Latest news about Bitcoin and all cryptocurrencies. Your daily crypto news habit.

Most of the mechanisms used in a blockchain network existed before Satoshi’s whitepaper. Peer to peer network, Cryptographic Hashing, Asymmetric key encryption, Merkle Tree, for instance, have been well known for a long time. The true revolution brought about by the Bitcoin in 2009 is cryptoeconomics and it is paramount to understand it if you want to grasp the real value of the blockchain revolution.
The purpose of cryptoeconomics is to build strong protocols that will be able to govern and securely develop peer-to-peer decentralized networks.
Peer to peer networks exist for some time. “Torrents” for instance, that many people used to share folder online, are peer to peer networks. However, they lake efficiency because members are happy to download content, but have no interests in sharing theirs. Blockchains, through cryptoeconomics, would give members this incentive to share folder, by giving token in exchange for instance.
In other words, blockchain networks could be compared to an incentive machine that will inject market structures in decentralized networks.
How does Cryptoeconomics work?
A peer to peer network such as the bitcoin is a decentralized and autonomous economy that needs to be implemented by its members since this function is not delegated to a third party anymore. But these members like any humans, are rational and will not spend their time working for a network for free. That’s the reason why they need to be rewarded and this is precisely what Satoshi has invented.
Cryptoeconomics refer to “crypto”, which are the technical mechanisms of a decentralized network, and “economics” which are the way these mechanisms are organized to incentivize members of the network to action it or develop it. To speak in basic terms, cryptoeconomics is the use of money to secure and develop a decentralized network.
Security means that the decentralized network must find a consensus on the way to update the shared database (i.e the blockchain) even when a certain amount of its members are not trustable (the Byzantine General Attack).
Development means that the members of the network are incentivized to update the shared database, i.e to use the service provided by the protocol and the network. We will now describe these two points.
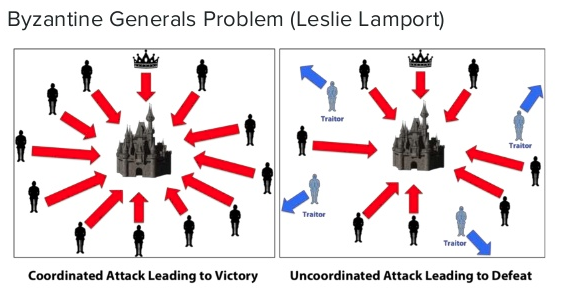
The Byzantine General Attack
This concept is essential to understand how rogue members of the network can attack a decentralized network. It is important to note that attack would only come from the inside, i.e from persons who have downloaded the protocol and have decided to use it against the rest of the network. If several members are acting in breach of the rules of the protocol or exploiting them at the same time, the network is under attack since it could become impossible to update the shared database and so monitor additional transactions among members of the network.
The example of the Byzantine Generals has been created to illustrate the concept. You just need to imagine 5 generals ready to attack a town. They are all placed around the city and they just need to coordinate with each other to launch the attack. If at least 2/3 of the army does not attack at the same time, they will be outnumbered by the city’s army and lose the battle. The leading general sends a messenger to the general who is next to him to communicate the time of the attack and ask this general to transmit the information to the next general. But what if this general is a traitor and decides to communicate a different hour.
Cryptographic mechanisms used by decentralized networks to solve the Byzantine attack issue are different depending on if we refer to a private or a public blockchain. With public blockchain, the most famous is Proof of Work, which has been popularized by the bitcoin. Other mechanisms such as Proof of Stake or Delegated Proof of Stake are gaining traction every day. With private blockchain mechanisms such as Practical Byzantine Fault Tolerance (used by Hyperledger for instance) and the Federated Byzantine Agreement (used by Stellar and Ripple) are more developed.
The Bitcoin example
On one hand, Bitcoin protocol uses several cryptographic mechanisms to ensure that users safely detain their bitcoin (Asymmetric key encryption), that transactions are securely added to the blockchain (cryptographic hashing used to link each block and transactions) and that all the history of network transactions is impossible to change (Merkle Tree).
On the other hand cryptoeconomics through Proof of Work are used to secure the system because it makes attack too expensive to be conducted by a rational attacker.
The Bitcoin protocol makes it extremely expensive to mine bitcoin in order to avoid the “51% attack”, which implies that a miner gathers more than 50% of the network hashing power. Crossing this limit would give this miner the possibility to prevent other miners to add a block to the blockchain and undo previous blocks. But it is estimated that gathering 51% of Hashing power would require USD 6 billion in hardware and consume USD 4 million per day (https://gobitcoin.io/tools/cost-51-attack/), which obviously cannot be profitable just by removing a block from the blockchain. This is why we mention that the high cost of mining ensures the security of the network. This is also why these costs increase proportionally to the number of miners acting on the network. It is important to note that the “51% attack” is not simply theoretical since a mining pool reaches this threshold in 2014.
