Latest news about Bitcoin and all cryptocurrencies. Your daily crypto news habit.
Reviewing how the Euler exploit looked from IntoTheBlock’s DeFi analytics and a reflection on risk in the DeFi ecosystem.

On March 13, 2023, right before 9AM UTC, an attack began on the Euler protocol that took advantage of an exploit in their code to steal approximately $197M worth of stETH, wstETH, WBTC, USDC, DAI, and WETH. Euler has published a thread detailing the incident, showing that even with multiple audits and reviews of the code, there is always a non-trivial chance that a vulnerability can be found.
While this exploit was a technical attack on the protocol, the attack can be seen through IntoTheBlock’s (ITB) economic risk indicators in the Risk Radar Dashboard for the Euler Protocol. Below we will dive into some of the indicators that show the attack in process and reflect on some different ways the DeFi ecosystem as a whole can work to mitigate risks and losses.
Brief Summary of the Exploit
As the attack has been explained in detail already many times such as that by Omniscia and Igor Igamberdiev, we will briefly go over the key points of how the attack took place.
There were multiple attacks from the same hacker that took place over the course of about 20 minutes (8:50 AM to 9:08 AM). Each attack targeted a specific asset market on Euler and the hacker used unique contract addresses for each market. This is seen through IntotheBlock’s liquidation history indicator where each liquidation in the highlighted boxes has a separate borrower and liquidator address.
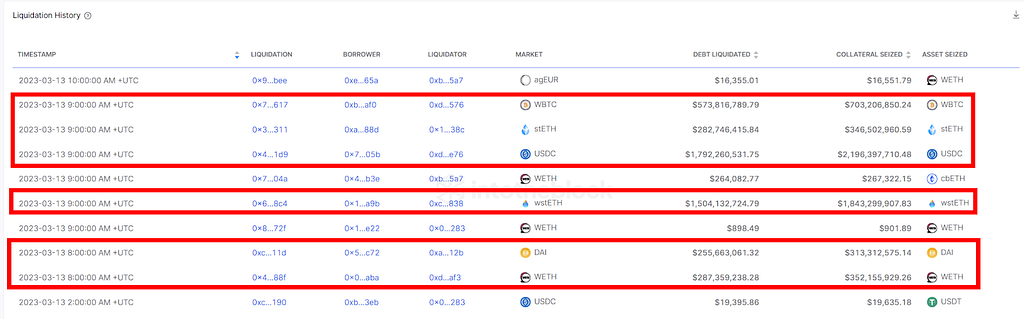
Source: ITB Euler Risk Radar
Each attack followed the same general process:
- Acquire an amount of the targeted asset through a flash-loan from another protocol (Aave and Balancer in this case)
- Deposit about 2/3rds of the acquired amount into Euler to mint ETokens (token representing a lending position in the market)
- Leverage the position about 10x to mint more ETokens and newly minted DTokens (representing a debt position in the market)
- Use the remaining ~1/3 of the flash-loan amount to repay a portion of the leveraged position to reduce the DToken position
- Leverage again to mint even more ETokens and Dtokens
- Finally, donate a portion of the ETokens to the reserve (burning these ETokens)
This sequence puts the hacker’s position below a health factor of 1, which opens the position for liquidation. Due to a portion of the ETokens being burned through the donate process, there is an imbalance in the total amount of ETokens and DTokens in the position. The liquidator contract processes the liquidation based on the manipulated difference between the ETokens and DTokens repaying the hacker for the liquidation at a rate higher than it should have been.
