Latest news about Bitcoin and all cryptocurrencies. Your daily crypto news habit.
Beyond the Hype: An Institutional Framework for Evaluating DeFi Protocols
Did you know there are hundreds — if not thousands — of DeFi protocols out there, spread across dozens of Layer 1 and Layer 2 networks? With so many options, it might seem tempting to deploy capital into a promising project that’s just been pitched. But what does it really take to evaluate if a protocol is fit for large-scale deployment? For institutions, this goes far beyond a quick market analysis. It requires a thorough look at sustainability, security, and long-term growth potential. Let’s dive into the core factors that can help determine whether a protocol deserves serious consideration for capital deployment.
In DeFi, protocols evolve quickly to capture liquidity and retain user interest, often adapting at a pace that can be challenging for institutions with regulatory and administrative constraints. Institutional deployments take time — weeks, sometimes months — to prepare, which means short-term strategies aren’t always practical given the upfront costs involved. Instead, institutions need to focus on the sustainability and long-term viability of protocols. This article will walk through essential factors to consider, from evaluating a protocol’s incentives and security to assessing the capacity for risk-managed deployment.
Initial Protocol Evaluation
Protocol Mechanics and Tokenomics Structure
Protocol Mechanics
When assessing a protocol for potential deployment, understanding its mechanics is key to gauging sustainability. Some essential questions to consider include:
- Will these mechanics drive lasting economic value for users and the protocol itself?
- Do they depend heavily on token incentives to function?
- Is there a unique design appeal to attract and retain users?
- Can the mechanics adapt as broader DeFi macro conditions change?
The goal here is to ensure the mechanics are resilient. Protocols that lean too heavily on token incentives or align themselves closely with fleeting liquidity trends may see rapid initial growth, but often struggle when narratives shift or incentives fade.
Tokenomics
Tokenomics are closely tied to a protocol’s mechanics and play a significant role in its long-term viability. Key factors to assess include the current stage of the token distribution process and its impact on strategies reliant on token incentives for returns. Specific considerations include
- Supply earmarked for incentives and the incentive schedule
- Market cap vs fully diluted value (fdv) helps determine the potential dilution the token can handle before slippage can impact returns
- Unlocks of vesting tokens
Together, these points help institutions determine the feasible deployment size without becoming so significant a holder of the incentive token that they risk influencing prices when realizing returns.
Security
Evaluating protocol security is a nuanced process that can vary based on an institution’s deployment size and risk tolerance. For a baseline assessment, both technical and economic security measures are essential.
Technical
On the technical side of protocol evaluation, some of the key items to consider are:
- Has the protocol been audited?
- What did those audits cover?
- Have new features been implemented since the last audit?
- If the protocol is a fork, were any known issues in the original addressed?
As protocols grow more complex, specialized audits often target specific functionalities. For robust technical security, it’s important to confirm that the entire protocol has been audited and that any recent updates have also undergone review.
Economic
The next section will go into more detail on reducing economic risk exposure in DeFi, but here are a few overarching security measures to consider when deploying into protocols:
- What type of oracle is used for assets?
- Do the liquidation mechanics make sense?
- What are all the assets that the strategy is exposed to within the protocol?
While external companies often review these factors, fast-moving protocols focused on launching new assets and features may sometimes overlook them. Oracles, for example, can vary widely in pricing mechanisms, and without an industry standard, this can lead to miscalculated risks. Liquidation mechanics — like collateral factors and liquidation bonuses — should be configured to prevent users from profiting by liquidating their own positions. Additionally, protocols may introduce low-liquidity assets that increase price manipulation risks, potentially exposing users to unexpected losses.
Protocol Capacity for Deployment
If a protocol is deemed secure after an initial review, a second evaluation needs to be done on the protocol’s capacity. Here, institutions can have more control over their economic risk management and develop strategies that fit their risk/reward profile.
Deployment Feasibility
The first step in evaluating protocol capacity is to determine the realistically feasible deployment size into the protocol and how long it will take to return profits given any costs that will be incurred.
Strategy Entry and Exit
Entry and exit costs for a position can vary depending on the strategy, as liquidity and market dynamics often differ between entry and exit points. For example, in a leveraged staking strategy on a lending market, a user typically deposits a liquid staking token (LST), borrows ETH, converts the borrowed ETH back into an LST, and then redeposits it in the lending market. This process is often looped multiple times to maximize yield from the LST. However, converting ETH into an LST generally incurs less slippage than converting back from LST to ETH, which means a quick exit could result in high slippage costs when swapping LST back to ETH to repay debt, ultimately lowering the strategy’s realized returns.
While entry and exit costs can shift with market conditions, understanding the maximum capacity for entering and exiting a position beforehand helps manage economic risks. This allows users to adjust their deployment size to avoid unnecessary costs associated with liquidity constraints and market slippage.
