Latest news about Bitcoin and all cryptocurrencies. Your daily crypto news habit.

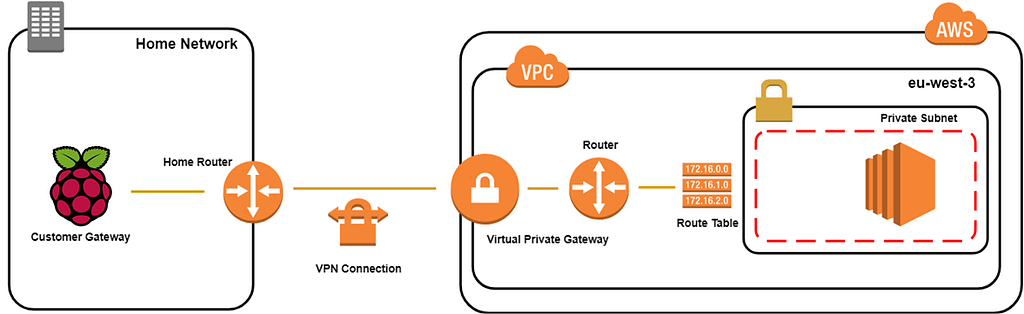
In my previous article, I showed you how to use a VPN Software Solution like OpenVPN to create a secure tunnel to your AWS private resources. In this post, I will walk you through step by step on how to setup a secure bridge to your remote AWS VPC subnets from your home network with a Raspberry PI as a Customer Gateway.
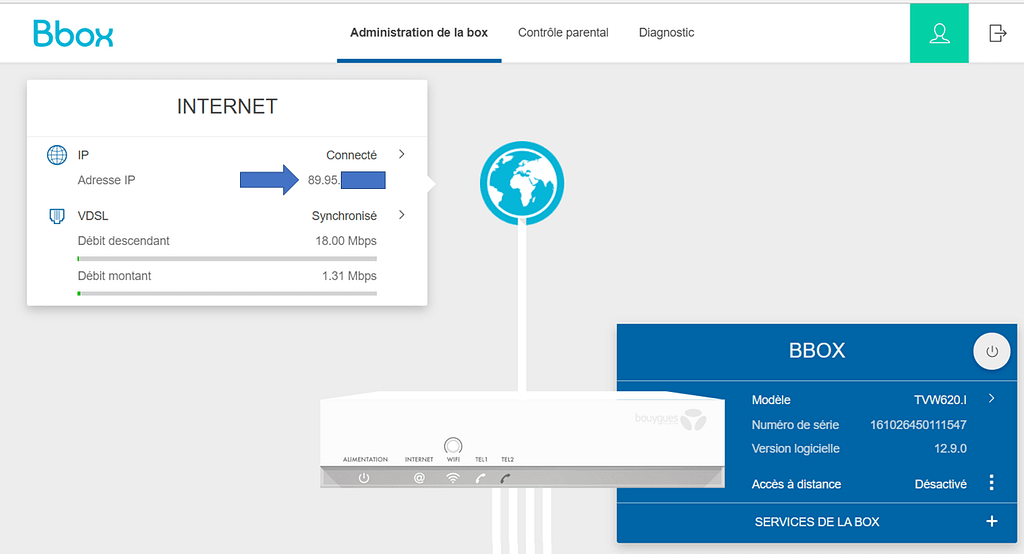
To get started, find your Home Router public-facing IP address:
