Latest news about Bitcoin and all cryptocurrencies. Your daily crypto news habit.

Cryptocurrency is redefining the stakes of information security by pushing the boundaries of finance in the digital age. The rise in price and subsequent influx of new investors has made this of the utmost importance. A key question has arisen for many investors: “How do I know my assets are safe?” As you cannot physically touch the assets, unlike cash hidden under a mattress or gold locked in a vault, how do we know they’re secure?
The answer to this question constantly evolves as the custody infrastructure in the crypto space continues to improve and become more user friendly. Solutions are arriving, aimed at both institutional investors and individuals, which will go a long way towards making the space more secure. An inability to adequately safeguard funds would be a major Achilles heel for digital assets, hence why proper custodial solutions will be one of the most influential factors in crypto’s long-term success.
With money becoming natively digital, the stakes for information security have never been higher.
What’s the principal risk?
When it comes to cryptocurrency (and any other digital information) the number one concern is getting hacked. It’s important to understand that the blockchain itself is a highly secure distributed system that is virtually impossible to hack. The points of vulnerability lie instead in the ways users access the blockchain, which creates an attack surface for hackers.
This includes things like wallet providers, exchanges and businesses. Whether it’s the infamous Mt. Gox hack that crashed the price of Bitcoin in 2013 or the more recent $500 million hack of Coincheck, crypto exchanges have proven to be an unreliable method of storage.
Coinbase has thus far been the exception to this rule, as it has never been hacked and is generally trusted to be safe. Despite this, it has the same security concerns as anyone else. Most users understand the Coinbase model because it emulates the traditional banking system. Coinbase looks and feels like a bank, especially given its insurance and FDIC coverage. In this way, it’s easy to feel comfortable with Coinbase and assume funds are safe there; particularly when taking into account social confirmation (“everyone else does it, so it must be safe”). This is not to say that there is anything inherently wrong with that, as Coinbase is an industry leader when it comes to security. Companies like Coinbase will play a vital role in providing the type of service that institutional investors need in order to invest.
This article is meant to shed light on what it means for the individual to not have to rely on a third party to secure their own wealth. This begs the overarching question: how do you truly know what you’re doing is secure?
What it means to own a digital asset
It’s important to understand what it means to truly own a digital asset. The unique innovation of blockchain technology was the ability to prove (and enforce) the concept of digital scarcity, and to track the ownership of digital assets in a decentralized way. This means that I am now able to say with certainty that any digital assets I hold in my wallet are verifiably mine and under my control.
The blockchain works on a system based on public/private key cryptography. The actual coins themselves simply represent a balance on the blockchain’s ledger. What users really hold is a cryptographic private key, allowing them to sign transactions from a given wallet and exert ownership over a specific balance of coins on the ledger.
You can only spend the funds if you hold the private key.
Stealing someone’s private key is analogous to getting the access code to their private vault full of gold. Anyone with the code can open the vault. The same goes for private keys. This represents a golden rule in crypto: If you don’t hold the private keys, it’s not your crypto.
body[data-twttr-rendered="true"] {background-color: transparent;}.twitter-tweet {margin: auto !important;}
I've said it before and I'll say it again: if you alone don't hold the private keys to your cryptocurrency, you don't actually own it.
— @lopp
function notifyResize(height) {height = height ? height : document.documentElement.offsetHeight; var resized = false; if (window.donkey && donkey.resize) {donkey.resize(height); resized = true;}if (parent && parent._resizeIframe) {var obj = {iframe: window.frameElement, height: height}; parent._resizeIframe(obj); resized = true;}if (window.location && window.location.hash === "#amp=1" && window.parent && window.parent.postMessage) {window.parent.postMessage({sentinel: "amp", type: "embed-size", height: height}, "*");}if (window.webkit && window.webkit.messageHandlers && window.webkit.messageHandlers.resize) {window.webkit.messageHandlers.resize.postMessage(height); resized = true;}return resized;}twttr.events.bind('rendered', function (event) {notifyResize();}); twttr.events.bind('resize', function (event) {notifyResize();});if (parent && parent._resizeIframe) {var maxWidth = parseInt(window.frameElement.getAttribute("width")); if ( 500 < maxWidth) {window.frameElement.setAttribute("width", "500");}}
Take Bitcoin, for example. As it is decentralized, there is no third-party authority to resolve disputes or enforce ownership. If two people have the private key to a wallet, they have an equal claim to control those funds.
This is the nature of a decentralized system, and representative of the challenges that come with being responsible for your own security. You may ask yourself, why would I want to do that? That sounds like a lot of work and responsibility — especially when a company like Coinbase will take care of it for free.