Finally, the Proof of Work mechanism is tailored to reward minors for their participation in the consensus process. Each miner who managed to add a block to the blockchain will receive 12,5 bitcoin. This way minors can repay their investments in mining material, electricity and bandwidth.
According to Elad Verbin, “Nakamoto found a clever game-theoretic solution to the classic Byzantine Generals’ Problem, by paying the generals a salary as long as they act honestly, but garnishing that salary if they are caught trying to cheat.”
Several incentive systems already exist
As we just explained, each decentralized network organized over a blockchain is an autonomous ecosystem, which uses different mechanisms to induce its members to participate in the development and/or the security of the network. Members are generally rewarded with tokens issued by the protocol.
These revenues can be very varied and depend on the problem that attempts to resolve the protocol. We can see patterns appearing and we will describe in a separate article the cryptoeconomics primitive, which have already been identified. In this article we will, however, identify three modes of recurring compensation:
- Dividend
- Buyback
- Increase in value
1 — DIVIDENDS
A token generates dividends when the members of the network are paid for their participation in the network. This participation may take several forms:
- The provision of resources: users of a network are paid for lending to the network resources, which belong to them. These resources can be very varied:
It may be the calculation capacity of a computer installation: Mining is the most common example. As we described above, the miners of a network (bitcoin for instance) offer to the network their own computer installation calculation capabilities (hashing power), to complete the consensus mechanism (proof of work for example) and add the transactions of the network on the blockchain. Minors are therefore paid for their contribution to the network, in bitcoin created by the Protocol (and costs attached to transactions). Mining is also the only mechanism for the creation of bitcoin.
It can also be memory space: In the case of SIA, Storj, Filcoin, Madsafe, users are paid to let other members of the network dispose of a part of the memory of their computer installation.
- By the production of content: Steemit is a good example. It is the first social media on which members are paid for posting articles and comments. Each member of Steemit vote for the articles that he reads and generates remuneration for the writer that is proportional to its level of involvement in the network. So as soon as you vote for an article, the protocol automatically grants remuneration. The more Steem token (token issued by the Protocol Steemit) you possess, the more your vote will make a significant remuneration to the author of the article.
The number of people who votes for your article is important because the more vote you receive the more money you receive. It is not rare to see writer be paid $500 for their articles.
Steemit is an excellent example of the way the Internet will evolve in the coming years. At the moment we provide the few platforms that we use (Facebook, Twitter, Intagram…) with all our content and personal data for free. But this period will end pretty soon. With the decentralized protocols and the new social media platforms, you no longer need to give your personal data and you are paid for the content that you add. This formula will apply very soon to all platforms who wish to survive the blockchain.
For example, I would not be surprised to see websites such as Tripadvisor compensate its users with travel tokens for any comments added on the hotels that you have visited. These tokens would grant you free nights in other hotels.
2 — TOKEN REDEMPTION:
In cryptoassets universe, token redemption does not take the same form as securities redemption that we are currently experiencing. The redemption is carried out in an indirect manner by the destruction of tokens.
It is indeed important to understand that in a network where the number of tokens is limited, destroying a certain number of tokens increases the value of the remaining tokens.
Bitshares consensus mechanism (delegated Proof of stake), for example, allows “witnesses” wishing to be elected to propose to the members of the network of “burn” (“burn”) a part of tokens that they will receive from the protocol as a reward for their work of “mintage” (we talk about “mintage” for proof of stake mechanism and not of “mining”, but the meaning is the same). Instead of getting richer, they, therefore, propose to remove these tokens from the network and thus to increase the value of other tokens.
3 — THE INCREASE OF VALUE
This is a common component of any investment, yet it is important to understand how and why a token gets value.
IF YOU ENJOYED THIS ARTICLE AND FOUND IT USEFUL, PLEASE DO NOT HESITATE TO LIKE IT AND SHARE IT! THANK YOU
Cryptoeconomics is THE revolution! was originally published in Hacker Noon on Medium, where people are continuing the conversation by highlighting and responding to this story.
Disclaimer
The views and opinions expressed in this article are solely those of the authors and do not reflect the views of Bitcoin Insider. Every investment and trading move involves risk - this is especially true for cryptocurrencies given their volatility. We strongly advise our readers to conduct their own research when making a decision.