Latest news about Bitcoin and all cryptocurrencies. Your daily crypto news habit.
GNU Privacy Guard (GPG, also called GnuPG) is a free encryption software you can use to encrypt and decrypt files. While the documentation for GnuPG is excellent, this is a quick cheatsheet on how to get started with GPG.
Install GPG
Mac
You need homebrew to be able to install gpg on Mac . If you don’t have homebrew installed, you can learn how to do that here. After that, it is a one line command.
brew install gnupg
Windows
There are many ways to install gpg on windows. Perhaps the easiest way to is to go to GnuPG site and use the simple installer for the current GnuPG.
yum install gnupg
Ubuntu / Debian
If you are using these Linux distributions, you might want to change the commands in this tutorial to gpg2 after using the command below. You can find more infomation on this here.
sudo apt-get install gnupg2
Entire Process
GPG uses a method of encryption known as public key (asymmetric) cryptography, which provides a number of advantages and benefits. In a public key (asymmetric) encryption system, any person can encrypt a message using a public key. That encrypted message can only be decrypted with the corresponding private key. This section just goes through the GPG commands to do this. If you don’t understand asymmetric encryption, there is a wonderful youtube video on it here.
Generating Key Pair (Private and Public Keys)
1) Create your keys. This will generate a key pair. One is a private key which you need to keep safe and a public key which you can share with other people.
gpg --gen-key
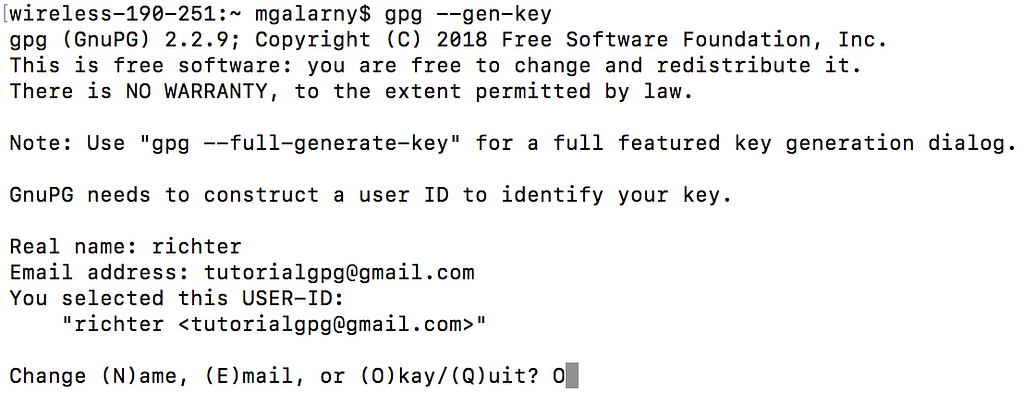 Enter name, email address, and O
Enter name, email address, and O
2) You will have to enter a password. Keep it somewhere safe.
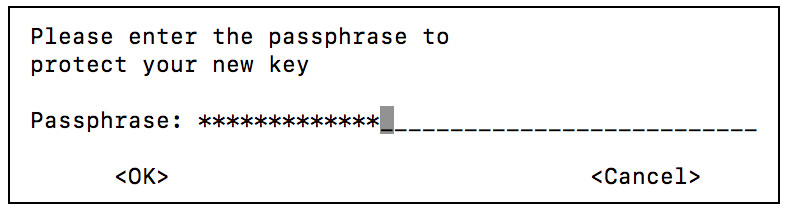 Enter and re-enter your password
Enter and re-enter your password
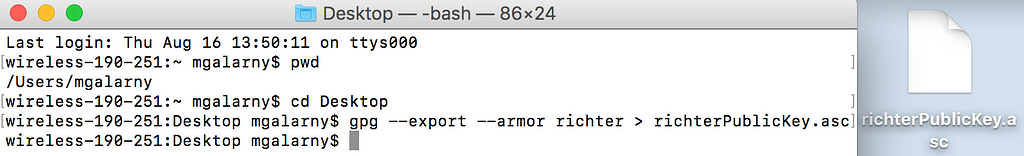
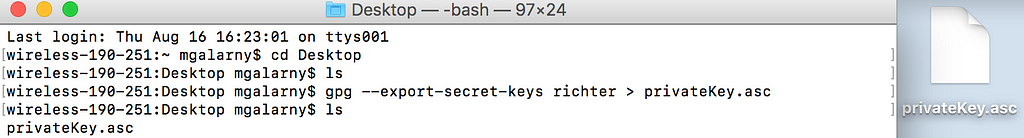
3) Export your public key. In this case, richter is the name of my public key. It will be whatever you named your key in step 1.
