Latest news about Bitcoin and all cryptocurrencies. Your daily crypto news habit.
 HP Color Laserjet MFP M477fdw, one of the most secure print devices ever. Image is courtesy of HP.
HP Color Laserjet MFP M477fdw, one of the most secure print devices ever. Image is courtesy of HP.
Imagine your office network. Cyber attackers are trying to get into it. They know that your company has lucrative proprietary data. They know that your company will be tempted to pay expensive cryptocurrency ransoms if they can cripple your computers with ransomware. Even if you keep good backups, it might not be practical to restore from them. Maybe the cyber attackers want money? Maybe they just want to vandalize your web servers “for the lulz?” Maybe an individual attacker won’t target your company, but profitable cyber attack botnets and services can be hired so easily from the Dark Web these days. Bots will travel all over the internet looking for vulnerable targets to hit. Your office network may be tagged “it.”
Can you imagine what your attack vector will be? It could quite possibly be a client PC. An employee could open a malicious email attachment that isn’t detected by your antivirus software. Maybe a cyber attack will slip through a firewall. Unfortunately, that happens sometimes. Maybe your web application will get SQL injected. Maybe an LDAP vulnerability will be exploited, and there’ll be a privilege escalation attack to your Active Directory.
Did you think about that big network printer that’s sitting in the corner of the room? Print jobs are sent to it from your client PCs constantly. It’s also connected to your corporate WLAN. It needs to be connected to your corporate WLAN. Well your WLAN connects to the internet, doesn’t it? It’s probably connected to your private internal network too. So it’s a cyber attack vector from the public internet to your private network. Hmmmm…
Hacking unsecured printers is easy. Unfortunately, according to a Spiceworks survey only 16% of IT industry respondents think printers are at high risk of a security breach! 43% of surveyed companies ignore printers in their endpoint security approach. Well, what adminstrators don’t know will hurt them. Corporations invest in securing their computing devices. Why not printers?
Print security has three major facets. It requires securely designed and deployed hardware, software, and networking. That means choosing to secure your office’s network requires starting with print devices which are designed with cybersecurity in mind from the ground up. One print device vendor knows you must secure the device, secure the data, secure the document. I got to see firsthand, that vendor is HP.
HP has the world’s most secure print devices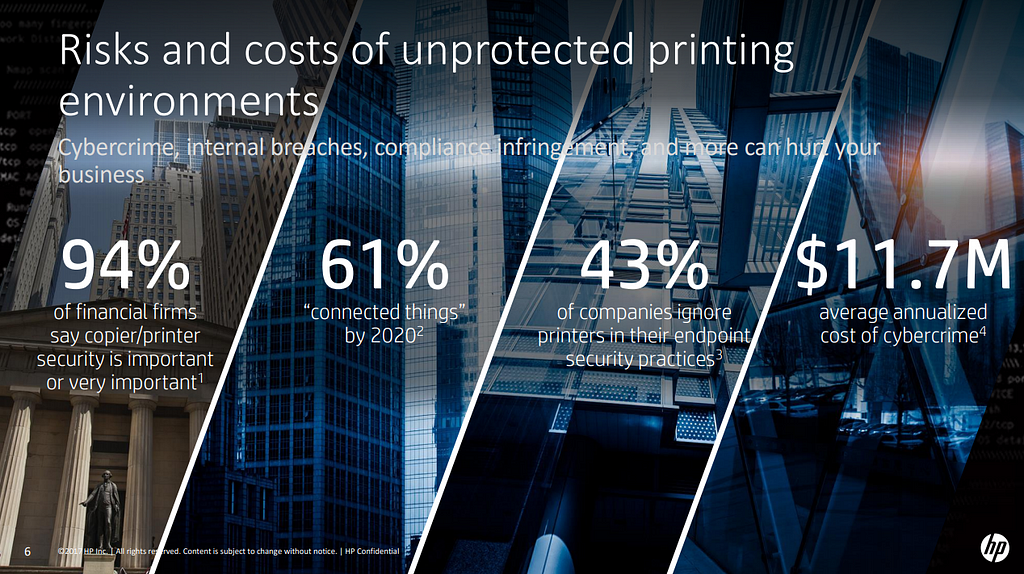 Image is courtesy of HP.
Image is courtesy of HP.
I got an exclusive look at HP’s print security initiatives in early February. HP indeed has the world’s most secure print devices! But don’t take my word for it.
Check out what it says in IDC MarketScape: Worldwide Security Solutions and Services Hardcopy 2017 Vendor Assessment:
“HP Inc. is leading the charge among all hardcopy vendors around raising awareness and visibility for print and document security concerns and promotes itself as having the most secure printers in the world. HP Inc.’s approach to security takes the entire print and document infrastructure into account, beginning with locking down the device and extending into all aspects of device usage and content protection.HP Inc.’s expansive suite of print and document security solutions is based on a mix of owned technology and partner-delivered capabilities that deliver security in four primary areas: HP JetAdvantage Security Manager, HP Inc.’s pull printing solutions, HP Inc.’s data protection, and HP Inc.’s security services. HP JetAdvantage Security Manager enables customers to develop a comprehensive print security policy, assess and remediate devices against that policy, and provide audit and reporting measures based on predefined guidelines.HP Inc. offers a broad range of pull printing solutions designed to meet the needs of specific customer environments as well as data protection solutions to help organizations detect and prevent data loss through print devices. Leveraging its broad solutions portfolio, HP Inc. offers an extensive set of security-based services including Security Audit Advisory Services, Implementation Service, and Advisory Retainer Service.HP Inc. offers its security services as standalone programs, but its entire portfolio of security solutions and services are also available through HP Inc.’s Managed Print Services (MPS) offerings. HP Inc. has established a formidable managed print services practice that includes security as a backbone and is foundationally built on investments it has made in its ‘as a service’ global infrastructure. In fact, HP Inc. markets its MPS programs as ‘Secure MPS,’ part of which is simply marketing, but it also points to core capabilities that have become standard security components in HP Inc.’s MPS arsenal.”