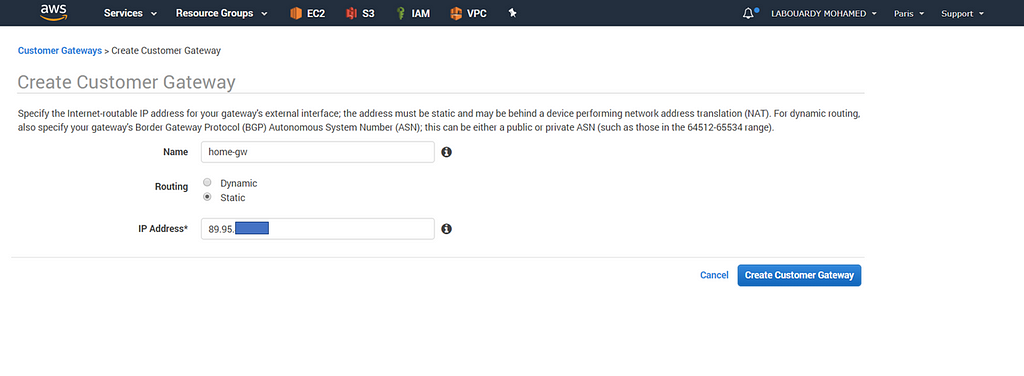
Next, sign in to AWS Management Console, navigate to VPC Dashboard and create a new VPN Customer Gateway:
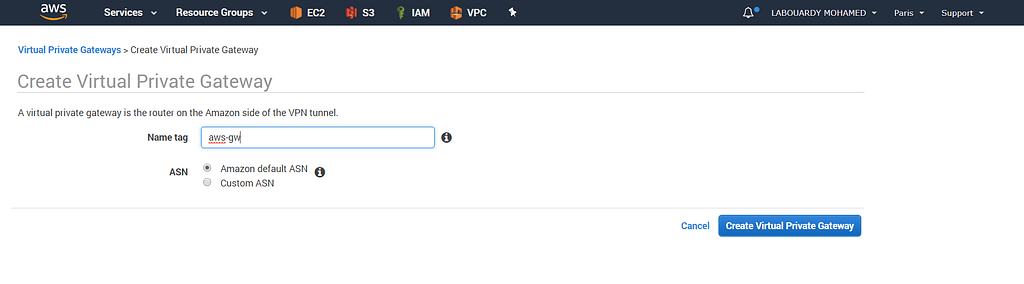
Next, create a Virtual Private Gateway:
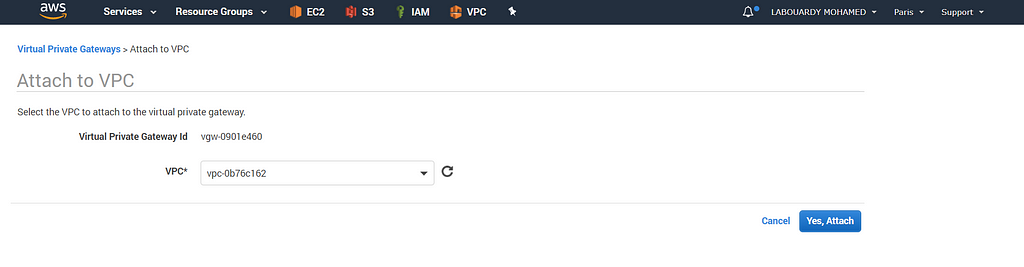
And attach it to the target VPC:
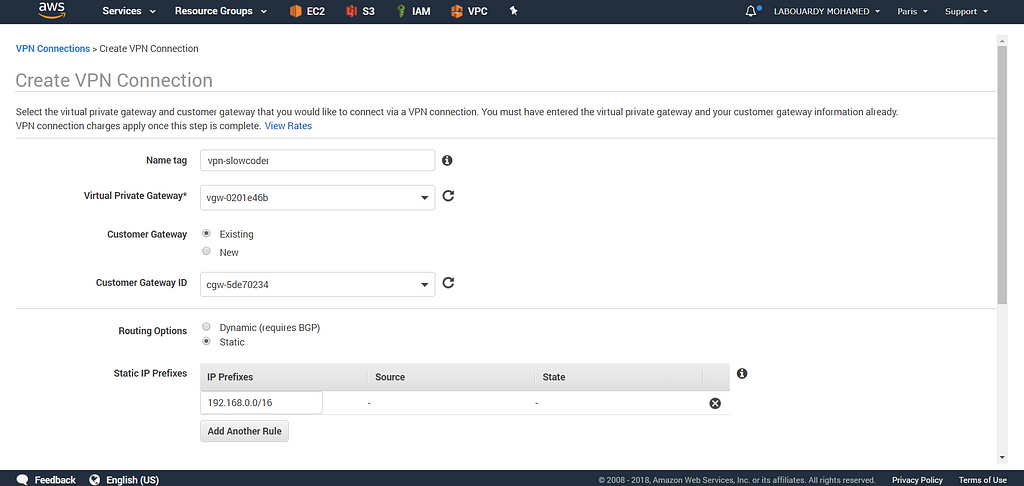
Then, create a VPN Connection with the Customer Gateway and the Virtual Private Gateway:
Note: Make sure to add your Home CIDR subnet to the Static IP Prefixes section.
