
The views and opinions expressed in this article are solely those of the authors and do not reflect the views of Bitcoin Insider. Every investment and trading move involves risk - this is especially true for cryptocurrencies given their volatility. We strongly advise our readers to conduct their own research when making a decision.