According to IDC MarketScape’s 2017 Vendor Assessment, HP leads the industry in print security.
You should also consider Quocirca’s research findings in their 2016 Managed Print Services Landscape:
“HP’s security offerings are a key differentiator in the MPS market which led itto launch a security-led MPS programme in 2016: HP Secure MPS. The major components of HP Secure MPS include HP’s enterprise printer portfolio, security software solutions and security services.The unique features of HP enterprise printers include run time intrusion detection, which makes HP the only printer manufacturer to offer integration of printer event data with major security monitoring and incident detection tools such as HPE ArcSight or Splunk.Solutions are a major strength for HP through its expanding JetAdvantage portfolio. It estimates that over 75% of its enterprise-direct engagements are software enabled, including solutions such as document capture, security, mobility, job accounting, forms automation and production printing.HP continues to deepen its industry focus, through market development, industry segment marketing and sales enablement capabilities. It has a range of solutions targeted at industries such as financial services, healthcare, manufacturing, communications/media/entertainment and public sector and a broad set of vertical solutions through the HP Enterprise Content Management platform.”
Only HP offers a combination of security features that can monitor to detect and automatically stop an attack, then self-validate software integrity in a reboot.
Inside HP’s proprietary print security features Image is courtesy of HP.
Image is courtesy of HP.
Here’s a list of printer security features that are exclusive or nearly exclusive to HP enterprise print devices:
- Run-time intrusion detection with self-healing
- “Instant On” security
- Secure boot with self-healing
- Only HP and Lexmark have device level SIEM integration
- Only HP, Lexmark, and Kyocera have Turn On/Off Remote Firmware Upgrade
- Only HP and Xerox have full print device security administrator notification capabilities
- Only HP and Kyocera have US NIST Checklist Inclusion
HP Sure Start is built into the BIOS. The BIOS runs its own firmware which checks the health and operation of your print device when you boot it up, the same way BIOS in PCs and servers works before the operating system is launched. BIOS firmware is a key target for cyber attackers, especially through malware! HP Sure Start is designed to protect your printer BIOS from being hacked. With HP Sure Start, if tampered BIOS firmware is detected, the device restarts using a safe “golden copy” of its BIOS.
Your network probably runs intrusion detection devices. If it doesn’t, it really ought to! It helps to have a dedicated IDS device in your network. It’s even better to also have intrusion detection built right into your enterprise print devices. HP’s run-time intrusion detection operates constantly. It detects anomalies during complex firmware and memory operations, automatically stops intrusions, and reboots.
A lot of the most destructive malware out there “calls home” to cyber attacking command and control servers. Malicious data doesn’t only enter private networks, it exits private networks too! That’s where HP Connection Inspector comes in. HP Connection Inspector evalutes connections coming into and exiting your print devices. If anything looks suspicious, HP Connection Inspector stops it in its tracks. That makes it extra challenging for cyber attackers to acquite access to your network’s sensitive data!
HP Security Advisory Services Image is courtesy of HP.
Image is courtesy of HP.
HP’s unique enterprise print device security strategy doesn’t stop at designing more secure hardware and software. If your network has HP devices, you can request an HP Security Manager Quick Assess. HP Security Manager Quick Assess will evaluate up to twenty of your HP network printers and will send you a full, detailed report with information about how you can improve your security. Start with their web form here.
DreamWorks Animation relies on HP Secure MPS
You’ve probably heard of DreamWorks Animation. They’re known for hit films such as Shrek, How To Train Your Dragon, and Kung Fu Panda. Chances are you’ve watched at least one of their movies with your family.
They’re working on new feature film animation projects right now that’ll show in your local movie theatre in the years to come. HP print devices are integral to their work. Aspects of their intellectual property work go through HP print devices and they don’t want the general public to see them until they’re ready to promote their upcoming movies. But paparazzi and entertainment magazines and websites will pay top dollar for Hollywood leaks. Pop stars and famous rappers hate it when the public gets to hear their music before they’re ready to release it. Why haven’t you seen any unauthorized leaks from DreamWorks? HP MPS is a major factor.
Mark Tokunaga, Vice President of Service Operations at DreamWorks Animation says, “Our onsite HP MPS service delivers predictable costs and nearly flawless print-device uptime. HP MPS enables the studio’s operations team to spend less time being diverted by print management issues, so that we can focus on strategic engineering initiatives.”
Choose your enterprise print devices
So you want HP Secure MPS and their proprietary print security features in your network. Where do you start?
HP has a list of their most secure enterprise print devices which you can find here. Happy printing!
Did you know that printers are a major cyber attack vector? was originally published in Hacker Noon on Medium, where people are continuing the conversation by highlighting and responding to this story.
Disclaimer
The views and opinions expressed in this article are solely those of the authors and do not reflect the views of Bitcoin Insider. Every investment and trading move involves risk - this is especially true for cryptocurrencies given their volatility. We strongly advise our readers to conduct their own research when making a decision.