Latest news about Bitcoin and all cryptocurrencies. Your daily crypto news habit.
Forget the clickbait bulls&$%. THIS is actually why…
I’ve been asked the above question forever (it seems) and was asked again by a number of people from the more “mainstream” sector in the last few weeks.
So in the spirit of turning what’s in my head into content, and not having to repeat myself 100 times, I’ve decided to write an article.
There a 4 key things to consider with the above statement, so you can better understand what’s going on. By the time you finish reading this, you’ll know exactly what TO do, and what NOT to do…
First of all….lets debunk some mis-conceptions.
1. What do you mean by “being hacked”?
Being “hacked” is such a broad term.
When the every day person thinks about being hacked, they imagine some guy in a dark room somewhere, somehow gaining access to your computer or your online data with a few strokes of the keyboard..
This couldn’t be further from the truth. In fact, it’s a complete load of crap.
Most “hacking” these days actually comes in the form social engineering type hacks. Social Engineering is defined as:
“the use of deception to manipulate individuals into divulging confidential or personal information that may be used for fraudulent purposes.”
This has nothing to do with a hacker getting “access granted” like the image above, but more from people who are good communicators, that might do the following to get access to your personal information.
Phone / Email Hijacking
- They go down to your local Telstra / Vodafone shop & buy a SIM card.
- They say “oops” I lost my wallet and phone yesteday — I just need to grab a new SIM card to re-activate it.
- 15y/o staff member says “sure”, I just need to check some personal details:
- Hacker (impersonator) says, “sure”, and begins to give them; Date of Birth, Address, Mother’s Maiden Name, and possibly even Address.
Hold on…you might say How?? Magic?? Mind Reading?? No…
How about facebook, google and your mailbox.
- Phone shop staff member says; “great, here’s your new SIM”.
- You then proceed to set up the SIM, and then start the process of accessing their emails.
- Step 1: Forgot Password
- Step 2: Input recover phone / Mothers maiden name
- Step 3: Reset Password
- Step 4: Thankyou very much — I now have access to your emails.
- Now that they have that — they can go in & log into any of your accounts, click reset password, and go to town.
You might say; “Why would someone go into the shop & do all that. Can’t they just call up your phone provider and pretend they’re you”?
Well…yes — and to be honest — that’s what they do most of the time. The above was just illustrating how easy it is in person. Over the phone is even easier.
Another very very common way, and aso a form of social engineering is:
Phishing
This is by far the most common form, especially when it comes to cryptocurrencies, ICO’s, etc.
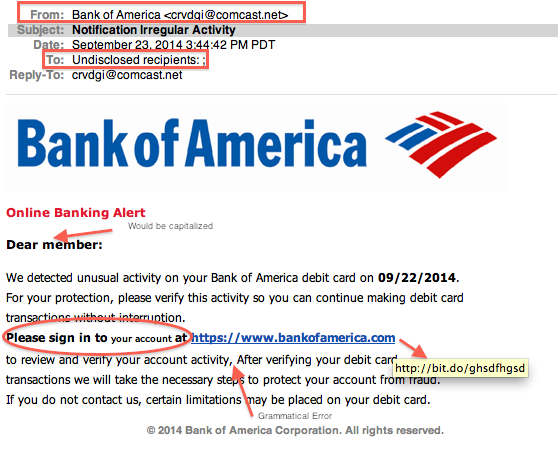
One form of phishing is where you get an email from a “trusted” company, like PayPal, or eBay, or your Bank — asking you to “log into your account” to check a balance or rectify some personal information. The branding of the email looks legit, the link even looks legit, and after you click on it, the landing page also looks legit.
You log in as you normally would, with your email & password — only to find that you couldn’t log in. Most people then think “Stupid Paypal. ask me to log in and then I can’t even log in”, so they leave it for later.
