Latest news about Bitcoin and all cryptocurrencies. Your daily crypto news habit.
On Saturday morning, I woke up to find a number of spam-looking emails in my gmail account inbox…sent by me. Only, I hadn’t sent any of these.
At first I thought that someone was sending me spam with the name of the sender simply set to the word “me”, but knowing that Gmail does a pretty good job of filtering spam from unknown email addresses, I decided to investigate.
Along the way, I discovered that this had happened to hundreds (if not more) of other people’s Gmail accounts.
Split Personality Spammer
Lo and behold, when I clicked on the sender to view more details, my email appeared as the sender. Even more concerning, these spam emails actually appeared in my Sent items folder as well, suggesting that I had indeed been sending them out from my email account.
Unless I had some sort of split personality and one of my personas was getting up in the middle of the night to send myself spam emails (far-fetched, even for me), it seemed like my Gmail account had been hacked.
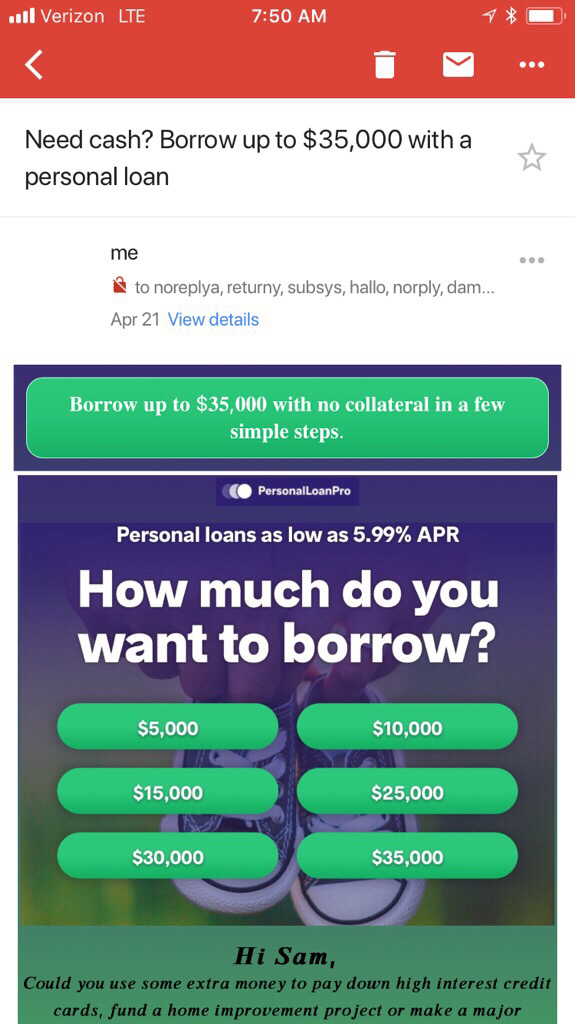 Sample image of the spam email (not mine).
Sample image of the spam email (not mine).
Naturally, the first thing I did was check whether my Google account had any suspicious activity like someone logging in from a new device (it didn’t), but to be safe, I reset my password and logged myself out of all devices. I then marked the emails as spam (which worried me, because it could mean I wouldn’t actually receive any future emails I sent to myself), and went to bed.
The next morning, I woke up and discovered the exact same thing had happened again. The emails that I was getting usually revolved around cryptocurrency scams, weight loss scams, and financial loan scams — and all of them were from me.
I took a look further into it and found that there were a bunch of fake email address recipients (things like my full name @salesforce.com, which I’m quite sure isn’t an actual email, plus other fake emails like norply@mxtoolbox.com), and that the sender was definitely my Gmail account…except that it had the words “via Telus” added to the end of the sender. Further, under the security label of the email, Gmail warned that the email was not encrypted — a message that does not usually appear in emails I send myself.
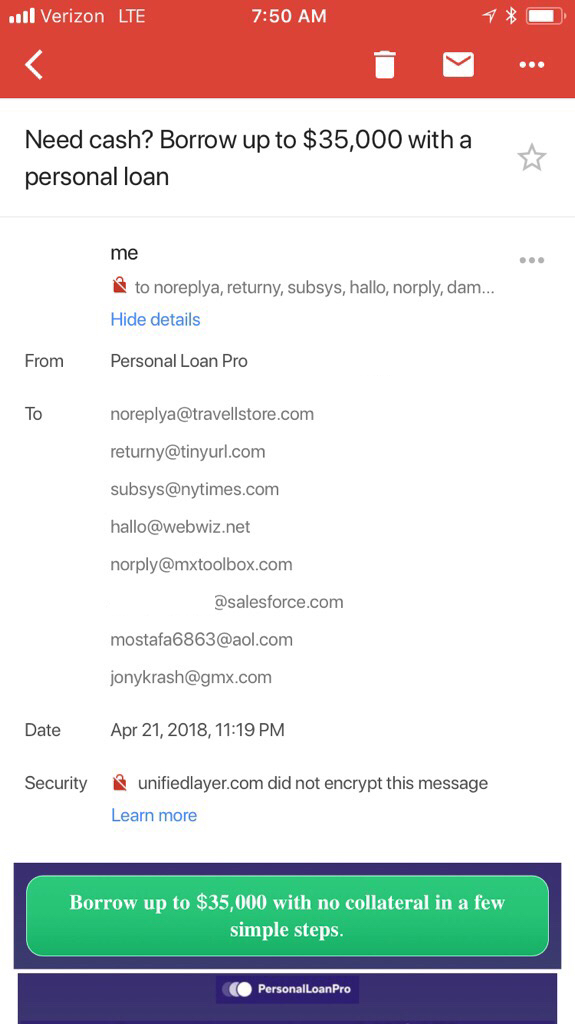 Sample image of the spam email (again — not mine).
