Latest news about Bitcoin and all cryptocurrencies. Your daily crypto news habit.
 It’s your girlfriend’s birthday and you want to send something special to her, you have bought some nice & rare chocolates especially for her. As she lives in another city, you need to parcel them (these chocolates doesn’t melt, that’s the interesting part about them). There’s just one parcel company and you can’t trust them with such a special gift. What can you do?
It’s your girlfriend’s birthday and you want to send something special to her, you have bought some nice & rare chocolates especially for her. As she lives in another city, you need to parcel them (these chocolates doesn’t melt, that’s the interesting part about them). There’s just one parcel company and you can’t trust them with such a special gift. What can you do?
To be honest, you don’t have a lot of options to explore. Think fast, time is running out. The first option that comes to your mind is -
Go and deliver it yourself.
No, not this time. If that is the option we are getting at then I will be finished writing the article. What can you think of next?
Put the chocolates in a box, lock the box and parcel them.
Seems legit, but your girlfriend don’t have the key and obviously you can’t just parcel the key. What next can you think of?
The solution that I am going to suggest now will require multiple to and fro rounds of the same chocolate box between you and your girlfriend. Let’s hop on to the solution without wasting much of time as “time is of the essence” right now (you can’t keep your girlfriend waiting).
- You put the chocolates in a box, lock the box with LOCK A.
- You will keep the KEY A with you.
- Parcel the box through the courier company. (The box is locked with LOCK A, the key to open it i.e. KEY A is with you only).
- The box reached your girlfriend (she is excited!)
- You called your girlfriend and asked her to lock the box with her own lock.
- She locked the box with LOCK B.
- She kept the KEY B with her.
- The box have now been parcelled to you using the services of the same courier company.
- The box currently has two LOCKS (LOCK A and LOCK B), the courier company can’t open them as they don’t have any of the keys with them.
- The box reaches you, you opened the LOCK A with KEY A. The box still have LOCK B on it (the KEY B of LOCK B is with your girlfriend and nobody else in this universe).
- You parcelled the box again back to your girlfriend (remember the box is locked with LOCK B, the key to open this box i.e. KEY B is with your girlfriend only).
- The box reaches your girlfriend and contains just one lock, i.e. LOCK B.
- Your girlfriend opened the box with KEY B.
- Tada! She can enjoy all the chocolates and is secretly sending you kisses!
- The courier boy is left scratching his head.
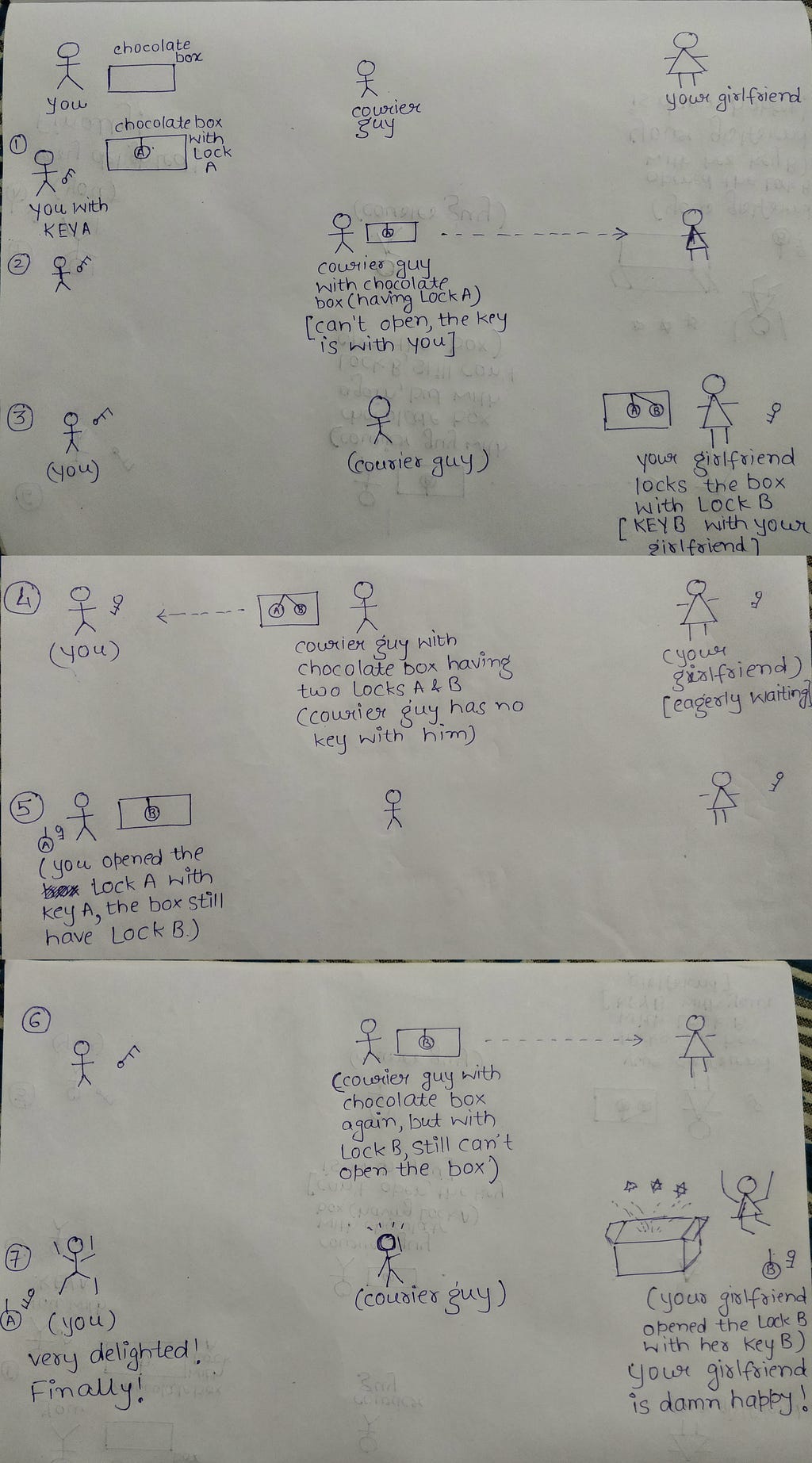 Explaining the concept with the help of a flow diagram (apologies for the messy parts).
