Latest news about Bitcoin and all cryptocurrencies. Your daily crypto news habit.

This seemingly harmless USB air purifier device if modified by someone malicious can damage your computer irreparably. Know the threat of the USB Killer, its history and how it is possible to buy it online ready to use or improvise it from low cost components.
A few years ago, DarkPurple a Russian hacker demonstrated the “USB killer 2.0” the USB equivalent of an RJ45 connector wired into mains power. Once connected, the USB device sends high-voltage negative DC through a USB port until it fries the circuitry of the host device. The USB Killer is a simple device with just a FET, a few high voltage caps, a DC/DC converter, and a USB connector. Plug this device into your computer and -220V is dumped directly into the USB signal wires. This will kills your laptop dead.
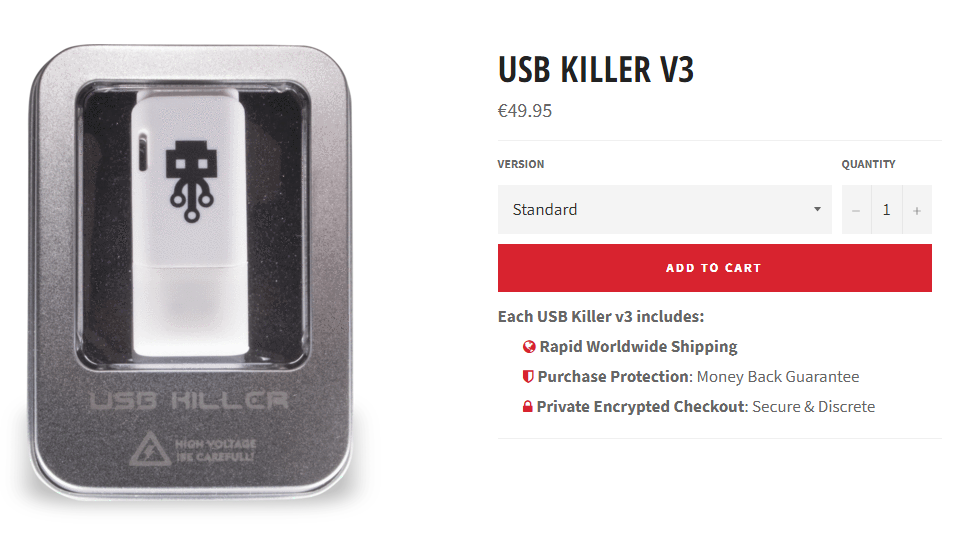
Over the years we’ve seen the USB Killer evolve as a crowdfunding campaign run by a company in Hong Kong make a similar device commercially available. The “USB Kill 3.0”, marketed as a testing tool for administrators looking to protect their systems, sells for €49.95 Euro (around US $60).
Despite the obvious nefarious potential for the tool, its public release at least appears well-intentioned. Or at least that’s what the manufacturer says. The USB Killer was developed by a security hardware team based in Hong Kong, who first publicized the vulnerability it targets over a year ago, and developed an early prototype.
But the team was deeply frustrated to see consumer electronics developers take little action on closing the vulnerability. According to the team, Apple is to date the only manufacturer that protects their devices against this so-called USB surge attack.
“Despite adequate warning, and time to respond,” the USB Killer team writes, “the majority of consumer-level hardware manufacturers choose not to protect their customer’s devices. We are disheartened by this lack of respect for customers.” Their emphasis, not ours. I have no idea what this actually means.
According to USB Killer 3.0 manufacturer tests, over 95% of devices are affected by a USB power surge attack. Almost all consumer-level hardware fails somehow when tested against the USB Kill. The most frequent outcome is the complete destruction or permanent damage of the device (laptops, smart TVs, car audio, etc).
More recently, Kedar Nimbalkar found that it is very easy to modify a $3 USB Air Purifier that in itself has the harmless aspect of a thumb drive in the home equivalent of a USB killer, only for the cost of $ 3 and a small modification.