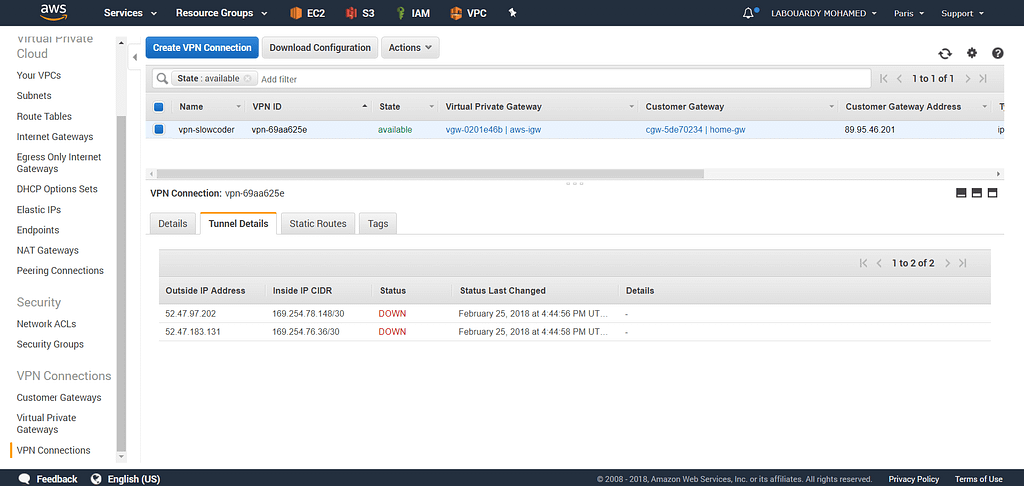
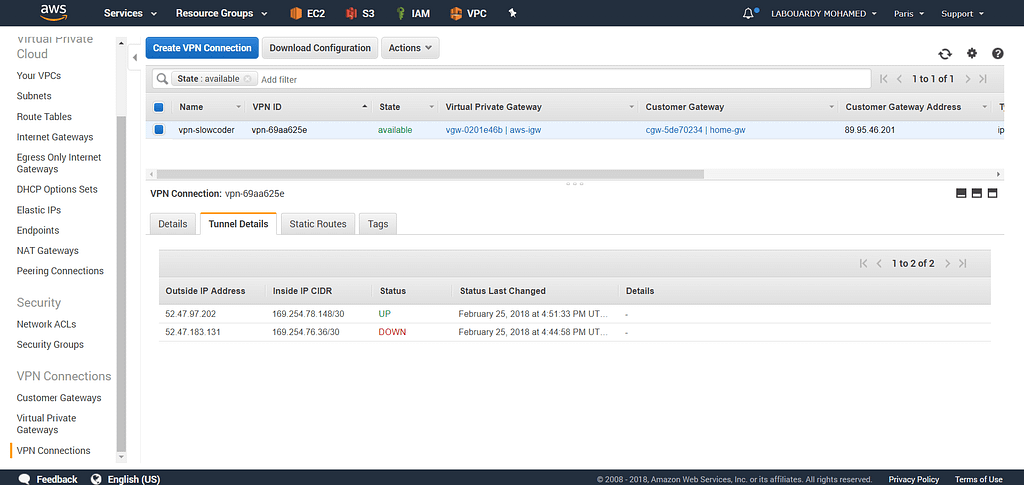
Once the VPN Connection is created, click on “Tunnel Details” tab, you should see two tunnels for redundancy:
It may take a few minutes to create the VPN connection. When it’s ready, select the connection and choose “Download Configuration“, and open the configuration file and write down your Pre-shared-key and Tunnel IP:
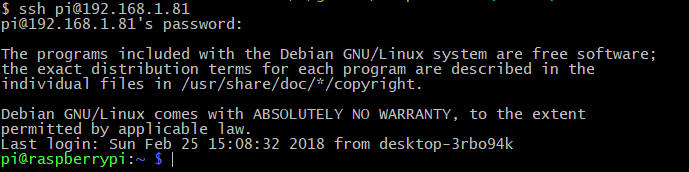
I used a Raspberry PI 3 (Quand Core CPU 1.2 GHz, 1 GB RAM) with Raspbian, with SSH server enabled (default username & password: pi/raspberry), you can login and start manipulating the PI:
IPsec kernel support must be installed. Therefore, you must install openswan on your PI:
sudo apt-get install -y openswan lsof
Update the /etc/ipsec.conf file as below:
Create a new IPsec Connection in /etc/ipsec.d/home-to-aws.conf :
- left: Your Raspberry PI private IP.
- leftid: Your Home Router public-facing IP.
- leftsubnet: CIDR of your Home Subnet.
- right: Virtual Private Gateway Tunnel IP.
- rightsubnet: CIDR of your VPC.