This underlines the greater value proposition of cryptocurrency, which is to financially empower oneself to truly own one’s wealth. This concept becomes extremely salient when it comes to instances of censorship.
There’s not much point to a censorship-resistant store of value like Bitcoin if you hold it on a third-party exchange where assets can be frozen on a whim through legal proceedings or government force. Using an exchange like Coinbase is not that different from having a bank account. It’s true that many people don’t care about Bitcoin’s properties as a censorship-resistant store of value: they just want to invest. While there’s nothing inherently wrong with that, the need to ensure the safety of those assets remains.
This raises the question of what you can do to secure your private keys and ensure your funds are safe, especially considering individuals tend to be notoriously careless when it comes to keeping secrets and securing their own devices.
Crypto Security’s Early Beginnings
Unfortunately, many early adopters of cryptocurrency fell victim to imprudent security practices — resulting in a loss of funds. Early on, the only way to store bitcoins was in software held on your computer. The lack of user-friendly ways to engage with the Bitcoin blockchain and store assets safely led to billions of dollars in financial loss.
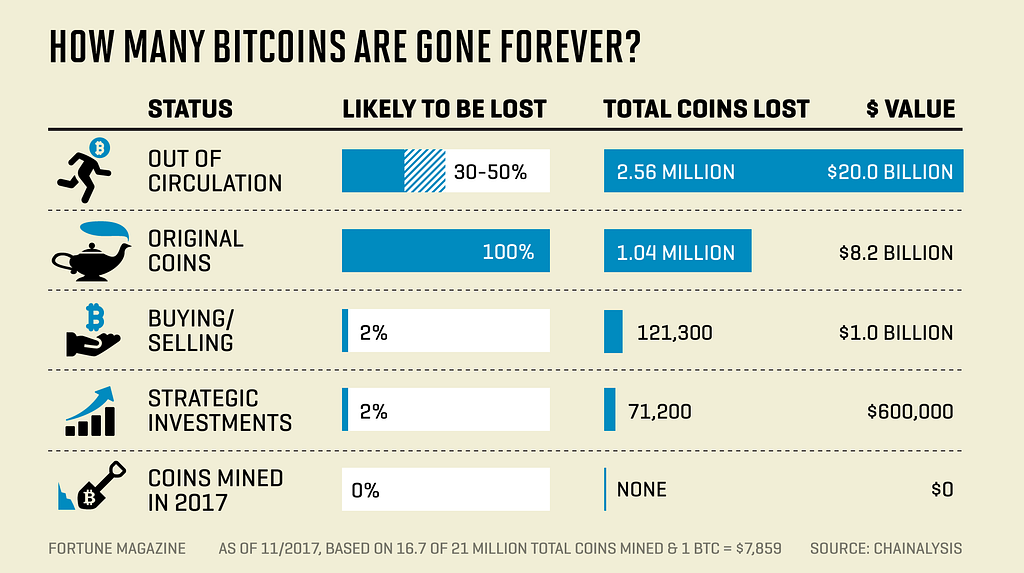 http://fortune.com/2017/11/25/lost-bitcoins/
http://fortune.com/2017/11/25/lost-bitcoins/
Many people were hacked, lost their passwords, or even threw out hard drives — some of which would now be worth tens of millions of dollars.
Even though it’s still possible to lose your crypto today, the infrastructure for securing assets has improved greatly and there are now many steps you can take to maximize your security.
Cold Storage and Basic Physical Security
Today’s gold standard for crypto security is the combination of cold storage and multi-sig. Cold storage is the practice of holding the private keys to a wallet in a manner that is not connected to the internet — thus inaccessible to hackers. Conversely, any funds that are continuously connected to the internet, such as an online wallet, are said to be in a hot wallet. Exchanges try to keep the majority of their funds in cold storage, but are required to keep a certain percentage online to facilitate the movement of funds.
Multi-sig denotes a wallet which requires more than one key (usually three different people or entities) to be able to move funds. Given multi-sig’s complexity, it is generally only used by large entities and institutional investors. Institutional custodians and exchanges employ both cold storage and multi-sig by dispersing private keys between different vaults and safety deposit boxes in different jurisdictions around the world.
Xapo, for example, is one of the world’s biggest wallet providers and custodians of Bitcoin. It stores private keys in a decommissioned military bunker in the Swiss Alps. Deep inside the bunker is a device that has never been connected to the internet (cold storage) in what’s called a “Faraday cage” (resistant to an electro-magnetic-pulse bomb) and this is still only one of the possible signers of a transaction!