Liquidity of Returns
On the other side of a strategy’s costs, understanding the liquidity of the yields earned on a position will help users estimate the size that they will deploy. As mentioned above, it is common that some of the yields earned in a protocol will be incentives from other tokens. If the user wants to realize their earned yields into the asset that they deployed, they will need to exchange these tokens in the market. If there is little liquidity available for these tokens, then the user will incur slippage that will reduce the realized yields from the strategy.
Estimating the amount of returns that will be in these secondary tokens and how frequently the user will plan to realize yields back into their deployed asset will help determine an optimal deployment size to achieve maximum returns.
AMM Deployment Considerations
In addition to the general economic risks considered in the previous section, there are specific risks that pertain to providing liquidity into automatic market makers (AMMs). These primarily focus on the liquidity size and distribution of the assets in a pool and include:
- Current and historical pool liquidity
- Pool token distribution
- Market depth
With the three metrics above, a user can model the capacity at which they can deploy into a pool with low cost impacts. In addition to capacity measurements, one can understand the potential longevity of the deployment before they need to withdraw their position to avoid high exit costs.
When entering an AMM pool that allows one-sided entry (entering into the pool with only one token instead of both), market depth can help you understand the slippage you will incur based on the size of deployment. In the background, a one-sided deployment will trade part of the deployment into the other token. A market with thin liquidity around the trading price can incur high slippage and price impact costs.
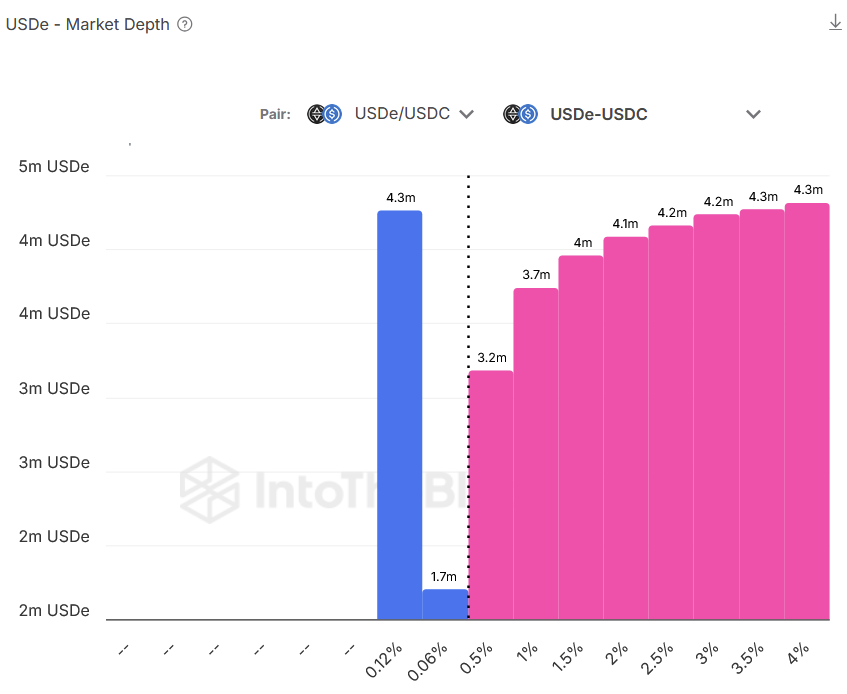
Source: ITB Risk Radar
Pool liquidity and concentration are key indicators of stability, helping to determine both the capacity that can be deposited and the duration of the deployment. Pools with stable liquidity and consistent token concentrations are generally more suitable for large deployments, as the pool’s conditions at entry are likely to remain similar upon exit. This stability allows for clearer, more predictable estimations of deployment costs, minimizing unexpected variations in cost due to liquidity shifts.
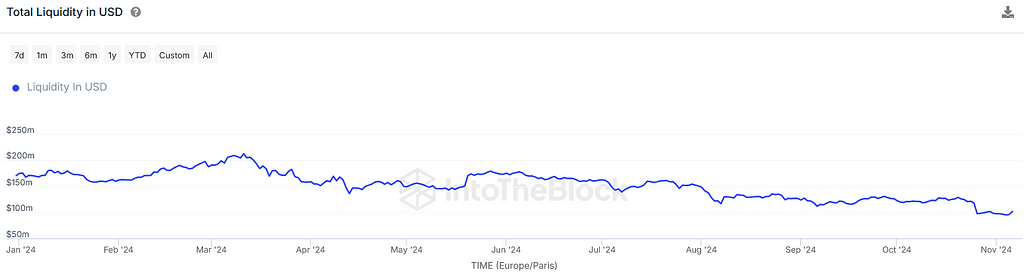
Source: ITB Analytics

Source: ITB Risk Radar
A useful heuristic for assessing stability is to review the pool’s historical liquidity over a timeframe comparable to the planned deployment period; this can help ensure that the pool’s conditions will likely support the deployment size with minimized cost impact.