gpg --export --armor richter > richterPublicKey.asc
4) Send the public key you exported to another person.
Public Key Holder
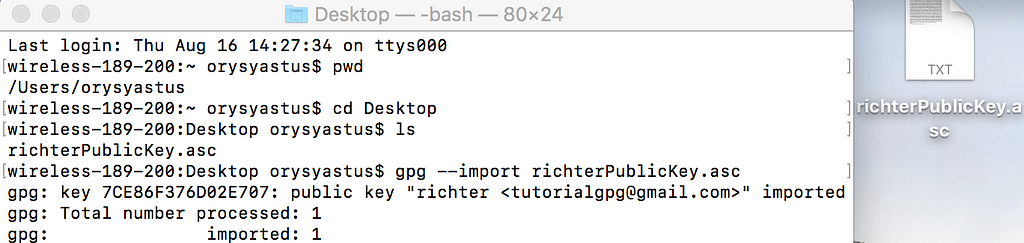
1) Import another persons public key. You need to substitute richterPublicKey for the public key you wish to import.
gpg --import richterPublicKey.asc
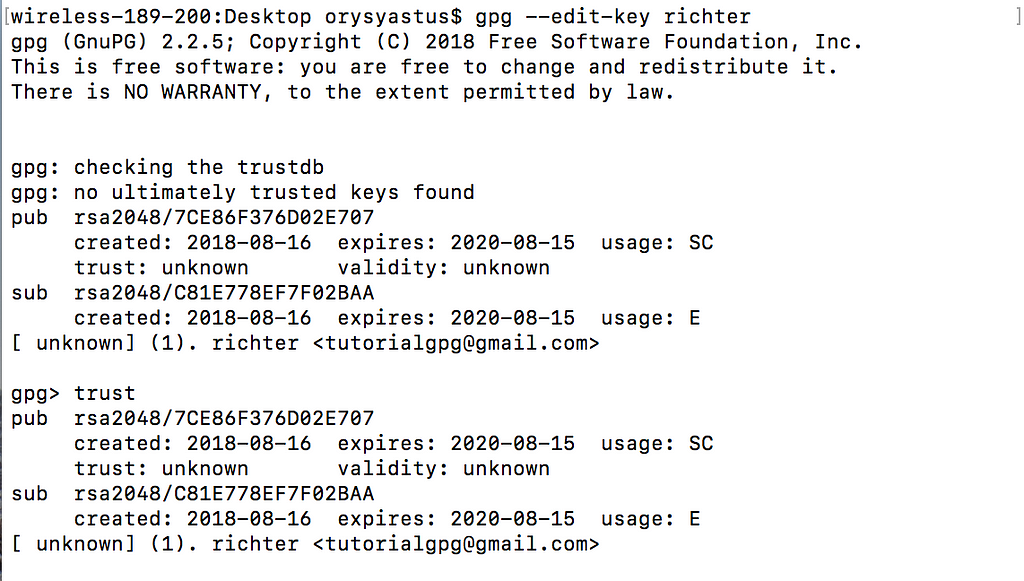
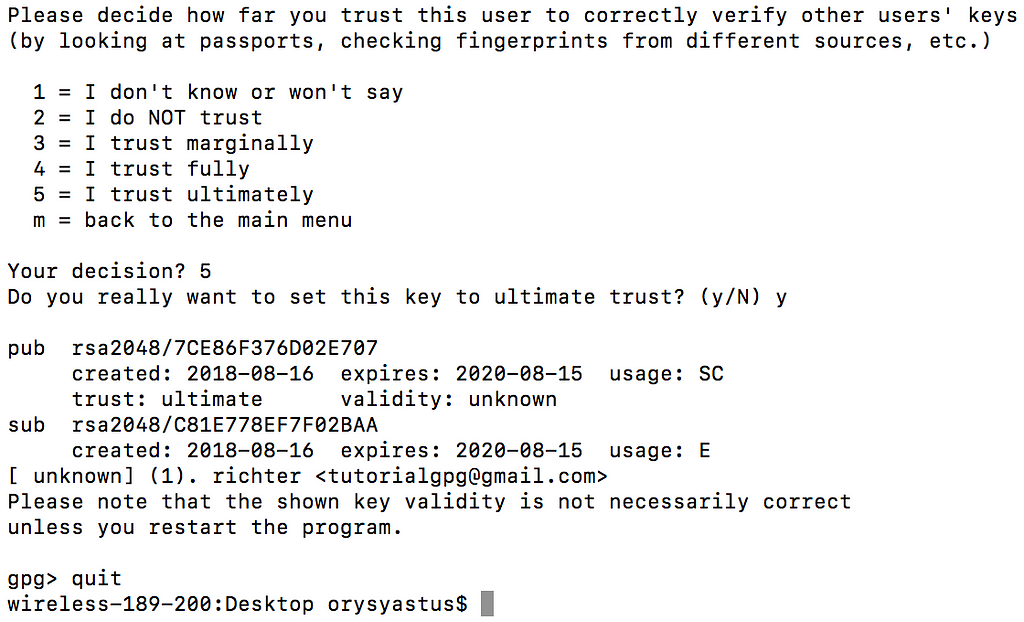