What they don’t realise is tha they’ve just input their username and password into some hacker’s database, who in the background says “thanks alot” and proceeds to input those details into your real PayPal (or Netbank, or email, or whatever” account, changes the password, locks you out, clears out all your money / funds / crypto / whatever.
The problem is compounded when the average person uses the SAME password across every service!! Their password for their email is the same for their Internet banking, PayPal, Spotify, facebook, Netflix and their crypto exchange!
Now — Mr or Mrs Hacker have access to ALLLLLLL of your stuff. And unless you realise it quickly — you’re screwed.
Phishing scams are quite advanced these days, and can impact even the most security conscious of us.
I lost about 20 bitcoin in the early days when I clicked on the link to an exchange, after I searched for it in Google, from a friends laptop (I didn’t have mine on me).
I googled the exchange I wanted to log into quickly to place a trade. I clocked on the top result in Google (I think it was a Google Adwords Ad), it took me to the page I recognised as the trading platform, I input my username & password — and viola — it didn’t log in..
I thought for a second..wait up — what’s wrong here?
So I refreshed the page, went back to google, clicked on the top link again — this time, unbeknownst to me, I actually went to the correct site, logged in, everything worked, I placed my trades and left for the day.
I had NO CLUE that I’d just given up my username & password.
2wks later when I tried to log in, I couldn’t. I reached out to support, they verified it was me, they helped me reset my password, but it was all too late — all the funds were gone.
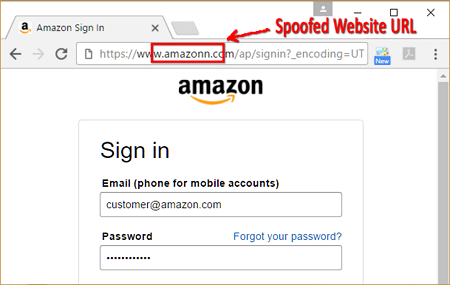 The bastards are cheeky. If you don’t triple check, you’ll miss it.
The bastards are cheeky. If you don’t triple check, you’ll miss it.
Back then it wasn’t worth too much, so I guess I wasn’t read to jump off a building — but looking at today’s price & writing this, that’s a call $200k out the window..And it was 100% my fault.
Every industry has risks. If you want to play with money or sensitive information online, you should probably learn some basic infosec (information security). Something like 2FA (2-factor-authentication) would’ve saved my ass.
The same way you’d understand the risks associated with building a house, before you go build it. Or if you’re going to transport 1 tonne of Gold, you wouldn't do that in a wheelbarrow for everyone to see — you’d do it an armored truck, with 4 guards. The same way you don’t go to the bank, withdraw a bunch of cash and walk down the street waving it around.
Understanding what you’re doing before you do it important. I hope the war story above serves it’s purpose; to teach other people not to do the same.
Anyway. Now that we understand how actual hacking works, lets take a moment to understand what’s going in Crypo Land — and why there’s alot of so-called hacking going on (hint…it’s over-exaggerated)
2. “Lost Bitcoin” is not “Lost”.
Neither should it be labelled as “hacked”.
The following article talks about how “20% of all Bitcoin is lost”.
Reports Say 20% of All Bitcoin (BTC) is Gone, But "Crypto Hunters" Can Help Recover Data
You don’t just “lose” Bitcoin. All of the Bitcoin that the Bitcoin network has ever produced are still on the network. It’s the “access” to some of that Bitcoin that’s been lost.
This access is what’s known as “private keys”.
A private key is like a password (just alot longer) and is the actual “thing” that decrypts the encrypted information.
Public & Private Key cryptography, and the standards of encryption in basically all cryptocurrencies today are exactly the same as what secures VISA, MasterCard, every credit card, Internet Banking and personal or sensitive information database — anywhere.
It’s not the encryption that’s being broken, but the management of the keys to access the encrypted data that’s being mis-managed.
You can think of your data as being stored in a letterbox. This magical, digital letterbox has the “stuff” inside it (your Bitcoin, your personal data, sensitive information held on a database, etc) and nobody can actually see inside or break into that letterbox.