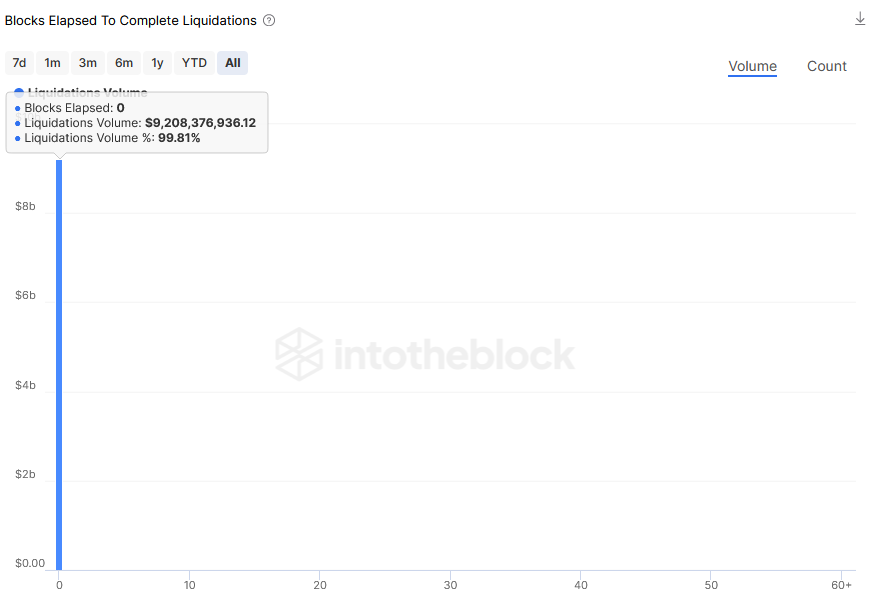
Source: ITB Euler Risk Radar
As seen in the chart above, each attack was an atomic transaction where everything occurred in the same block. This means that countermeasures on any of the individual attacks would have been difficult, with one of the only potential solutions being a MEV bot front-running the hackers liquidations process. Mitigation could have potentially been possible after the first attack since several blocks elapsed before the following attacks began. This could have been possible by some sort of “circuit-breaker” style function that pauses markets after abnormal activity occurs in the protocol, such as a liquidation that is near to the size of the entire tvl of the protocol the block before.
The Exploit Through Charts
Initial red-flags that a potential exploit is occurring can be seen through the rapidly increasing TVL and recursive lending supply share in the Euler protocol. Over the course of an hour, we can see a 22x increase in supply volume in the protocol.
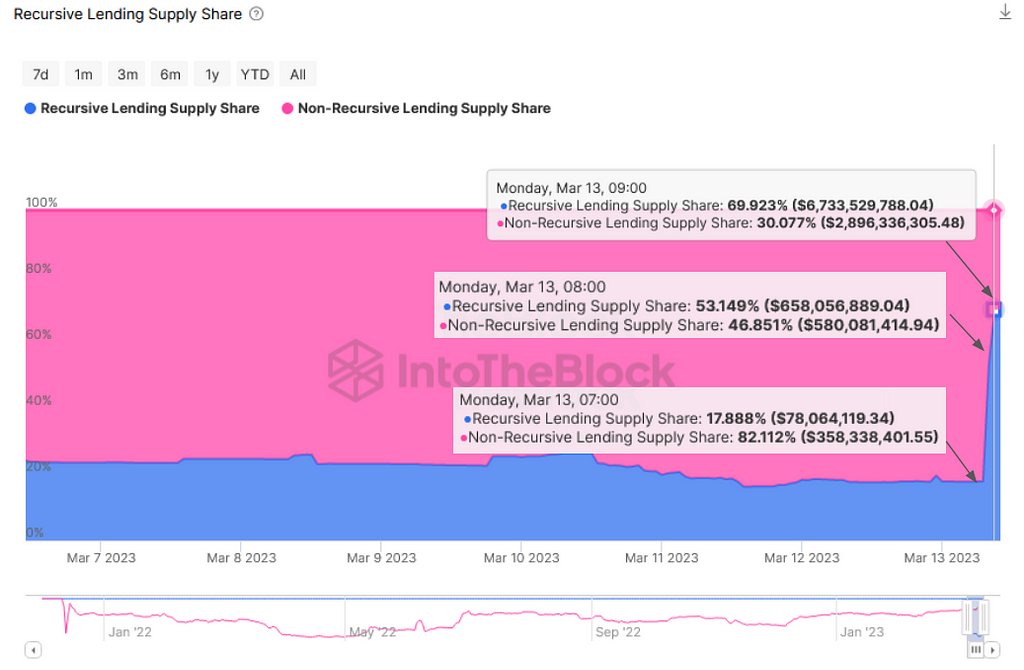
Source: ITB Euler Risk Radar
The rapid increase in supply occurs simultaneously with the spike in Health Factors below or near the liquidation point as seen below.