2) Trust the public key. This will prevent GPG from warning you every time you encrypt something with that public key. You need to substitute richter for with the name of your public key.
gpg --edit-key richter
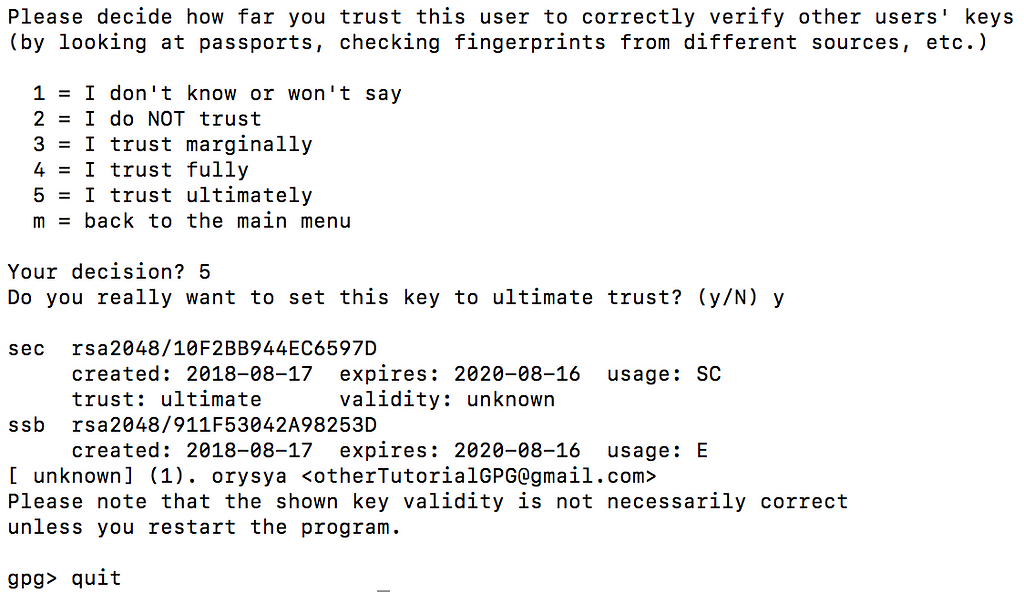
Enter trust
Enter 5 , y , and then quit
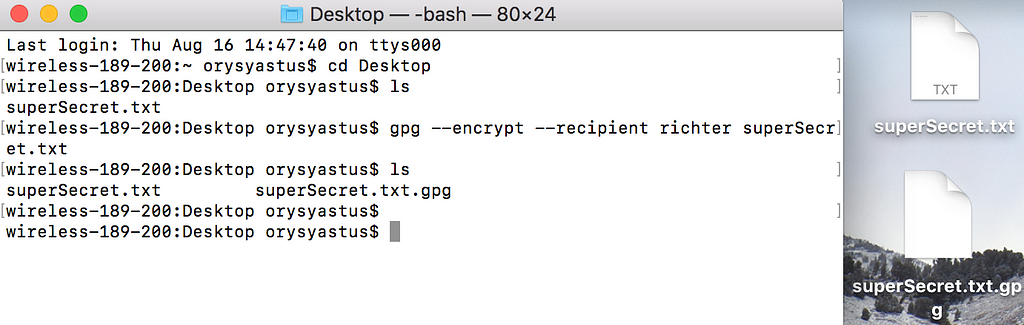
3) This step shows how to encrypt a file (in this case, I encrypted a file superSecret.txt).
gpg --encrypt --recipient richter superSecret.txt
4) Transfer the encrypted file to the private key holder.
Private Key Holder
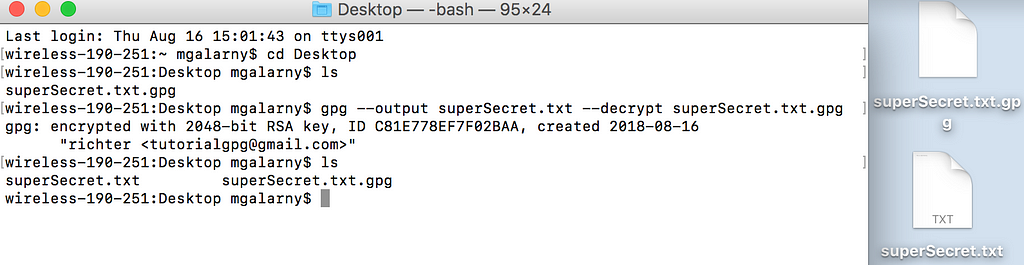
After receiving the file, you can decrypt the file. You will have to enter your password.
gpg --output superSecret.txt --decrypt superSecret.txt.gpg
Keep in mind that you can also decrypt multiple files using the following command.
