Latest news about Bitcoin and all cryptocurrencies. Your daily crypto news habit.
According to Chinese internet security firm Qihoo 360 Netlab, hackers have stolen $20 million in ether from poorly configured Ethereum mining rigs and third-party applications. Experts at the firm say the cyber-attacks target unsecured Ethereum nodes on the Internet.
Details of the Hack
On March 15, Qihoo 360 Netlab alerted the cryptocurrency community to the activities of hackers scanning the Internet for unsecured Ethereum nodes. At the time, the alleged cybercriminals had stolen 3.96 ETH.
Remember this old twitter we posted? Guess how much these guys have in their wallets? Check out this wallet address https://t.co/t4qB17r97J $20,526,348.76, yes, you read it right, more then 20 Million US dollars https://t.co/SXHrdTcb6e
— 360 Netlab (@360Netlab) June 11, 2018
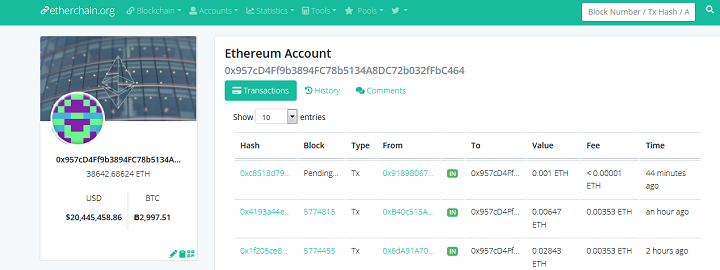
However, recent findings have unearthed another hacker who has managed to steal an even more considerable amount of ether. By hijacking unsecured Ethereum wallet apps, the hacker has managed to siphon off 38,642 ETH worth about $20 million. The image below is the address of the suspected hacker:
The hack exploits the ability of Remote Procedure Call (RPC) interfaces running on port 8545 to access sensitive miner and wallet information. The RPC provides third-party access to this data via a programmatic API. If left unsecured, a hacker could gain access to miner/wallet funds. Thus, the RPC is usually disabled by default on most Ethereum-based apps.
Safeguarding Your Ether Holdings
Whether by omission or commission, some app developers — in tinkering unnecessarily with their apps — have opened up the unsecured node vulnerability. With the astronomic rise in cryptocurrency prices last year, it seems more hackers are incentivized to conduct rigorous Internet scans in search of unsecured cryptocurrency holdings.
Qihoo 360 Netlab reports that there is an increase in scans for RPC interfaces on port 8545. With the success of the $20 million heist, it is safe to assume that more cybercrooks will join the attack.
In May 2018, reports emerged of Satori Botnet targeting exposed Ethereum miners. There are numerous hacking resources available on GitHub to automate port 8545 scanning exploits. According to Qihoo 360 Netlab team:
If you have honeypot running on port 8545, you should be able to see the requests in the payload, which has the wallet addresses. And quite a few IPs are scanning heavily on this port now.
As for users of Ethereum-based apps, they are advised to check that their RPC interfaces are not left unsecured on the Internet.
Have you checked to see if your Ethereum-based apps and mining rigs are properly configured? Do you think other blockchains-based apps are vulnerable to this same attack? Share your views with the community in the comment section below.
Images courtesy of Shutterstock, Twitter/@360Netlab, and etherchain.org.
Disclaimer
The views and opinions expressed in this article are solely those of the authors and do not reflect the views of Bitcoin Insider. Every investment and trading move involves risk - this is especially true for cryptocurrencies given their volatility. We strongly advise our readers to conduct their own research when making a decision.