Latest news about Bitcoin and all cryptocurrencies. Your daily crypto news habit.

Word Origin and History for “wallet”
- late 14c., “bag, knapsack,” of uncertain origin, probably from Old French,perhaps from Proto-Germanic *wal- “roll.” Meaning “flat case for carrying paper money” is first recorded 1834, American English.
As the popularity of cryptocurrencies has moved beyond the realm of technological curiosity exclusively populated by those with deep understanding of the protocols, there has been an increased misinterpretation of the tools and utilities available. There recently has been a proliferation of services made available to investors, traders and “holdlers,” and while there have been major improvements since the days when you had to download the whole blockchain and use a command line to access token holdings, there seems to be a lot of confusion about what exactly you are getting when you use these tools.
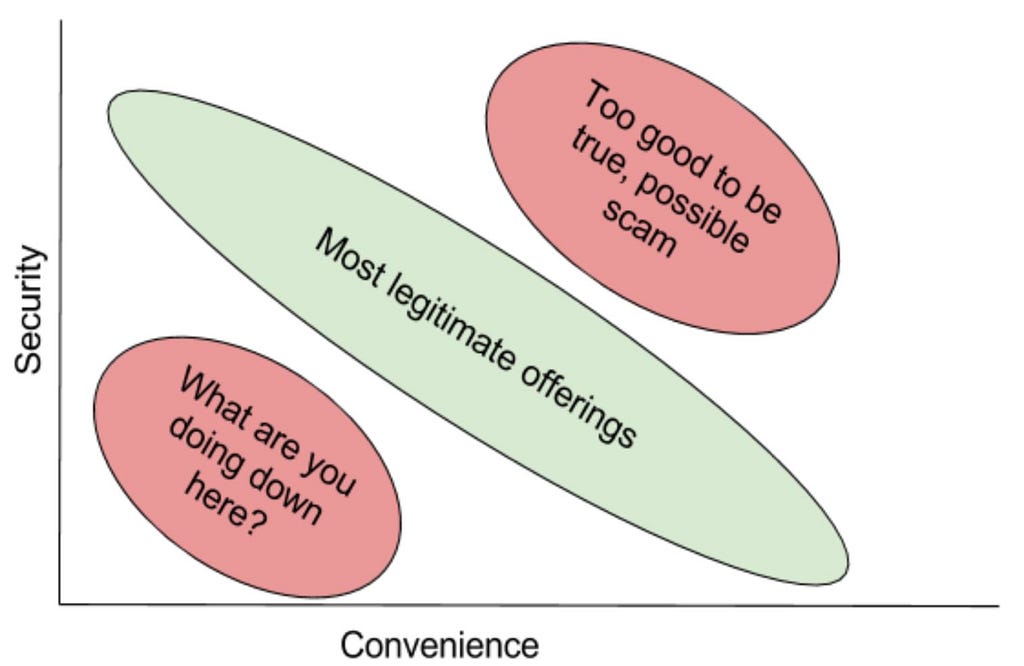
With an increase in options there comes an increase in potential for confusion and mistakes. It is easy to get excited about the technology and potential, but it is also easier to make a mistake based on a misunderstanding. Unfortunately, mistakes can lead to lost or stolen tokens. You can put the various services into a couple buckets that all offer some combination of security and convenience, but these variables are often negatively correlated. If you can decide what exactly you are trying to get out of using a service then you should be able to find something that works for you.
If you are reading this you have probably heard at least one person say that you MUST own and protect your private key. I am hoping to provide some context to understand not just why but also what counts as “owning” and “protecting”.
A cryptocurrency wallet provides utility — it’s a tool. It does not “hold” your tokens but merely provides an interface to interact with and manage your assets. Your private key gives you access to an account. You need both to get any value/utility out of your tokens. If you don’t have access or you don’t have a tool to perform actions then the tokens associated with that account are useless. Think of the wallet software as a cellphone and your private key as the SIM card. Neither is that useful on its own and the sim card just gives you access to value in an account.
When you are evaluating a wallet you need to know if you are storing your assets on chain or at a third party. How do you know? Third parties include all exchanges (Poloniex, GDAX, Bittrex) and other services like Coinbase and Abra. Do you use a username/password to log in? Were you never provided a private key to store? Saying yes to either one of those likely means that you are using a third party and trusting them.
Exchanges & 3rd Parties
Having your tokens on an exchange or held by a third party is like going into a casino. You are handing your money over and getting an IOU (chips in this example) in return. You have to withdraw your tokens from an exchange to transact with them outside of the exchange, just like you need to cash in your chips when you leave the casino. If someone steals all of the cash from the casino then your chips become useless. So while it is easier to just remember a password and take advantage of password recovery services with a third party, you rely on them to secure your assets.
When you deposit bitcoin to an exchange you NO LONGER own that bitcoin. The exchange has it and you are trusting it will be there if you went to withdraw it. You’re just shuffling IOUs around until you cash it in.