gpg --decrypt-files *.gpg
List Keys in your Keyring
Public Keys
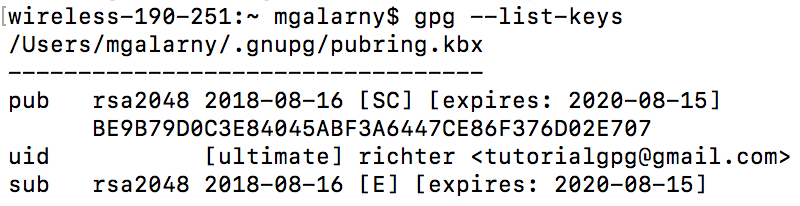
You can view a list of public keys in your keyring as well as the name and email address associated with each key
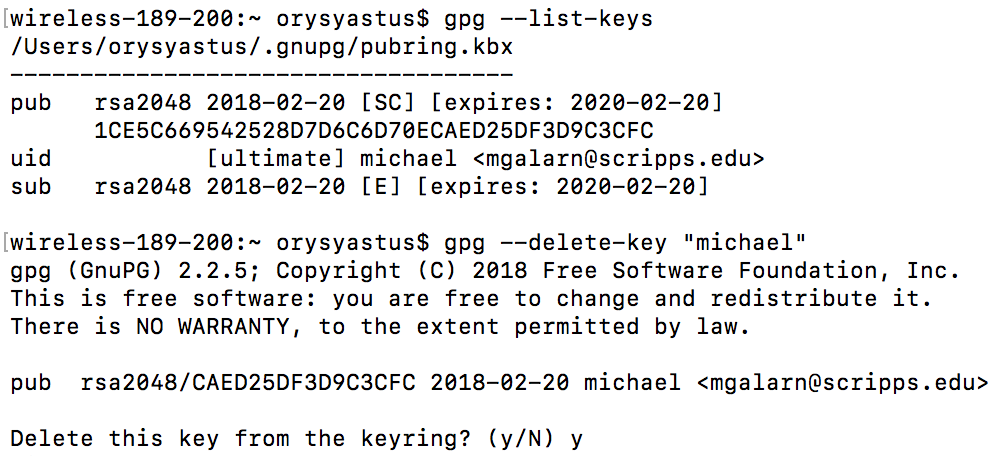
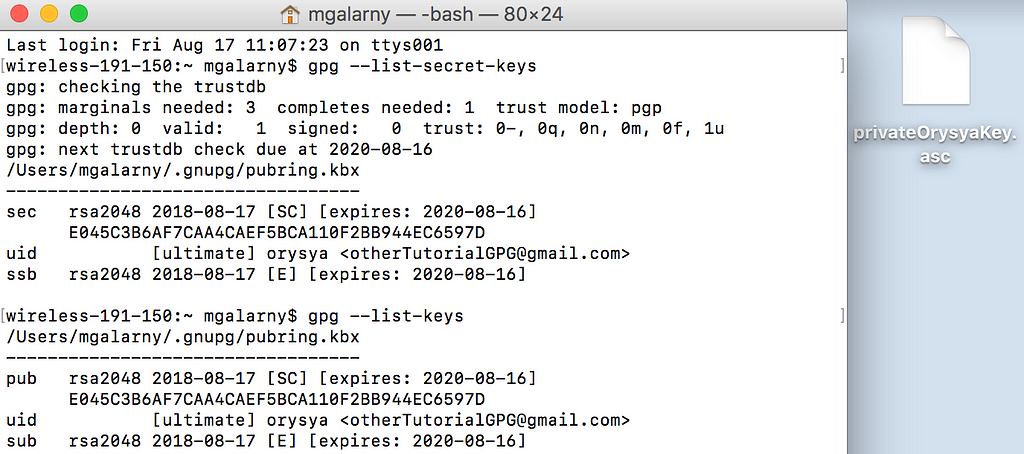
gpg --list-keys
The following command will list the private keys in your keyring. This will show the private keys you have (including the one you created or imported earlier)