The only way to access & view what’s inside is with the Private Key.
Password are generally a useful “abstraction” of a private key, where instead of you having to know how to use a private key to sign a transaction or a perform a function to access data, a program you’re using gives you a password (which is earier for you to remember) and when you input that password, the application performs functions, for example “view data”, or “send Bitcoin”, etc with your authority (because you logged in).
The Private Key is the Magic Word!
If data is encrypted, if the passwords, the usernames, and personal information are stored on encrypted databases (which most are these days), it’s basically impossible (or highly highly improbable) that the data is going to be viewable by way of the encryption being broken.
If something gets leaked or “hacked” it’s because the private key was leaked, or the password that represents the private key was leaked.
Security is less about encryption, and more about the protocols used to ensure the access codes, passwords and/or private keys are not leaked.
Now the we understand that, lets have a look at how these so-called “hacks” actually happen.
3. Exchange Hacks — The Crypto Honeypots
A honeypot is basically a metaphor for something that stores a whole lot of valuable information / data / money, etc.
Hackers term it that, because if they get in, they get the gold (or the honey).
 ummm…..not that kind of honeypot.
ummm…..not that kind of honeypot.
Now that you know what private keys / passwords are, and what’s going on with how people get phished or have their details hijacked, and how little time people actually put into thinking about infosec, lets see what’s going on here.
- Most exchanges have BAD information security protocols.
Most of the crypto exchanges that were built over the last few years, were built by people who just don’t get it. They’re not security experts, they generally come from finance (which has 100 years worth of custodianship protocols built around it) and simply don’t realise how easy it is for data to be leaked.
When you hear about exchanges being “hacked”, it’s generally because the master password, or access codes were somehow leaked, or were poorly protected in the first place.
When you hold your “crypto” on an exchange, what you’re doing is entrusting the security / storage of the private keys that are associated with your funds, to the owners / operators of the exchange.
They are holding EVERYONE’S private keys. And most of the time in encrypted databases. Which is fine. What happens is that the password or private key that encrypts all that data is generally known by one or two people.
What if something happens to that person?
What if their personal stuff is hacked (like in the social engineering examples above)? What if they’re phished? What if, like most people, they use the same password for the company database that they use for facebook?
What if a key employee, who has access to that password or private key, decides to go rogue? Or even if he doesn’t, but is fired or quits and knows enough about the boss to perform a social engineering type take over of the boss’s accounts..
Well…then ALL of the data that’s protected by their private key (or password) is now compromised.
This happens ALL THE TIME in the normal world. ALL THE TIME.
Equifax, the world’s largest holder of private data, leaked hundreds of millions of people’s personal data. Not once, not twice, but we don’t know how many times!
Equifax Says Cyberattack May Have Affected 143 Million in the U.S.
143m above. Here’s another 20m to add to that:
- Equifax breach exposed millions of driver's licenses, phone numbers, emails
- Equifax says more private data was stolen in 2017 breach than first revealed
Data breaches, in centralized systems, are almost inevitable.
The difference between Equifax (or a traditonal business) and Crypto exchanges is:
- The equifax leak meant hackers got access to people’ personal data, and with that could go an hijack their identity and get access to a whole lot of other things (incuding their crypto exchange accounts if the person wasn’t aware of the breach).
- With a crypto exchange, that the data breach involves access directly to cryptocurrency private keys. Which in this case means direct access to funds, which are natively digital, which can be moved across the internet instantaneously, and which once they’re associated with a new set of private keys, cannot be returned.
2. Most people have BAD information security protocols.
You’re going to read this and think “you can’t win”. And you’d be right, except winning is about getting smarter — and most people probably shouldn’t play with fire whilst it’s too hot…but anyway…
Alot of people have been “hacked” due to no fault of the exchange.
They’ve simply been phished (much like what I explained above).