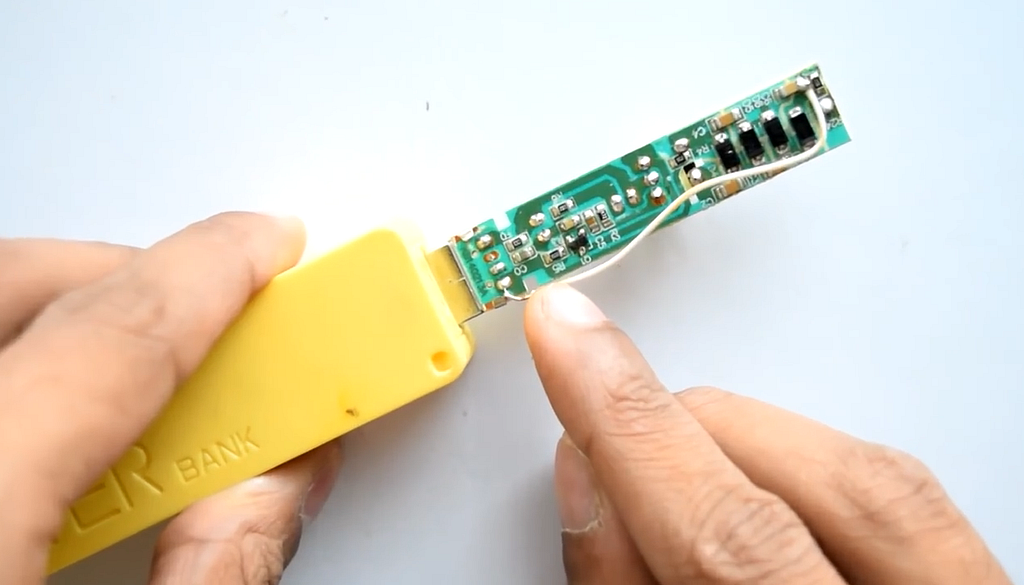 Air purifier turned into a USB Killer
Air purifier turned into a USB Killer
Ionizer purifiers use high voltage electrostatics charged electrical surfaces or needles to generate electrically charged air or gas ions. These ions attach to airborne particles which are then electrostatically attracted to a charged collector plate. This mechanism produces trace amounts of ozone and other oxidants as by-products. Permanently mounted home and industrial ionizer purifiers are called electrostatic precipitators.
Nimbalkar found that if you disconnect the charged needle and route the output from a capacitor to either of the two data lines (not normally used in this device) you create a device equivalent to a USB Killer, but still harmless looking.
While not the original USB Killer it is still a very dangerous device and it would at least fry the USB port and kill the USB controller. The high integration and miniaturization of the components of modern devices such as laptops makes them much more vulnerable than the old desktop computer in which the USB controller was a physically separate from CPU. On modern system on chip (SoC) is an integrated circuit that integrates all components of a computer or other electronic systems from CPU to USB Controller.
While it may seem like a fun idea to make one of these devices it is important to test it only on some old computer of our legal ownership, as bringing a premade destructive device proves premeditated intent which escalates your practical joke to criminal damage in most jurisdictions around the world.
So, Listen, I get it. When you find a random USB stick laying around somewhere, it’s tempting to snatch it up and plug it in to your computer. Maybe it’s curiosity or some users connect the drive with the altruistic intention of finding the owner.
But that’s exactly the wrong thing to do. It’s a really bad idea to plug anything of unknown origin into your computer. During a 2016 study out of the University of Illinois investigated the anecdotal belief that end users will pick up and plug in USB flash drives they find by completing a controlled experiment in which researchers drop 297 flash drives on a large university campus. They found that the attack is effective with an estimated success rate of 45–98% and expeditious with the first drive connected in less than six minutes
One can imagine that maybe it is better not to open the files, or you may think you have some security knowledge and try to mount it as read only from Linux, however if the device is a USB Killer you will get an unpleasant surprise.
That’s right, guys, do not connect anything USB to your computer you if you do not know where it came from, especially if it seems to be an air purifier.
This $3 DIY USB Device Will Kill Your Computer was originally published in Hacker Noon on Medium, where people are continuing the conversation by highlighting and responding to this story.
Disclaimer
The views and opinions expressed in this article are solely those of the authors and do not reflect the views of Bitcoin Insider. Every investment and trading move involves risk - this is especially true for cryptocurrencies given their volatility. We strongly advise our readers to conduct their own research when making a decision.