Photos: The secret Swiss mountain bunker where millionaires stash their bitcoins
But short of building your own military-grade bunker deep in the Swiss Alps, what can you do?
Personal Security
Hardware wallets
Hardware wallets are the de facto uniform recommendation from security experts when it comes to owning cryptocurrency. These are devices that aim to lower the barrier for employing cold storage to a more user-friendly level. These wallets are physical devices that store users’ private keys offline, allowing them to engage with an online wallet while remaining protected against malware. This is possible because the device does not actually reveal the private keys to the computer when plugged in.
The two best-regarded hardware wallets in the space are:
- Ledger Nano S - Cryptocurrency hardware wallet
- TREZOR Bitcoin Wallet | The original and most secure hardware wallet.
The way these devices work is by setting up a wallet where your private keys are stored offline. The keys are generated upon set-up in the form of a 24-word mnemonic phrase, which needs to be written down and kept somewhere safely offline in case you lose your device or need to restore your wallet. (General best practice is to put this piece of paper in a safety deposit box — and definitely not on a computer.)
The device itself is secured by a 4- to 8-digit PIN code which will automatically erase the device after three failed access attempts to prevent against physical theft. In this case, your wallet can be restored on the same device or on a new device by entering your private key (the 24-word mnemonic) and restoring access to your funds.
The benefits of this type of device cannot be understated. Hardware wallets protect against remote hackers stealing private keys through malware, use a trusted on-device display allowing you to verify any potentially manipulated transaction information, and have buttons that allow you to physically sign a digital transaction.
It’s important to remember the coins themselves are not on the actual device: they exist merely as a balance on the blockchain.
Hardware wallets enable you to secure your private key and to physically sign transactions offline: funds can never be moved from your wallet without a physical confirmation on the device. Unless someone physically steals your device, knows your PIN or steals the backup seed to your private key, your funds are protected.
Even if you don’t get a hardware wallet, general best practices for information security are especially paramount for cryptocurrency:
- Use two-factor authentication (2FA) on all accounts: do NOT use SMS as your phone number can be ported to another device. Use Google Authenticator or Authy instead.
- Store sensitive information offline in a secure location such as a safety deposit box.
- Use a password manager or different passwords for different sites.
- Make sure your email accounts are secure (especially linked “forgot my password” back up accounts) as they are often the first line of defense.
Your greatest vulnerability may be you.
In the end, no matter how securely you store your cryptoassets — regardless of whether you take your own measures or simply trust an exchange like Coinbase — all of this is meaningless if you succumb to social engineering.
Social engineering is the process by which you are tricked into divulging personal information allowing a hacker to steal your identity. This could be your email address, your phone number or anything else that might be used to verify your identity. From that point on a hacker can pretend to be you, reset your passwords and login to your accounts on exchanges or online wallets to steal your funds. This is a major reason why you should never use your phone as a method of two-factor authentication: it’s fairly simple for a hacker to call your cellular carrier, pretend to be you, and port your phone number over to a device under their control.
Many hackers also launch “phishing attacks”, whereby they try and get you to input your password or your private key on, for example, a fake version of a real website that has malware installed. It’s important to always check URLs to make sure you’re on the correct site and never to click the first “ad” link on Google. Easily made mistakes, like not updating your own software especially with anything that has to do with crypto (e.g. hardware wallet) are also risky. These are all things that can affect you in various aspects of your life — on a personal, as well as a financial level.
Conclusion
Given that crypto is natively digital, it will forever be enticing for hackers to steal. As long as you employ basic security best practices, you can significantly reduce the likelihood you will ever be attacked. For many, buying a hardware wallet and going through these steps may seem like too much work. But those who have an amount of money invested in cryptocurrency that they can’t afford to lose should be particularly mindful of the risks, and the steps they can take to mitigate them. The existing infrastructure and tools available to users today will only become more secure and easier to use in the coming years — further enabling us to realize the full potential of what cryptocurrency has to offer.
Disclaimer: I have no affiliation or relationship with any of the companies listed above. This is by no means an exhaustive list of the security precautions one might need to take to secure their assets and unknown vulnerabilities may exist in some of the strategies listed above.
Crypto Security: How to securely own a digital asset was originally published in Hacker Noon on Medium, where people are continuing the conversation by highlighting and responding to this story.
Disclaimer
The views and opinions expressed in this article are solely those of the authors and do not reflect the views of Bitcoin Insider. Every investment and trading move involves risk - this is especially true for cryptocurrencies given their volatility. We strongly advise our readers to conduct their own research when making a decision.