Most people have no idea how to store their passwords, where to store their passwords, they slap their personal information all over the web, they have no idea what hacking actually entails and they think phishing is when you go out on the boat for a weekend to catch fish.
The image above seems like hyperbole, but is actually sadly accurate.
In the crypto world, the 35yr olds are actually the granny’s above, getting taken for a ride because this space is so new, and they just don’t have the knowledge or understanding to compete with the 18yr old digital natives.
Losing your password, or accidentally leaking it somewhere means you have physically given the “keys” to your house to someone, who’s intent it is to take what’s in your home.
And because it’s digital, and they can do it whenever, from wherever, believe that it’s going to be done.
And you might say; “this is ridiculous”, it can’t happen with a bank, they’d give me my money back, etc — which is mostly true, because the money is traceable, so you can get it bac — but also note that actually giving away your password negates their terms and conditions, and if they don’t want to they won’t help you, and if they do this has a huge cost in terms of resources, etc in the banking world — which we end up paying for.
In rebuttal to the above, I’d say every technology has it’s pro’s & cons.
The same argument was made for the original cars. They were dangerous, they would “kill people” and the British (for example) mandated laws which stifled the development of the automobile in England, for example the one where you needed 3 operators to legally drive a car (the red flag act):
- One on the wheel
- One in the passenger seat, to refuel the car
- One to run 150m ahead of the car & wave a red flag to notify that a car was on the way.
Seriously….wtf…
The automobile was basically invented in Britain, but it’s no wonder that the innovation moved to the USA, and with Ford, led the world in the industrial revolution & creation of the middle class.
All new technology has it’s pro’s & cons. Moving toward a world, where value natively is digital, always on, open, instantaneous, and accessible by anyone, anyehere & anytime — having to learn some basic infosec is a small ask — and the path toward this world will surely involve some ups & downs — like it did with Electricity, the automobile, the telephone, the internet, and now Bitcoin & digital currencies.
4. Bitcoin & Cryptocurrency Hacks
Cryptocurrencies are never really “hacked”, but their core protocol or their consensus mechanism can be compromised, if it’s not been thought through properly, or if the game theory is not sound — in which case the rules of the network can be changed and the data (funds) associated with certain private keys can be changed (fund re-appropriated).
This is different to a “hack” as described above, and is generally the result of a poorly designed consensus protocol, no understanding of game theory, and a very non-decentralized (ie; centralised) system that can be controlled (network rules changed) by a majority, that’s not hard to achieve (the more decentralised, the harder it is to get a majority, therefor the more secure).
Bitcoin is the ONLY digital network, that we’ve ever created (as humans) that has had 99.9% uptime, or that’s never been compromised. The 0.01% was a bug from the early days, where Bitcoin was still worth in the cents (from Token Daily):
Fun fact: bitcoin was hacked 8 years ago in what is known as the “value overflow incident.” Block 74638 contained a transaction that created 180 billion bitcoins for three different addresses. The blockchain was forked, so the transaction no longer exists on the longest chain (and neither do the bitcoins it created).
Other than that, it’s the most secure digital network in history.
Why?
It’s not because of some fancy, incredible encryption — it’s because of the rules of the network, that the participants of the network adhere to. It’s a mix of economics, game theory, incentives & dis-incentives, cryptography, encryption & more.
Bitcoin is a technological solution, to a social problem, with far reaching political impact.
Bitcoin represents a new form of social “agreement” or “trust” that’s been applied to solve (or improve) the oldest form of “shared fiction” our species (Homo Sapiens) has ever built societies on top of, ie; Money.
To learn more about how money has evolved over the years, and how we’ve come to Bitcoin & Digital currencies, go here:
Homo Sapiens, Evolution, Money & Bitcoin
And to understand how all the economics, cryptography, game theory, etc comes together, read this:
Cryptoeconomics = Social Engineering
Now….I can hear you saying it:
“If Bitcoin is so “hacker proof”, then why do I hear about hacks all the time, people losing their funds, their wallets being hacked, etc, huh, huh??”