Explaining the concept with the help of a flow diagram (apologies for the messy parts).
Moving on to some serious stuff
Encryption is no different from the above example, in fact, what I just explained is an analogy to Asymmetric Encryption technique. As https://crptography.io explains -
Asymmetric cryptography is a branch of cryptography where a secret key can be divided into two parts, a public key and a private key. The public key can be given to anyone, trusted or not, while the private key must be kept secret.
Let’s try to explain it in Layman terms -
- You and your girlfriend have your own Private Keys (KEY A & KEY B).
- Neither you nor your girlfriend exchanged those keys with each other through any medium.
- You secured the data with your own Private KEY A and your girlfriend did the same with her Private KEY B.
- You sent the data through an untrusted channel (the courier guy).
- Eavesdropper couldn’t figure out the data (it was always secured with LOCK A/LOCK B/Both).
- Intended receiver got the data at the end.
This is the essence of Encryption. And the above example explains the same more or less.
What actually happens in Asymmetric Encryption?
Let’s consider a hypothetical situation, there are three users, User A, User B and User C.
User A will generate a pair of public and private key using some mathematical operation. Lets call this pair as PUB-A (public key of A) and PRI-A (private key of A). Similarly User B will generate another pair PUB-B and PRI-B. And User C with PUB-C and PRI-C.
A little intro about Key pairs- A public-private key pair implies that if we lock (encrypt) the data with one of them, it can only be unlocked (decrypted) with the other one. i.e. if we encrypt the data with a Private Key, it can only be decrypted using its paired Public Key and nothing else. Similarly if we encrypt the data with a Public Key, it can only be decrypted using its corresponding Private Key.
User A will keep PRI-A with him and broadcast PUB-A to the world, both User B and C will receive this, similarly User B will keep PRI-B with him and broadcast PUB-B to the world. User C will do no different.
Now User A has- PUB-A, PUB-B, PUB-C, PRI-A
User B has- PUB-A, PUB-B, PUB-C, PRI-B
User C has- PUB-A, PUB-B, PUB-C, PRI-C
User A wants to send some data to User C but doesn’t want User B to see that data, now the following chain of events will ensure this -
- User A will lock (encrypt) the data with PRI-A (which can only be decrypted using PUB-A).
- But since PUB-A is with User B as well, the data needs to be more securely encrypted.
- User A will then encrypt the data again with PUB-C (this can only be decrypted/opened with PRI-C). And PRI-C is only with User C.
- The data is now secured with PRI-A and PUB-C. (can only be opened using PUB-A and PRI-C).
- User B was eavesdropping, found the data, and tried to open the data with the keys available to him, i.e. PUB-A, PUB-B, PUB-C, PRI-B. He has PUB-A, but he still needs PRI-C to make sense of the data). Fortunately he doesn’t have that.
- Data gets to User C, he has the following keys PUB-A, PUB-B, PUB-C, PRI-C, he needs PUB-A and PRI-C to open the data. Fortunately he has, he can open the data, and it all makes sense to him.
Curious readers will ask that User A can just lock the data with PUB-C and then only User C can open it with PRI-C. Correct! But, User C can never be sure if it was actually User A who had sent the data. Hence User C tried opening the data with PUB-A, which can only be locked using PRI-A, and since PRI-A is with User A only, User C can be sure that this actually came from User A and not from any impersonator. This can also be done using signed certificates, if we use signed certificates and rely on a third party to let us know the true origin of data then User A needs to encrypt the data only with PUB-C, and contact the third party to sign the data with a certificate stating that the origin of data is User A. When User C receives the data, it checks the certificate and verifies the true origin of it, and only after that it will open the data with PRI-C.
This in short is the true essence of Asymmetric Encryption Technique. Will be writing another article in this Cryptography Series. Until then, remember -
What happens in Vegas ends up on YouTube. — Tim LeberechtSo be safe and secure!
PS: I hope you like my article, correct me if I am wrong anywhere.
Asymmetric Encryption explained with the help of chocolate boxes. was originally published in Hacker Noon on Medium, where people are continuing the conversation by highlighting and responding to this story.
Disclaimer
The views and opinions expressed in this article are solely those of the authors and do not reflect the views of Bitcoin Insider. Every investment and trading move involves risk - this is especially true for cryptocurrencies given their volatility. We strongly advise our readers to conduct their own research when making a decision.