Lending Deployment Considerations
Lending protocols also have specific economic risks that can pertain either to lenders or borrowers:
- Lenders: Available liquidity
- Borrowers: Distance from Interest Rate Model kink
- Historical Averages for the above
An often-overlooked economic risk for large suppliers in lending markets is the potential for their liquidity to become “locked” when it is borrowed out. As lending markets grow more efficient, this risk becomes increasingly prevalent. While withdrawing funds can trigger an increase in interest rates that may eventually release more liquidity, this process can be too slow if the deployment is part of a larger, time-sensitive trade. In such cases, having immediate access to funds is critical to avoid disruptions and potential losses.
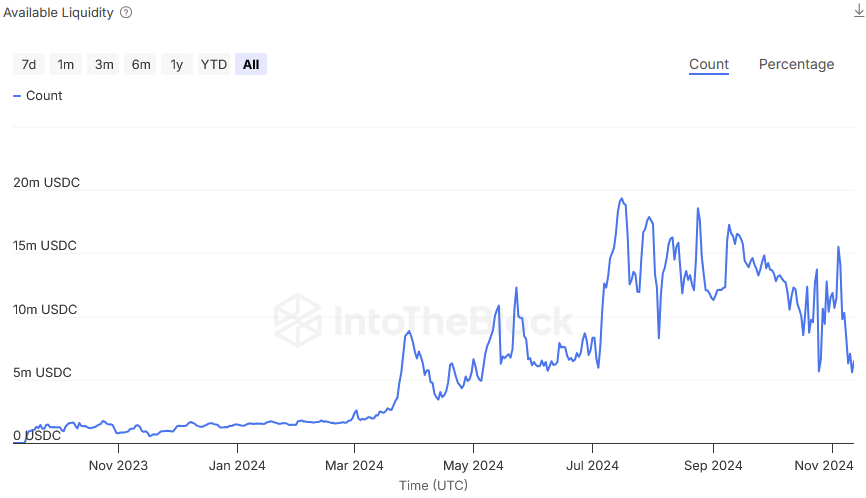
Source: ITB Risk Radar
For this reason measuring lending capacity is often best determined by the available liquidity in that market. Taking the rolling average of a specific period of time can provide a good understanding of what the general max capacity of a deployment should be while remaining liquid.
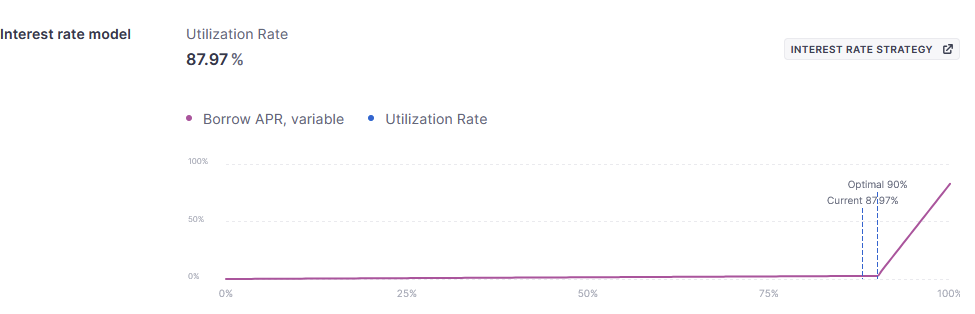
Source: Aave
For borrowers, one of the most reliable metrics for determining borrowing capacity in a lending market is the distance to the “kink” in the interest rate model. Strategies involving borrowing should closely monitor available liquidity as it approaches this kink, as crossing it can lead to sudden spikes in borrowing rates, potentially causing liquidations or reducing returns. Similar to evaluating available liquidity for lenders, assessing a rolling average of liquidity before reaching the kink provides a strong indicator of the strategy’s maximum sustainable capacity.
Summary
Following the sections above, a quick checklist of items to review in protocols can help institutions evaluate and quickly iterate through protocols before a more in-depth security and deployment analysis:

Running through this checklist will identify many large questions or potential red flags and can help filter out protocols that will not be feasible for deposit based on the institution’s deployment size.
Are you looking for more insights? Download our latest research paper here, or contact us to discuss your specific situation.
Beyond the Hype: A Framework for Institutional Investments in DeFi was originally published in IntoTheBlock on Medium, where people are continuing the conversation by highlighting and responding to this story.
Disclaimer
The views and opinions expressed in this article are solely those of the authors and do not reflect the views of Bitcoin Insider. Every investment and trading move involves risk - this is especially true for cryptocurrencies given their volatility. We strongly advise our readers to conduct their own research when making a decision.