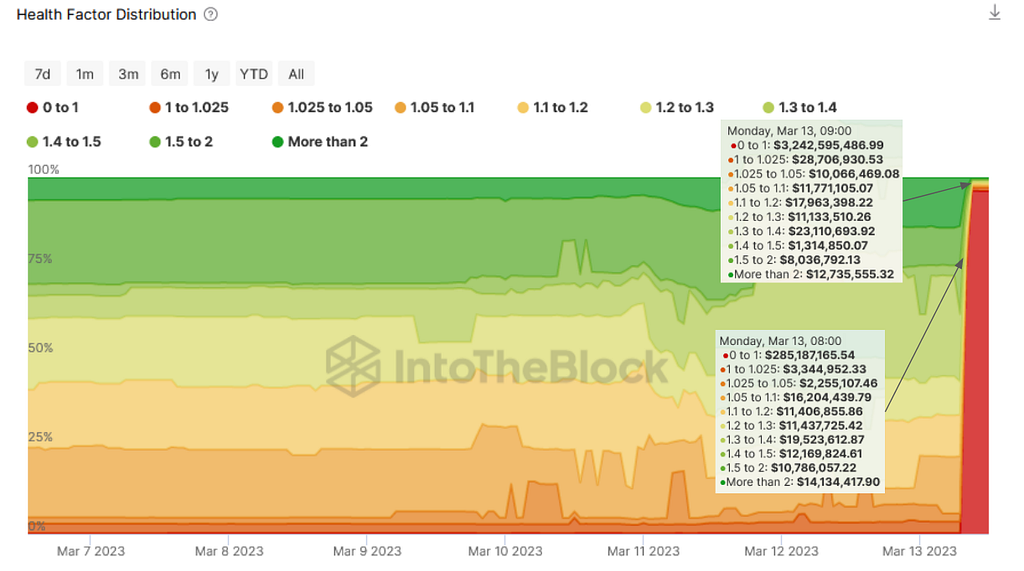
Source: ITB Euler Risk Radar
In both of these charts we can see that enough time had passed that some individuals had begun to take notice that an attack was happening. However, with many of the markets already exhausted of borrowing capacity, users who had supplied to these exploited pools were not able to remove their liquidity. This caused a cascading effect where the users of exploited pools began to borrow other collaterals to try and recover some of the stuck assets. As the USDT pool was already at max capacity with users performing a long USDC strategy due to the depegging event that began the previous week, the only pool with a large capacity still available to borrow assets from was the cbETH pool.
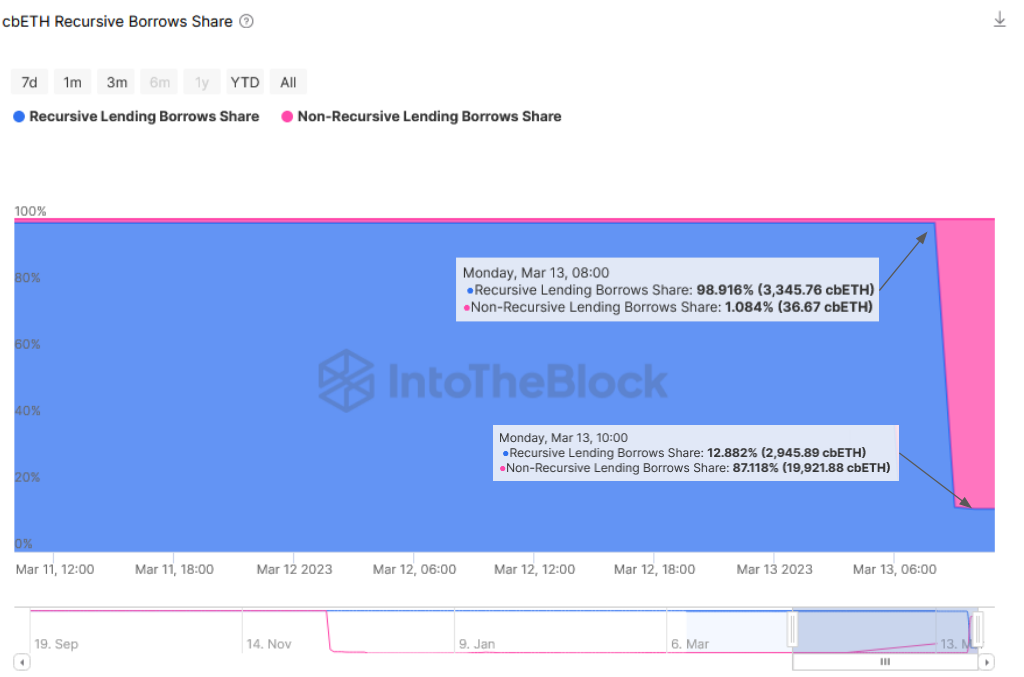
Source: ITB Euler Risk Radar
The exodus to this pool can be easily seen through the recursive borrowing chart above. There had been initially little borrowing on the cbETH pool, with ~99% of the borrowers doing recursive lending to farm EUL token rewards. However, after the hack, we see a sharp drop in the ratio of recursive borrowing and a large inflow of non-recursive borrowers seeking to pull some amount of value out of the protocol.
