Latest news about Bitcoin and all cryptocurrencies. Your daily crypto news habit.
An Overview Of Hashgraph
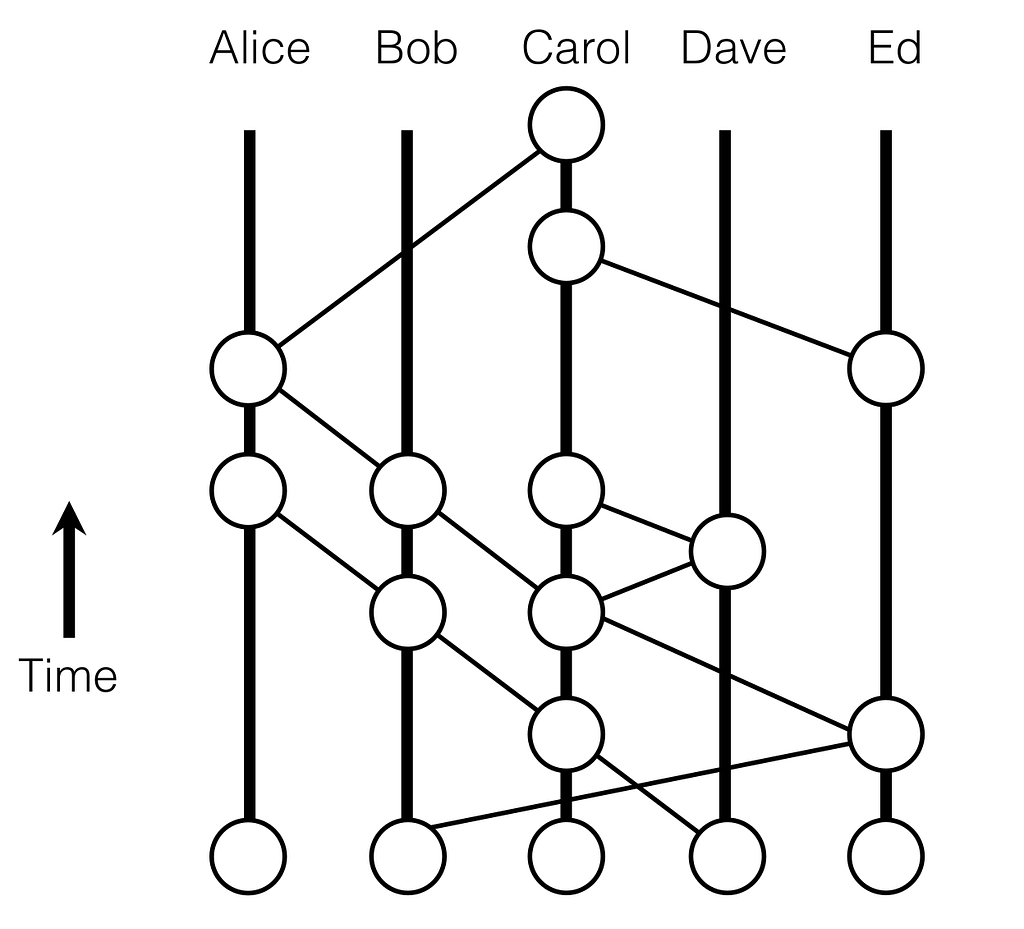 Simple Overview of the Hashgraph Protocol
Simple Overview of the Hashgraph Protocol
A distributed ledger technology (DLT) is a system where we share information and we don’t trust each other individually, but we trust the group as a whole. DLTs allow us to come up with a consensus on the order of transactions and timestamps.
Introducing Hashgraph
Hashgraph was developed by Swirlds. The cofounder and CTO of Swirlds is Leemon Baird, who obtained his bachelor’s degree at the U.S. Air Force Academy and obtained a PhD in computer science at Carnegie Mellon University.
Hashgraph is a DLT. However, hashgraph is not a blockchain in the sense that it’s not built on a chain of blocks. Hashgraph would be best characterized as a DAG — Directed Acyclic Graph.
Other DLT solutions might be secure, but they’re not particularly fast or fair. The following use-cases require fairness and speed:
- Matching buyers and sellers on a stock market
- Dark Pools
- Online Video Games
- Auctions
- Instances where it matters who filed first
- Patents
- Domain Names
Hashgraph fixes many of the failings that previous DLTs have faced: Hashgraph is incredibly fast, secure, and fair. Let’s examine each of these points piecemeal.
Hashgraph has a incredibly high throughput compared to other DLTs. It is able to achieve hundreds of thousands of transactions per second, even with only one shard. Furthermore, hashgraph has small latency — it takes only a few seconds for the transaction to be sent out.
Hashgraph achieves this speed through what’s called the “gossip protocol”
The consensus algorithm of hashgraph is asynchronous byzantine fault tolerant (asynchronous BFT). What this means is that if there are any two given transactions in a network, we as a community can come to an agreement as to what order those transactions came in. It also assumes that no more than ⅓ of people in the system are attempting to corrupt the system.
Asynchronous BFT is the strongest form of byzantine fault tolerance. With it, there is a moment when you know with 100% certainty that you have consensus. It uses a mathematical proof so that you can never be wrong about when you achieved consensus. Asynchronous BFT allows for a network to survive malicious nodes, firewalls, and DDOS attacks. Asynchronous byzantine consensus algorithms are nothing new: they existed three decades ago. The problem with them, at the time, is that those algorithms were so slow you’d never use them. As stated above, hashgraph was able to solve the issue of speed through the gossip protocol.