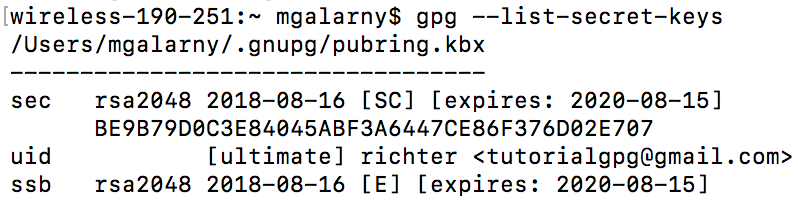
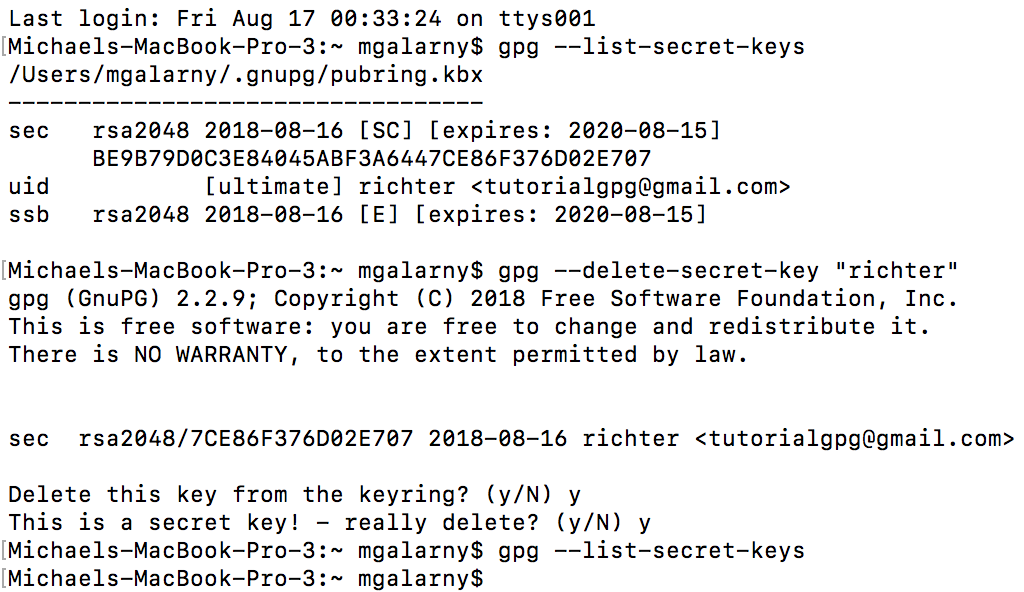
gpg --list-secret-keys
Delete Keys from Keyring
You can also delete keys from your keyring.
Remove Public Key
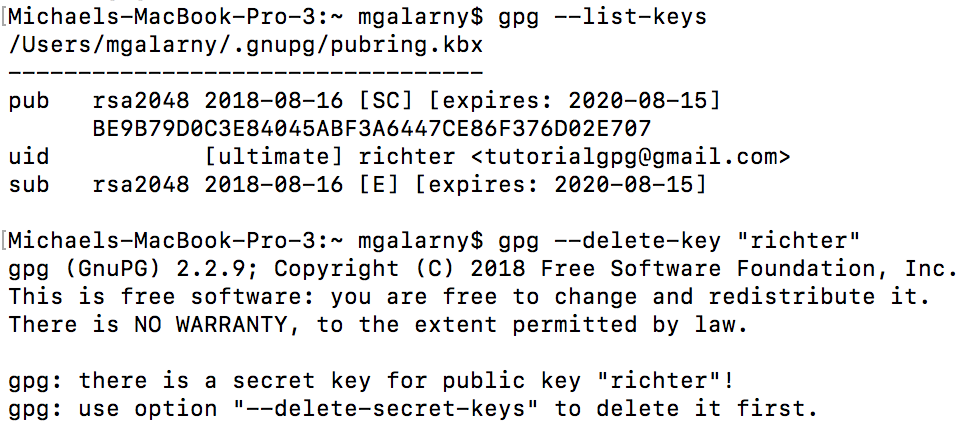
gpg --delete-key "User Name"
Note that if you try to delete a public key when you have its associated private key you will run into an error.
gpg --delete-secret-key "User Name"
How to Export and Import a Secret Key
Export a Secret Key
You can also export your secret key.