Add the tunnel pre-shared key to /var/lib/openswan/ipsec.secrets.inc:
89.95.X.Y 52.47.119.151 : PSK “irCAIDE1NFxyOiE4w49ijHfPMjTW9rL6”
To enable the IPv4 forwarding, edit /etc/sysctl.conf, and ensure the following lines are uncommented:
Run sysctl -p to reload it. Then, restart IPsec service:
service ipsec restart
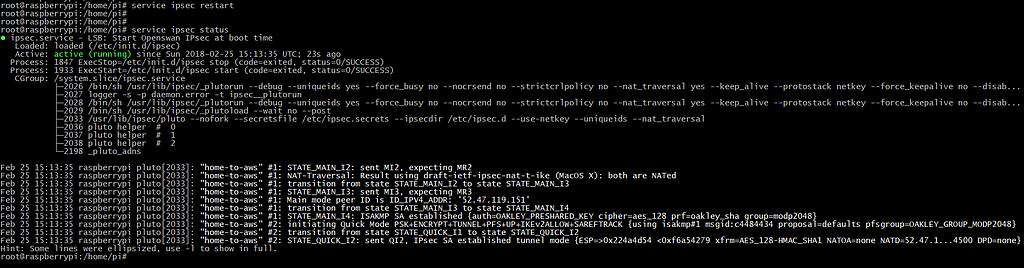
Verify if the service is running correctly:
If you go back to your AWS Dashboard, you should see the 1st tunnel status changed to UP:
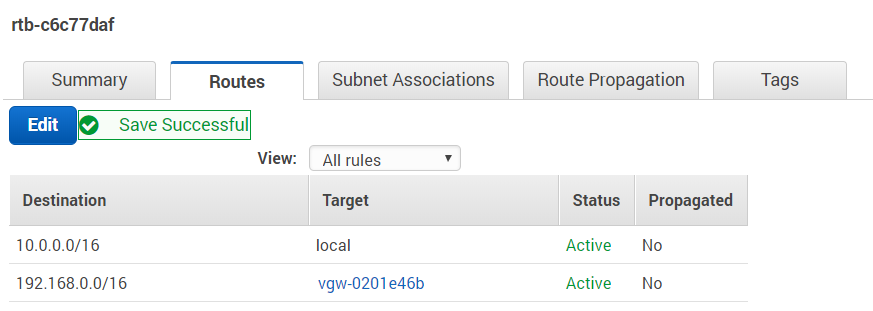
Add a new route entry that forwards traffic to your home subnet through the VPN Gateway:
Note: Follow the same steps above to setup the 2nd tunnel for resiliency & high availablity of VPN connectivity.
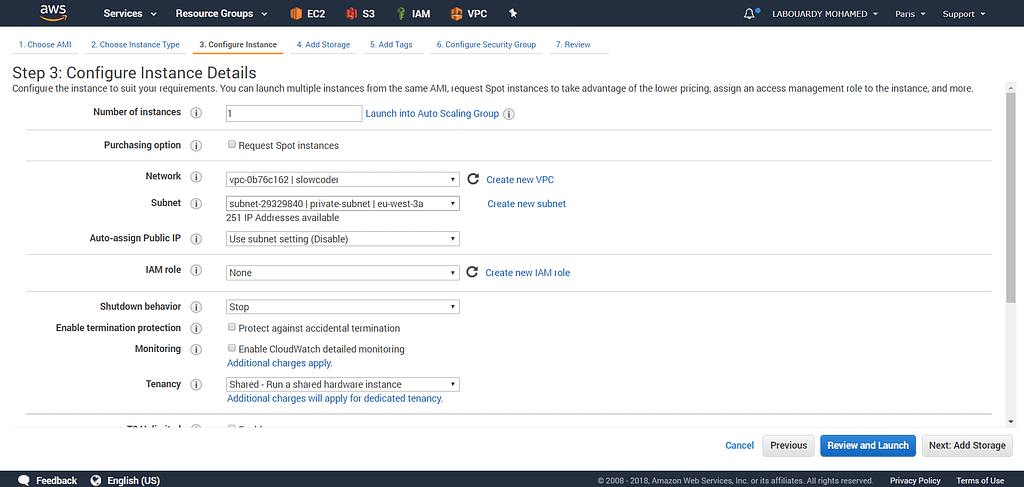
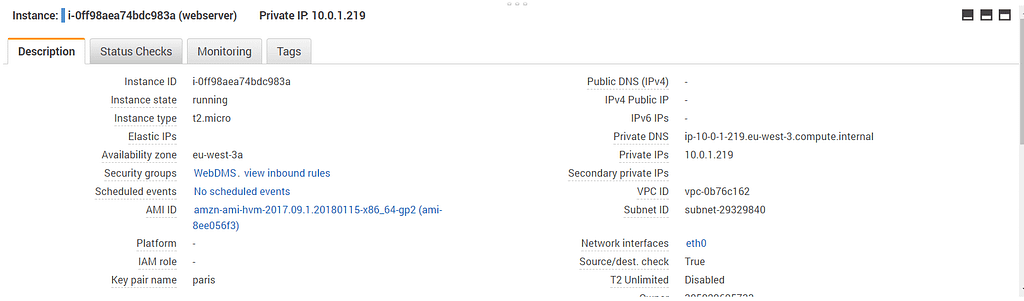
Launch an EC2 instance in the private subnet to verify the VPN connection:
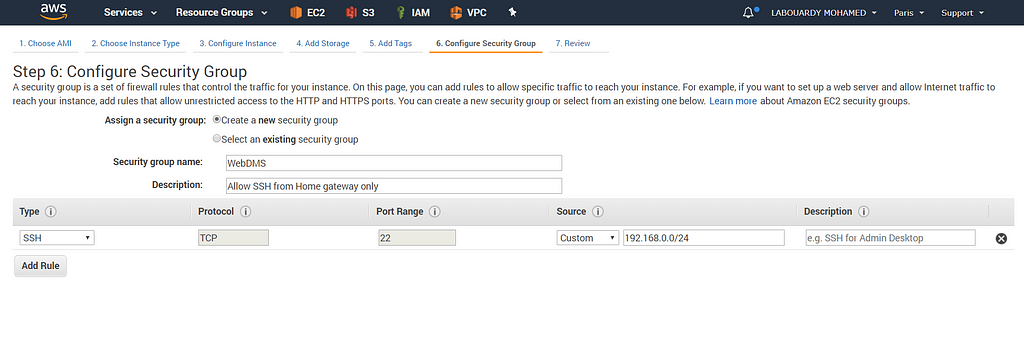
Allow SSH only from your Home Gateway CIDR:
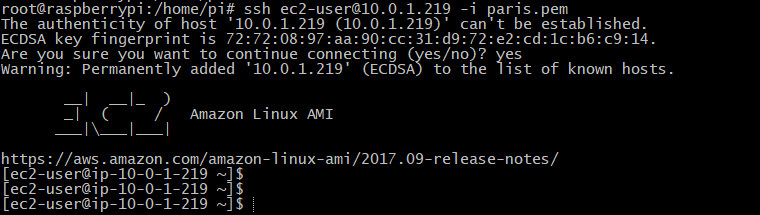
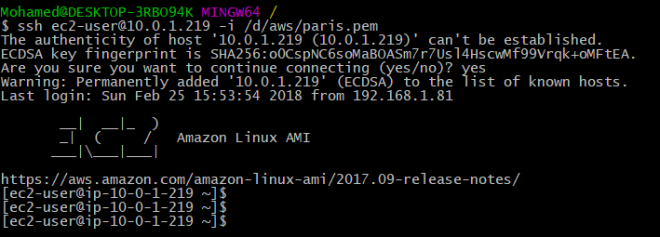