Let’s contrast asynchronous BFT with some other consensus algorithms, such as distributed Proof of Stake where we take turns being leaders. The issue with that is the following: If the attacker can shut down one computer at a time, then they can shut down your entire network because all they need to do is shutdown the leader of the system. When a new computer becomes the leader, all that attackers need to do is to keep following the new leader and attacking them.
Hashgraph also provides fair ordering and fair timestamps. Let’s focus first on why fair ordering is important, using the stock market as an example. If I put in a bid for a share of X, and then you put in a bid for a share of X a second later, my bid should have priority over yours. But if for some reason the network were to mess up, and your bid was prioritized over mine, that would be VERY bad. Ordering of transactions for stock markets is very important: Wall Street High Frequency Trading firms spend millions to shave a few milliseconds off the time it takes to put their bids in.
Fair timestamps are important as well, because it allows you to trust that the community as a whole timestamped something, and not just one miner. Let’s say there’s a payment dispute, and somebody claims you didn’t pay them on time. But you actually paid them before the deadline. Hashgraph solves this issue, as it uses cryptographic proof you can take to court. You can go the court and say “In fact, I did send John his money before the deadline according to this timestamp. It wasn’t just the opinion of one miner, but the whole community contributing to the timestamp”.
There are several key points to mention about Hashgraph. First, Hashgraph does NOT have a cryptocurrency. Secondly, it does not have a public ledger. Instead, Hashgraph is a permissioned ledger.
You might be asking: What is the difference between a public and a permissioned ledger, anyway?
Public Ledgers and Permissioned Ledgers: What they are and why’d you use one over the other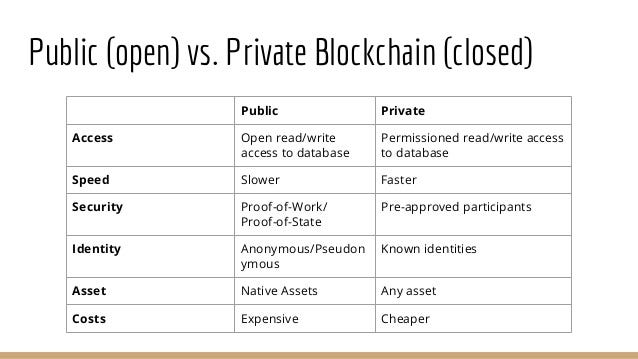
In a public ledger, anybody can be a node in the network. Take Bitcoin, for example, the biggest public ledger in terms of market cap. Anybody can use Bitcoin’s cryptographic keys, anybody can join the network, and anybody can become a miner to be rewarded in helping the network function. Anybody can see transactions on the network, and anybody can write a new block on the Bitcoin chain (as long as they follow the parameters of what constitutes a valid Bitcoin block).
A permissioned ledger, on the other hand, requires permission (hence the name) to perform certain activities on or to the network. Permissioned ledgers can limit the people and groups who are able to transact on the blockchain, and limit the people and groups who can write new blocks onto the chain. Owners of the permissioned ledger can determine who can be transaction validators on the network. In essence, a permissioned ledger requires that you have permission to run a full node.
So why would you want to use a permissioned ledger over a public ledger? In instances where you don’t want your average Joe to be able to run a full node of the ledger.
Permissioned ledgers are INCREDIBLY useful for industries where you care about keeping secrets. The financial industry is a great example of such an industry. Dark pools (also known as black pools), private forums for trading securities and derivatives, would be one portion of the financial industry where permissioned would be wanted instead of public ledgers — you would want every node of a dark pool to be permissioned and communication between nodes to be encrypted. Hashgraph’s permissioned ledgers would bring transparency and fairness to the OTC derivatives market. Swirlds also focused heavily on security for hashgraph: Swirlds has actually implemented encryption that meets the standards of encryption to protect top secret government information.
Conclusion
Shared Worlds: The Vision of Hashgraph
Leemon Baird stated in an interview that the company name “Swirlds” is a portmanteau of the phrase “shared worlds’. One problem that Leemon sees is that, although we have technology that can allow us to communicate to virtually anybody on the planet, we are feeling more socially disconnected than ever before. MIT researcher Sherry Turkle examined this phenomenon in her book Alone Together. Leemon believes the reason why this occurs is because technology allows us to be distracted when communicating with other people technologically, instead of focusing on the other person. Shared worlds would solve this issue.
The goal of Swirlds is to allow people to create shared worlds spontaneously, securely, by yourself, without needing to rely on anybody or anything else. Imagine being able to create your own fast, secure, and fair stock market in a shared world that you build.
Furthermore, Swirlds aims to allow people to do all of this for free. This would remove the need for advertisers, because if a server is free to run then there is no need to run advertisements for nonexistent server costs. This has huge implications on the advertising industry; it would remove the industry based on spying on people’s behaviors for advertisements.
DISCLOSURE: All of the above is based off of information from the Hashgraph website as well as from interviews and talks done from Leemon Baird found on YouTube. I was not paid to write this article, and am not an employee of the Hashgraph team.
You can support me by donating ETH or other ERC20 tokens to this address: 0x0BcB78d67D8d929dc03542a5aEdef257f378e513
Want to reach out to me directly? You can find my email in my Medium bio.
An Overview of Hashgraph was originally published in Hacker Noon on Medium, where people are continuing the conversation by highlighting and responding to this story.
Disclaimer
The views and opinions expressed in this article are solely those of the authors and do not reflect the views of Bitcoin Insider. Every investment and trading move involves risk - this is especially true for cryptocurrencies given their volatility. We strongly advise our readers to conduct their own research when making a decision.