Sample image of the spam email (again — not mine).
Telus The Truth
When I went to the office on Monday, I asked our Head of Engineering if he had encountered the same thing. After showing him the email, he explained that what had happened was that my email had been spoofed — not hacked — thanks to a Canadian telecommunication company called Telus.
Long story short, Telus appears to have allowed all IP addresses to send spoofed emails as though they were coming from its server. As a result, the hacker(s) were able to make emails appear to be sent from the Telus server, but internally in the email header, changed the sender to be my Gmail address. When the Gmail server was notified that an email was incoming to my inbox (with other recipients listed, likely to make the email look more authentic, even though the email addresses look quite blatantly fake), it queried Telus’s domain DNS server to check to see if the email server that sent the email was permitted to send messages on its behalf (which was answered in the affirmative because of Telus’s settings)…and then delivered them straight into my inbox. Click here for a more in-depth explanation.
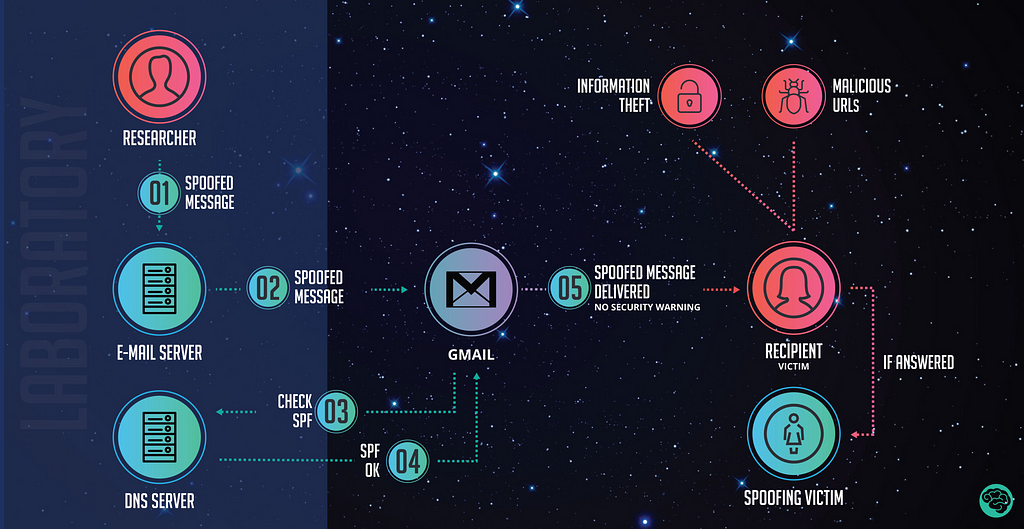 Image source: here.
Image source: here.
Upon receiving an email that appeared to be sent by me, Gmail automatically filed a copy of it in my Sent items — hence why they were appearing there as well.
This ability to spoof Gmail servers was apparently previously raised with Google by a researcher last year — but the company responded by saying that because it “did not substantially affect the confidentiality or integrity of Google users’ data”, it would not be taking any action.
However, this latest incident caused a furore online, with hundreds of Gmail users posting on numerous threads about the issue — including those who already had high level security settings and two factor authentication implemented (which indicated that it was not a hacking issue).
Initial reports indicated that Telus had denied any involvement in the issue and had said that it was a Google problem — but this position was abandoned rather quickly, and by Monday evening, the problem had been fixed.
Stop The Spoof
In order to figure out whether an email that appears to be coming from a legitimate source (like your own Gmail account!) is a spoof email, always check the sender label for tell-tale signs like “via [xx]” and also check the security label to see if the email has been encrypted.
If you want to be even more careful, open the email in Gmail, click the top right dropdown menu arrow, and select “Show original”. This will open up the message headers, and you can search for the Return-Path to see who is the actual sender of the email.
As always, don’t click on anything inside the email itself — in fact, I was quick to report these emails as spam and empty them out of my trash in Gmail. Finally, consider turning on two factor authentication (with a strong password), and monitor your account for suspicious activities.
Have any tips or tricks on how to spot a spoof email? Leave a comment below or shoot me a tweet (@carmenhchung)!
Why You Think Your Gmail Account Was Hacked was originally published in Hacker Noon on Medium, where people are continuing the conversation by highlighting and responding to this story.
Disclaimer
The views and opinions expressed in this article are solely those of the authors and do not reflect the views of Bitcoin Insider. Every investment and trading move involves risk - this is especially true for cryptocurrencies given their volatility. We strongly advise our readers to conduct their own research when making a decision.