There is an answer…well a few main one’s actually:
1. You lost your private keys.
This has nothing to do with Bitcoin. This is a PEBKAC problem (look it up).
In the early days, when Bitcoin was purely experimental, and nobody gave a real shit (including me), we had no concept of private key hygiene and why storing $500 so securely back then would be so important. Fast forward 6, 7, 8 yrs and with that $500 worth $10m, you’ve got people who had that private key stored on a hard drive on an old computer, which ended up in a dumpster, now going out, digging up a dumpster, looking for that computer, hoping they can somehow salvage the data on there….hoping….praying…that they can get that magical private key…that will deliver them to the promise land.
Yep…it’s true.
I’ve lost my fair share of private keys from the early days. No clue where I put that shit, and because I buy a new computer every 18/24mths, I don’t even know where to start looking.
But hey — that’s part of the war stories, and part of why I can appreciate how important personal information security is in our ever-increasing-digitally-dominated world.
So if you downloaded a wallet, and you wrote your private key somewhere, you bought a bunch of Bitcoin and you then lost the private key, good luck.
Reports Say 20% of All Bitcoin (BTC) is Gone, But "Crypto Hunters" Can Help Recover Data
This article (linked earlier too) talks about people going to hypnotists in the hopes of remembering that private key by bringing it from the sub-conscious to the conscious mind. It talks about people with corrupted or broken hard drives looking for data retrieval experts to get it back, etc.
And they’re doing this, because as I mentioned earlier, all of that Bitcoin is still there, on the network, associated with a set of private keys. He who controls the keys, controls the Bitcoin associated with them.
Perhaps a hypnotists or some other wallet recovery service might be able to help. Either way, best of luck.
2. Your wallet was hacked / corrupted
There are 2 types of wallets. Hosted & Client Side.
Client side means you control the private keys, and they’re not stored with the wallet provider. If this kind of wallet is corrupted, etc — you take the private kets and just set up a new wallet, and restore the funds with the private key. Nothing is lost.
Hosted wallets on the other hand, store your private key. This is no different to an exchange, in that every user’s private keys are held there. If the hosted wallet service is compromised (which I’ve had this happen to me too, and lost $10k in crypto…yeah — I’ve had some bad luck right), then there is nothing much you can do. But….
There is a place for these services!!
Most people really, really suck with custodianship, and personal information security hygeine. Most people (remember in Ready Player One), have their freakin computer password written on a post-it note…ON THEIR COMPUTER!!
 Password was on the chair !! wtf….
Password was on the chair !! wtf….
So for these people, holding their funds on a reputable exchange, or a reputable hosted wallet service is actually a better idea. Because if they forget their password, they can just identify who they are & have it reset. Otherwise if they lose their wallet, or their phone, or their laptop, and then go to restore their wallet (ie; their funds), but have also lost their private keys, then goodbye Bitcoin…and basically no chance of getting it back..
In closing
Digital currencies are still nascent technologies.
And because this is all happening at the intersection of cutting edge technology, social & societal transformation and the most important building block / shared fiction of them all, ie; “Money”, it’s going to be a WILD ride.
We are barely 9yrs into a global revolution. Most probably the greatest we’ve seen in our lifetimes, if not since the internet (which changed everything).
In the early days, nothing moves in a straight line (in fact, nothing ever does continue in a straight line. Wether early or later); but, my point is that we’re super super early.