gpg --export-secret-keys richter > privateKey.asc
gpg --import privateKey.asc
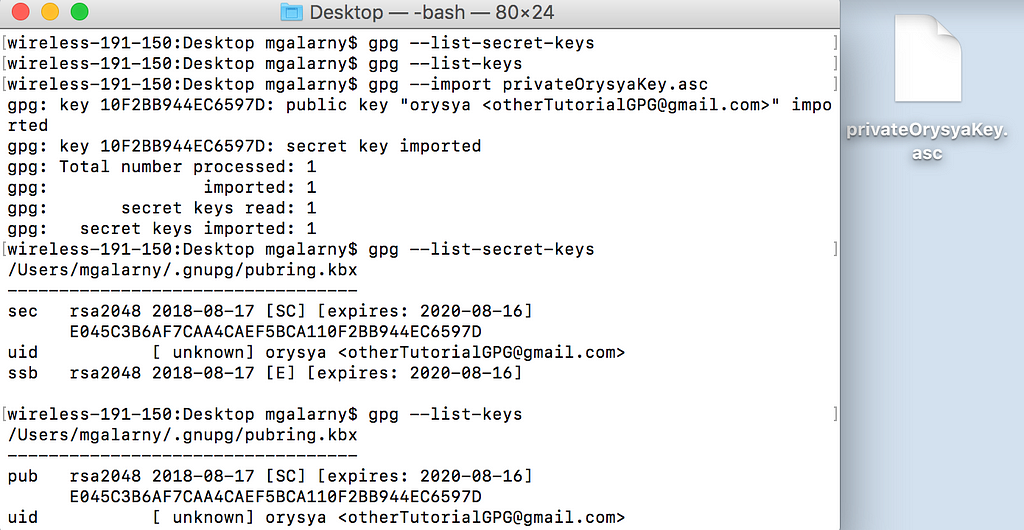 Not done yet, you still need to ultimately trust a key.
Not done yet, you still need to ultimately trust a key.
You will need to make sure that you also ultimately trust a key.
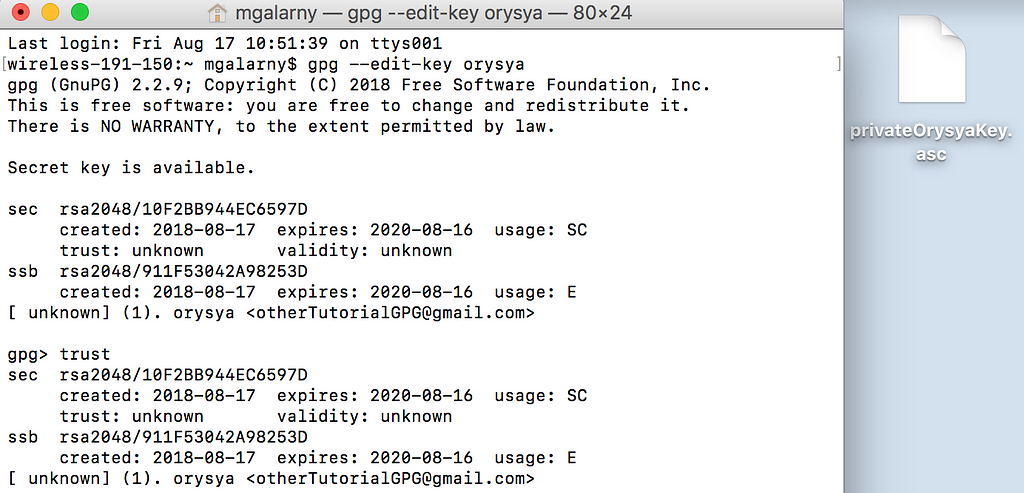
gpg --edit-key orysya
enter trust
Enter 5 , y , and then quit
You can check this by using the command
gpg --list-secret-keysgpg --list-keys
Keep in mind that you could also automate the trusting process.
expect -c "spawn gpg --edit-key {KEY} trust quit; send \"5\ry\r\"; expect eof"Conclusion
I hope you find this tutorial useful. If you any questions or thoughts on the tutorial, feel free to reach out in the comments below or through Twitter.
Public-key (asymmetric) Cryptography using GPG was originally published in Hacker Noon on Medium, where people are continuing the conversation by highlighting and responding to this story.
Disclaimer
The views and opinions expressed in this article are solely those of the authors and do not reflect the views of Bitcoin Insider. Every investment and trading move involves risk - this is especially true for cryptocurrencies given their volatility. We strongly advise our readers to conduct their own research when making a decision.