A hack or regulatory shutdown can leave you high and dry, but you also don’t need to worry about getting your own computer hacked or losing your key. More about the perils of trusted third parties in Nick Szabo’s “Trusted Third Parties Are Security Holes“.
Trusted Third Parties are Security Holes | Satoshi Nakamoto Institute
On-Chain Account
If you are not using a third party to store your assets you are likely storing them on chain: good for you! Storing on chain refers to having your transactions recorded directly on the blockchain. This doesn’t happen in an exchange setting since everyone is just moving the exchange IOUs back and forth. To use Ethereum as an example, anyone can download the tools necessary to interact directly with the blockchain — no web interface or wallet necessary. Once the toolkit is installed and a copy of the blockchain downloaded you can run commands from a command line and the resulting actions on chain are no different than using the front end interface at MyEtherWallet or any other Ethereum Wallet. For example, running $ geth account new will create a new account on the Ethereum blockchain. Once you do that similarly simple commands can be run to check token balances or send ether or other tokens to other addresses.
Having an account “on chain” is really just owning a private and public key pair. The private key is needed to prove ownership and send transactions or perform other actions on the account. The public key can be used to check balances or receive tokens. You should be very careful to protect your private key whereas your public key can be shared liberally. What most wallet services are doing is providing a nice interface to run all of these same commands. Instead of downloading the whole blockchain directly and running commands yourself, you get a nice button to click “create account” or “send tokens”. Services like MyEtherWallet are great for this. You can easily perform all of the actions you would like and your private key does not get stored in any central location. Sounds great, but now you are responsible for your private key. Are you comfortable storing that on your computer, on a piece of paper, on a USB drive? What if the account has $100 worth of tokens in it? $100,000? These are questions you need to think about. If you lose it or someone gains access to it, all of that value can disappear. Social hacking (phishing) is way easier and much more prominent than finding vulnerabilities in code which means there is a better chance you make a mistake that puts your assets at risk than someone finding a vulnerability in the software you are using. There are countless stories of folks typing in their private key to a fake site they followed a link to or falling for some sort of email scam.
Multi-Currency Wallets
A popular middle ground is multi-currency wallets (Jaxx and Exodus being some of the most popular). These services provide you with control of your own private key, but it is one private key used across multiple blockchains. There is an abstracted layer in between which makes things easier for the end user; you don’t need to continually enter your private key and you can go to one place to perform transactions with multiple tokens on multiple chains. That extra layer though opens up another vulnerability. An issue was exploited in the local Jaxx wallet that led to people losing tokens earlier this year and there have been multiple issues leading to hundreds of millions of dollars of token value lost in hacks to the Parity wallet software. Making anything more complicated makes it more vulnerable. MyEtherWallet is great because it is simple and you know the risks. There is work being done in the multi-currency wallet software to make it easy to use, yet these very advancements could present vulnerabilities. Such is the nature of software development. Jaxx has a great mobile app though, making using crypto in everyday life much easier. MyEtherWallet isn’t ideal for quick transactions on the go since it is not optimized for mobile.
 Perils of adding too much complexity to a wallet
Perils of adding too much complexity to a wallet
Think of the wallet you have in your pocket or purse. It’s good for carrying cash — maybe some coupons, rewards cards, credit cards — but there’s a pretty standard size of what will comfortably fit. Silver coins or a gold bar don’t fit into a wallet very well, and if you try to put too many different things in there you are going to have problems. What it does provide though is convenience and control. You can keep it with you and put whatever you want in it. Consider the safe. Maybe you have one at home. You can put anything you want in it, but how secure is it really? It is not very convenient to transact or trade the assets you have in the safe. You can use the safety deposit box at your bank, but it is still only of a certain size. The bank could be robbed, and you need to go through a whole rigamarole to access whatever you have in it. You can put whatever the hell you want in a storage locker, but if you have diamonds or a prized stamp collection you probably want to add another layer to store them so they don’t get lost. Just like with physical assets, you need to think about what your intention is — how valuable is it? How much do you trust 3rd party options? How often do you really need to access the tokens?
Storage Options
Exchange/3rd Party
Can trade multiple tokens on multiple chains. Use username/password to access. You do not own your private key and funds are all held in a central exchange wallet.