Risk in DeFi
Economic and technical risks are still widely prevalent in DeFi. This is unfortunately highlighted by the Euler protocol, which stood out as a protocol for risk management with multiple audits, bounties, and analytics to track the protocol. The best that the ecosystem can do is to continue learning and supporting each other through improvements in practices, standards, and innovations to mitigate known and unknown risks and to have a secondary plan when the worst still happens.
Risk Analytics
There is still a lot to be done in the space of developing risk analytics for individual protocols and the ecosystem as a whole. IntoTheBlock has been developing risk metrics for several years now for our clients to help with their risk management and strategies. However, we believe that it is important for the larger DeFi community to have access to high-quality risk indicators that we have been using internally for years. This is why we have begun to partner with multiple protocols to develop risk dashboards in our Risk Radar Platform that are publicly available for anyone to use. With more and more protocols building risk indicator dashboards, there is a larger potential for multi-protocol risk analysis to be done which can help prevent certain economic attacks on specifically lending and collateralized debt position (CDP) style protocols. Increased risk analytics for each protocol that are publicly available will benefit the protocol itself, but also have a positive spillover effect on the entire ecosystem as it makes it easier to track risks and money movement across protocols and chains.
Insurance as a Standard
Another space that needs more development are DeFi insurance markets. This has long been a topic of discussion within IntoTheBlock and is summarized here by our CEO. Insurance markets are vastly underdeveloped in DeFi compared to other financial products such as lending and exchanges but are a critical piece of infrastructure in a financial system. Fortunately, there are protocols that are solely focused on insurance products and other protocols that incorporate internal insurance designs into their protocol, but a general push for greater innovation and native products is needed. For now, there are some possibilities that could improve loss recoveries from hacks and exploits that could work in the current system.
Streaming revenue sharing to insurance fund at protocol level
A protocol could incentivize an insurance fund internally or with an outside insurance fund by creating a revenue sharing mechanism. Individuals who stake assets in the fund would receive a portion of the fees generated by the protocol. If an exploit occurs, the funds would be used to compensate the users of the protocol.
Redirected token rewards to safety module at boosted rate
This is an adaptation of Aave’s safety module, but the idea would be similar. A safety module is created to compensate users for exploits or potentially bad debt. However with this system, the idea would be that users of the protocol are receiving incentive rewards for using the protocol, but there is an option to divert your rewards to the safety module. If a user chooses to divert their rewards to the safety module, they receive a boosted amount of rewards. If the protocol is exposed to a loss, these individuals are eligible for higher compensation.
Conclusion
At IntoTheBlock, we are saddened by the exploits that occur far too often in DeFi. The Euler exploit was especially saddening as we have worked closely with the Euler team to build their Risk Radar dashboard. While we hope the best for the Euler team and community on their road to recovery, the best step forward for the rest of the DeFi ecosystem is to learn from the exploit and support each other. At IntoTheBlock, we believe that our risk indicators can be a good step in the right direction and we are open to partnering with any interested protocols to develop risk dashboards to be available for the entire DeFi community.
Euler Exploit: IntoTheBlock’s Risk Radar Perspective was originally published in IntoTheBlock on Medium, where people are continuing the conversation by highlighting and responding to this story.
Disclaimer
The views and opinions expressed in this article are solely those of the authors and do not reflect the views of Bitcoin Insider. Every investment and trading move involves risk - this is especially true for cryptocurrencies given their volatility. We strongly advise our readers to conduct their own research when making a decision.