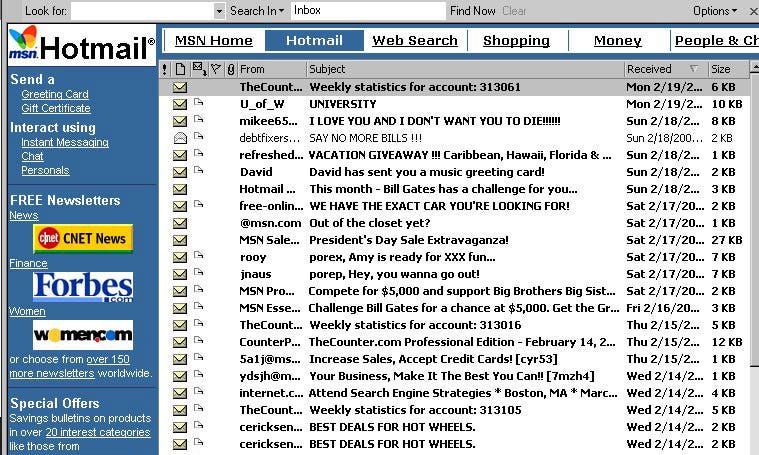
When email first came out, people had NO idea what they were doing. As the tech evolved, and companies like Hotmail came out, with the aim of making email easier, adoption began to accelerate.
We went from this:
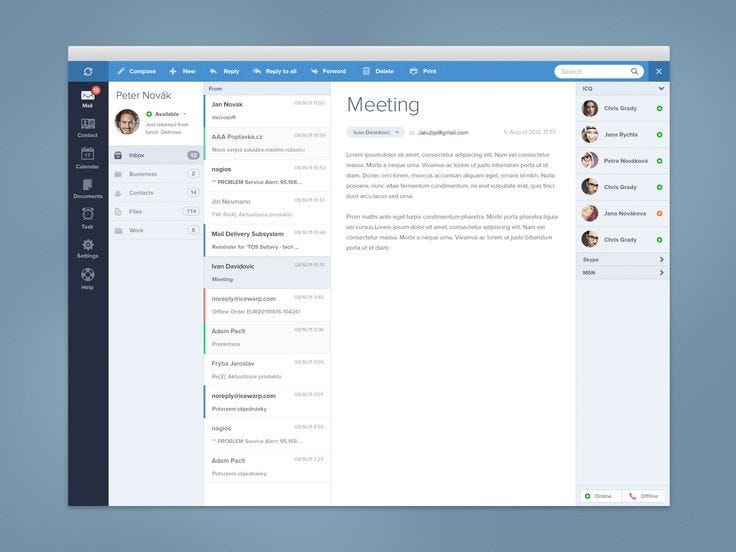
To this:
To now this:
The interface, the process and the user experience (UX) evolved there, as it will evolve in this new world too.
We are currently sending crypto like it’s 1984.
But that’s going to change, and this nascent tech will be used by hundreds of millions, and billons around the world.
So if you want to come play, come & do so.
Spend some time learning, get your head around what you’re doing before you do it, take responsibility for the areas in which you screw up, don’t do it again, and just understand the pro’s & cons + risks of what you’re doing.
It’s no different to the real world, but it’s an exciting new world. A new frontier, where there is lots of risks, and a hell of alot of opportunity.
Be safe out there ladies & gents!
___________________________________________________________________
If you enjoyed this post, please show it some love, give it a clap (or a few) and pass it around to anyone you think should have a read (I personally think anyone / everyone who’s thinking about being involved in crypto should be reading this)
Some of my stuff is a little blunt, but it’s done that way to jolt people into think clearer / deeper about what they’re doing.
Hope you got some value & feedback is always welcome!
Aleks
Co Founder @ Amber Labs & CEO @ Fabric.
___________________________________________________________________
You can also follow me here:
- Aleksandar Svetski - Medium
- Aleksandar Svetski (@AleksSvetski) | Twitter
- Aleksandar Svetski - Hacker Noon
Why do cryptocurrency hacks keep happening? was originally published in Hacker Noon on Medium, where people are continuing the conversation by highlighting and responding to this story.
Disclaimer
The views and opinions expressed in this article are solely those of the authors and do not reflect the views of Bitcoin Insider. Every investment and trading move involves risk - this is especially true for cryptocurrencies given their volatility. We strongly advise our readers to conduct their own research when making a decision.