Once the instance is created, connect via SSH using the server private ip address:
Congratulations ! you can now connect securely to your private EC2 instances.
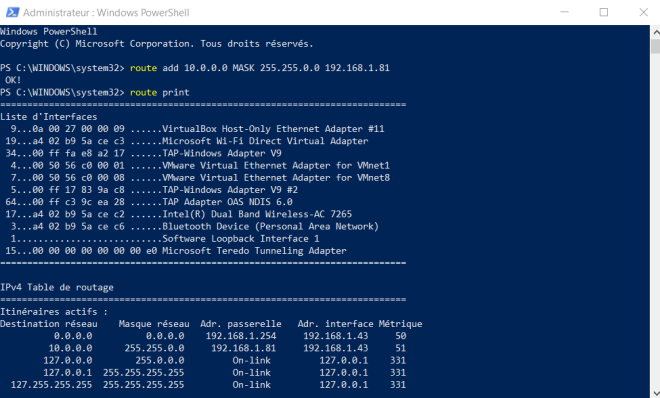
To take it further and connect from other machines in the same Home Network, add a static route as described below:
1 — Windows
route add 10.0.0.0 MASK 255.255.0.0 192.168.1.81
2 — Linux
sudo up route add -net 10.0.0.0 netmask 255.255.0.0 gw 192.168.31.232
3 — Mac OS X
sudo route -n add 10.0.0.0/16 192.168.31.232
Test it out:
Setup Raspberry PI 3 as AWS VPN Customer Gateway was originally published in Hacker Noon on Medium, where people are continuing the conversation by highlighting and responding to this story.
Disclaimer
The views and opinions expressed in this article are solely those of the authors and do not reflect the views of Bitcoin Insider. Every investment and trading move involves risk - this is especially true for cryptocurrencies given their volatility. We strongly advise our readers to conduct their own research when making a decision.