Multi Currency Wallet
You own your private key but software enables you to use the same root key to secure tokens across multiple chains. Ex: Jaxx, Exodus
Web Wallet
Chain-specific, web-hosted wallet. Some store your private key behind a password (Metamask), others require you to store your private key and upload it before performing any actions on the account (MyEtherWallet)
Local Wallet
Software installed locally to perform actions on a specific blockchain. Private Key still needs to be stored where wallet can access it
Hardware Wallet
Private Key is stored in a physical offline device. Integrates with wallet software/web wallets. Ex: Paper Wallets, Ledger Nano S, Trezor
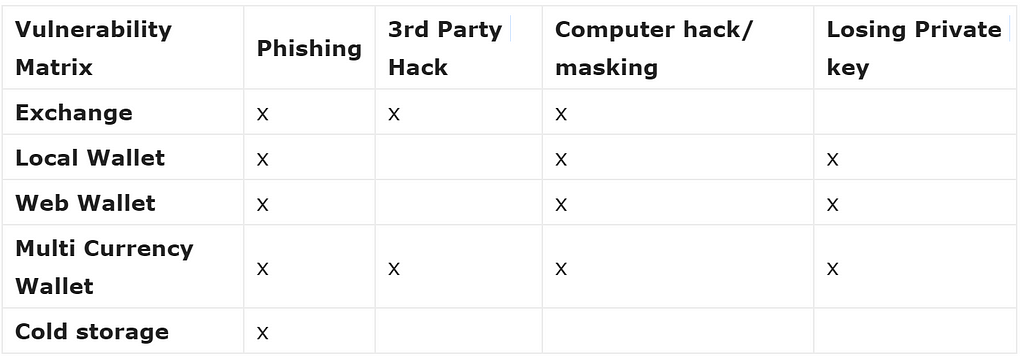
Attack Vectors
Phishing
Basically tricking you into giving up the information needed to access your account. Ex: An email to a link to put in your private key or exchange username and password.
3rd party Hack
Malicious parties exploit a vulnerability and drain funds. Ex: Parity multi-sig hack / Mt. Gox
Computer Hack/Masking
Actions taken on your computer are tracked, so your key or passwords are stolen as you enter them. Someone accesses your computer and finds files with saved passwords/keys.
Losing your Keys/Password
Losing stored private keys or forgetting passwords and seed phrases.
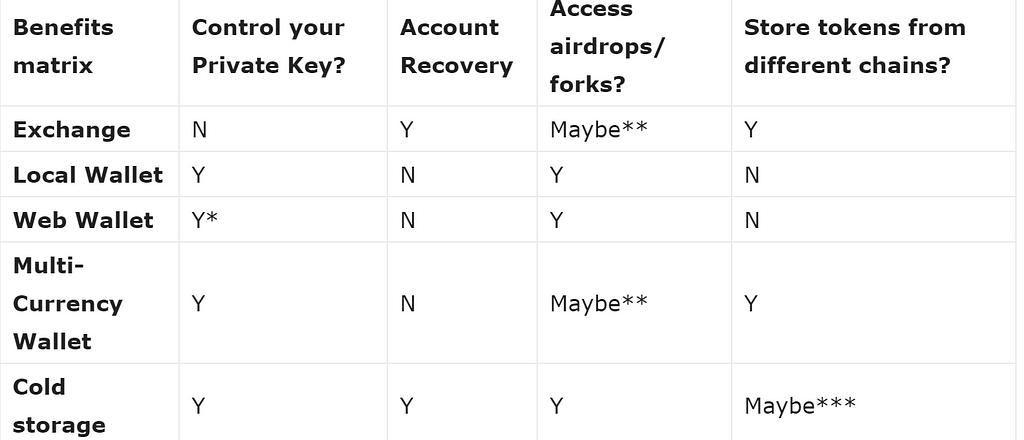
Benefits
Control Private Key
This means you can always take your key and access your tokens using another piece of software or even by interacting with the chain directly.
Account Recovery
If you forget your password or lose your private key there is a service to help you recover access
Access Airdrops/Forks
When a hard fork happens or a token is airdropped to holders of another token, you only receive access to those new tokens if you own your private key.
Store Tokens from Different Chains
Ethereum and Bitcoin are different blockchains. You cannot send Bitcoin on the Ethereum blockchain and you cannot send Ether on the Bitcoin blockchain. You can issue new tokens on a blockchain, and access them with the same account.
*You may need to go through some conversion to make your wallet key work as an on-chain key
**Depends on if exchange/wallet software integrates it.
***Ledger Nano and Trezor both support tokens from multiple chains but different software wallets are used.
To find find the appropriate balance for yourself you need to be honest about your comfort levels with each option. How tech savvy are you? How well will you sleep at night if you know a USB drive in your desk drawer controls access to your digital assets and they are GONE if you lose it? Are you going to feel left out if you don’t receive every airdrop or hardfork token? Eventually there will be better offerings, but there wouldn’t be so much upside right now if it was easy. Read up, ask around, and when trying out a new option always, always, always test with a conservative amount first.
Wallets, Exchanges, and Attack Vectors — How Should You Store Your Crypto-Assets? was originally published in Hacker Noon on Medium, where people are continuing the conversation by highlighting and responding to this story.
Disclaimer
The views and opinions expressed in this article are solely those of the authors and do not reflect the views of Bitcoin Insider. Every investment and trading move involves risk - this is especially true for cryptocurrencies given their volatility. We strongly advise our readers to conduct their own research when making a decision.